You’ve probably heard the horror stories — user data leaks, payment fraud, hacked admin panels, and platforms shut down overnight due to compliance failures. When it comes to launching a white-label Turo-style app, safety is not just a technical concern anymore — it’s a business survival issue.
In 2025, car-sharing platforms handle high-risk data: driver licenses, identity documents, payment information, vehicle location tracking, and real-time bookings. One weak security layer can expose thousands of users and put founders at serious legal and financial risk.
This is why many entrepreneurs ask a very real question:
“Is a white-label Turo app actually safe?”
In this guide, we’ll give you an honest, practical security assessment — no marketing fluff. You’ll understand the real risks, the standards your app must meet, and how security-first providers like Miracuves reduce these risks with enterprise-grade architecture.
Understanding White-Label Turo App Security Landscape
What “White-Label Turo App Security” Actually Means
When we talk about white-label Turo app security, we are not talking about a single feature or tool. Security here is a complete system that protects users, vehicles, payments, and the business itself.
A white-label Turo-style app typically includes:
- User onboarding with identity verification
- Vehicle listings with ownership data
- Real-time booking and availability logic
- In-app payments and refunds
- GPS-based location tracking
- Admin dashboards with full data access
Security means protecting every one of these layers, not just encrypting passwords.
Why People Worry About White-Label Turo Apps
Concerns usually come from three real risks:
- Fear of shared or reused codebases
- Lack of visibility into backend security
- Unclear responsibility during a breach
These concerns are valid if the provider cuts corners. A security-first provider isolates deployments, audits code regularly, and documents compliance clearly.
Current Threat Landscape for Turo-Type Platforms (2025)
Car-sharing apps face some of the highest-risk attack vectors today:
- Account takeovers using credential stuffing
- Fake driver identities and document fraud
- API abuse to scrape vehicle and user data
- Payment fraud and chargeback abuse
- Location tracking misuse
- Admin panel brute-force attacks
According to global app security reports:
- Over 43% of mo= m
- \8bility apps faced API-related vulnerabilities in the last 24 months
- 1 in 3 data breaches involved improper access control
- Financial and identity data leaks caused the highest regulatory penalties
Security Standards That Matter in 2025
Modern white-label Turo apps are expected to align with:
- Zero-trust security models
- Encrypted data at rest and in transit
- Privacy-by-design architecture
- Region-specific data residency compliance
- Continuous monitoring instead of one-time checks
Security is no longer optional — it is part of product credibility.
Key Security Risks & How to Identify Them
Understanding security risks early helps founders avoid expensive fixes, legal trouble, and trust loss later. A white-label Turo app handles sensitive data and real-world assets, which makes risk identification critical.
Data Protection & Privacy Risks
User Personal Information
A Turo-style app stores:
- Names, phone numbers, email IDs
- Government ID documents
- Driving license images
- Address and profile data
If this data is stored without proper encryption or access control, it becomes a prime target for attackers.
Payment Data Security
Even when third-party gateways are used, risks still exist:
- Insecure webhook handling
- Exposed transaction logs
- Improper token storage
- Weak refund and dispute workflows
These gaps can lead to fraud, chargebacks, and compliance violations.
Location Tracking Concerns
Real-time vehicle and user location data is highly sensitive. Common risks include:
- Over-collection of location data
- No clear retention policy
- Unauthorized internal access
- Exposure through unsecured APIs
Misuse of location data can trigger serious privacy complaints and regulatory action.
GDPR and CCPA Compliance Gaps
Many apps fail at:
- User consent management
- Data deletion requests
- Data portability requirements
- Purpose limitation enforcement
Non-compliance can result in fines, platform bans, and forced shutdowns.
Technical Vulnerabilities
Code Quality Issues
Poorly written or reused code can introduce:
- SQL injection vulnerabilities
- Broken authentication logic
- Insecure file uploads
- Hardcoded credentials
Server Security Gaps
Common backend risks include:
- Misconfigured cloud storage
- Open ports and services
- No firewall or intrusion detection
- Shared server environments
API Vulnerabilities
APIs are the backbone of a Turo-style app. Weak APIs can lead to:
- Data scraping
- Booking manipulation
- Unauthorized admin actions
- Rate-limit bypass attacks
Third-Party Integrations
Maps, payments, messaging, and analytics tools can introduce risk if:
- SDKs are outdated
- Permissions are excessive
- Data sharing is undocumented
Business-Level Security Risks
Legal Liability
Data leaks can make the platform owner legally responsible, even if the provider caused the issue.
Reputation Damage
Trust loss in a car-sharing app is hard to recover. Users associate security failures with unsafe vehicles and unreliable hosts.
Financial Losses
Security incidents often lead to:
- Regulatory fines
- Chargeback losses
- Legal fees
- Emergency rebuild costs
Regulatory Penalties
Non-compliance with data protection laws can result in platform takedowns and long-term operational restrictions.
Risk Assessment Checklist
- Is all sensitive data encrypted at rest and in transit?
- Are admin roles strictly permission-based?
- Is each app deployment isolated?
- Are APIs authenticated and rate-limited?
- Is there a clear data retention and deletion policy?
- Are security audits documented?
- Is incident response clearly defined?
If any of these answers are unclear, the app carries high security risk.
Read more : – Turo Revenue Model: How Turo Makes Money in 2025
Security Standards Your White-Label Turo App Must Meet
Essential Certifications and Compliance Standards
ISO 27001 Compliance
ISO 27001 focuses on building an Information Security Management System (ISMS). For a Turo-style app, it matters because it proves the provider has repeatable controls for:
- Risk management
- Access control policies
- Incident response
- Vendor and infrastructure security governance
SOC 2 Type II
SOC 2 Type II is a strong signal of operational security maturity because it validates controls over time (not just “on paper”). It’s especially relevant if your platform handles:
- Continuous user onboarding
- Document verification flows
- Payment processing and refunds
- Admin and support access to user data
GDPR Compliance
If you serve users in the EU/UK, GDPR is not optional. For a car-sharing app, GDPR typically impacts:
- Consent collection for tracking and marketing
- Data minimization (collect only what you truly need)
- Right to access, delete, and export user data
- Data processing agreements with vendors
CCPA / CPRA Compliance
If you serve California users, you must support:
- “Do Not Sell or Share My Personal Information” where applicable
- Consumer rights requests (access/delete)
- Transparency around third-party data sharing
PCI DSS for Payments
If your app stores, processes, or transmits card data directly, PCI DSS is mandatory. Most modern platforms reduce PCI scope by using tokenized payment gateways, but you still must secure:
- Payment flows and webhook endpoints
- Transaction logs and reconciliation data
- Refund and dispute workflows
HIPAA (If Applicable)
A typical Turo-style app doesn’t require HIPAA. It becomes relevant only if your platform handles protected health information (for example, medical transport services). If not, don’t treat HIPAA as a default requirement.
Technical Requirements
Encryption
A secure white-label Turo app should include:
- Encryption in transit (TLS/SSL across all traffic)
- Encryption at rest (databases, object storage, backups)
- Strong key management (rotation, restricted access, audit logs)
Secure Authentication
Minimum baseline in 2025:
- 2FA for admin and high-risk actions
- OAuth-based login options if needed (with safe token storage)
- Rate-limiting and bot protection for login endpoints
- Session security (short-lived tokens, refresh token hygiene)
Regular Security Audits
Audits should cover:
- Mobile app security review
- Backend and infrastructure review
- Dependency scanning and patch verification
- Access control and permission review
Penetration Testing
At least:
- Before launch
- After major releases
- After infrastructure changes
Pen tests should explicitly include API abuse scenarios (booking, payments, identity flows).
Secure API Design
Your APIs should implement:
- Strict authentication and authorization per endpoint
- Input validation and output filtering
- Rate limiting and anomaly detection
- Secure object-level authorization (prevent “IDOR” style data access issues)
Logging, Monitoring, and Alerting
Non-negotiables:
- Centralized logs with tamper resistance
- Alerts for suspicious admin actions
- Alerts for spikes in failed logins, refund abuse, booking manipulation
- Incident playbooks (what happens at 2 AM when something breaks)
Security Standards Comparison Table
| Standard / Control | What it covers | Why it matters for a white-label Turo app | Typical proof you should request |
|---|---|---|---|
| ISO 27001 | ISMS governance, security controls framework | Ensures security is systematic, not “developer dependent” | ISO certificate, scope statement, ISMS overview |
| SOC 2 Type II | Operational security controls tested over time | Proves ongoing security discipline, not a one-time checklist | SOC 2 Type II report (or summary letter) |
| GDPR | EU/UK privacy, user rights, lawful processing | Identity docs + location tracking makes privacy high-risk | DPA, privacy design notes, DSAR process |
| CCPA/CPRA | California privacy rights and disclosures | Requires transparency and user request handling | Privacy policy mapping, request workflows |
| PCI DSS | Card data security | Reduces payment fraud and compliance exposure | PCI attestation, gateway architecture showing tokenization |
| Encryption (at rest/in transit) | Data confidentiality | Prevents data exposure via interception or storage leaks | Architecture diagram, encryption policy, key management details |
| Pen testing | Real-world attack simulation | Finds API and auth weaknesses that audits miss | Pentest report, remediation evidence |
| Secure SDLC | Security in development lifecycle | Prevents repeat vulnerabilities after launch | Patch policy, dependency scanning reports, release checklist |
Read more : – Best Turo Clone Scripts in 2025: Features & Pricing Compared
Red Flags: How to Spot Unsafe White-Label Providers
Choosing the wrong provider is the fastest way to turn a promising Turo-style app into a legal and security nightmare. Many safety issues are not technical — they are behavioral and procedural warning signs.
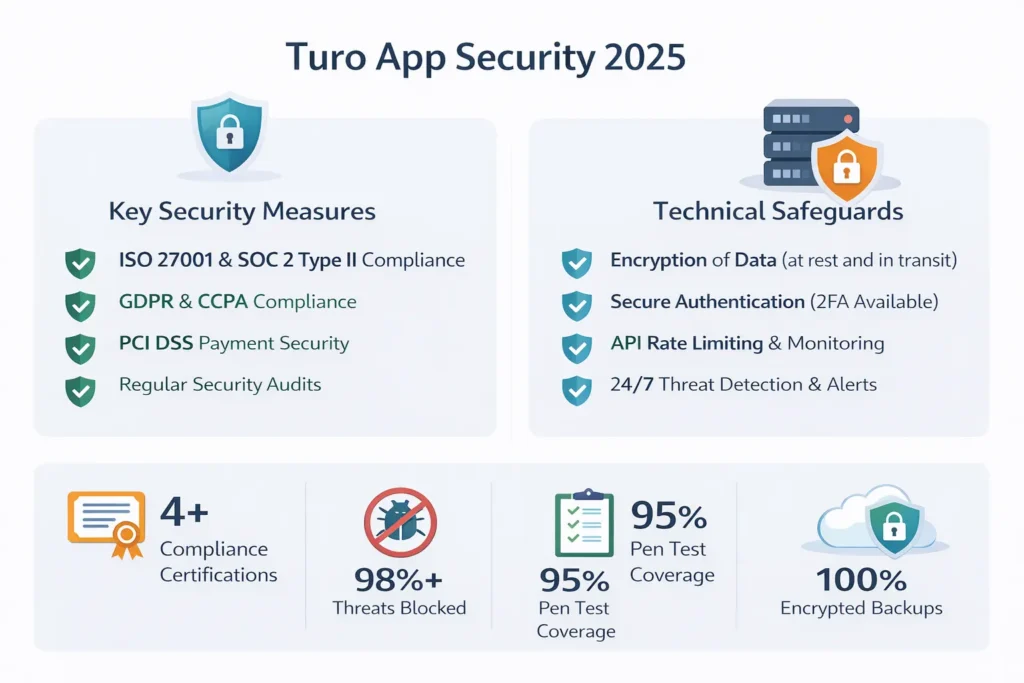
Warning Signs You Should Never Ignore
No Security Documentation
If a provider cannot clearly explain:
- How data is stored
- How access is controlled
- How incidents are handled
It usually means security is not formalized.
Unusually Cheap Pricing Without Explanation
Security has real costs — audits, monitoring, testing, and compliance. If pricing seems unrealistically low, security is often the first thing cut.
No Compliance Certifications or Roadmap
Even if certifications are “in progress,” a serious provider should show:
- A clear compliance plan
- Defined timelines
- Interim security controls
“No need for compliance” is a major red flag.
Outdated Technology Stack
Old frameworks and unpatched libraries are a common breach vector. Providers unwilling to modernize are exposing your app to known exploits.
Poor Code Quality
Signs include:
- No code documentation
- Hardcoded secrets
- Inconsistent logic across modules
- No automated testing
These issues often lead to hidden vulnerabilities.
No Security Update Policy
Security is ongoing. If the provider can’t answer:
- How often updates are released
- How vulnerabilities are patched
- Who is responsible post-launch
You are accepting long-term risk.
No Backup or Disaster Recovery System
Without tested backups:
- Ransomware can shut down the platform
- Data loss becomes permanent
- Business continuity is impossible
No Insurance Coverage
Reputable providers carry cyber liability or professional indemnity coverage. Lack of insurance means you carry all the risk.
Evaluation Checklist Before You Sign
Questions to Ask Providers
- How is each client’s app isolated at infrastructure level?
- Who has access to production data and logs?
- How are security incidents detected and escalated?
- What happens if a vulnerability is found after launch?
- How are third-party tools vetted and updated?
Documents to Request
- Security architecture overview
- Data flow diagrams
- Compliance certificates or audit summaries
- Incident response policy
- Backup and recovery documentation
Testing Procedures
- Pre-launch security audit or penetration test
- API security testing evidence
- Admin role and permission testing
- Payment and refund flow testing
Due Diligence Steps
- Speak with existing clients if possible
- Review app update history
- Check whether security fixes are documented
- Confirm long-term maintenance and patch support
A provider that resists transparency is not protecting your business.
Best Practices for Secure White-Label Turo App Implementation
Security is not a one-time checklist. For a white-label Turo-style app, safety must be built before launch and actively maintained after launch.
Pre-Launch Security Best Practices
Security Audit Process
Before going live, the app should undergo:
- Backend and API security audit
- Mobile app vulnerability testing
- Infrastructure and cloud configuration review
- Access control and role validation
This helps identify risks early, when fixes are faster and cheaper.
Code Review Requirements
A secure app must pass:
- Manual code review for authentication and authorization logic
- Automated dependency scanning for known vulnerabilities
- Validation of encryption implementation and secrets management
Code quality directly impacts long-term security.
Infrastructure Hardening
Key infrastructure steps include:
- Private network segmentation
- Firewalls and WAF protection
- Restricted admin access by IP and role
- Secure cloud storage permissions
Shared or open infrastructure increases breach probability.
Compliance Verification
Before launch, verify:
- GDPR and CCPA data handling workflows
- Consent collection and storage logic
- Data retention and deletion automation
- Payment flow compliance (PCI scope clarity)
Compliance gaps discovered after launch can halt operations.
Staff Training Programs
Security failures often come from human error. Teams should be trained on:
- Data access rules
- Incident escalation procedures
- Secure support operations
- Admin panel usage best practices
Post-Launch Security Monitoring
Continuous Security Monitoring
A production Turo-style app should run with:
- Real-time log monitoring
- Alerts for suspicious login attempts
- Alerts for abnormal booking or refund activity
- Monitoring of API abuse patterns
Early detection prevents small issues from becoming major incidents.
Regular Updates and Patching
Post-launch security requires:
- Monthly dependency updates
- Emergency patch deployment capability
- OS and server patch automation
- Mobile app security updates aligned with OS changes
Outdated apps are easy targets.
Incident Response Planning
A defined response plan should include:
- Clear severity classification
- Communication flow (internal and external)
- Temporary access restrictions
- Regulatory notification timelines
Speed and clarity matter during incidents.
User Data Management
Ongoing data protection includes:
- Periodic access reviews
- Automated data deletion on request
- Secure backup encryption
- Minimal data retention policies
Backup and Recovery Systems
A safe app must support:
- Automated daily backups
- Encrypted backup storage
- Periodic recovery testing
- Defined recovery time objectives
Backups are useless if they are never tested.
Security Implementation Timeline
- Week 1–2: Architecture review, compliance mapping, risk assessment
- Week 3–4: Code audit, API testing, infrastructure hardening
- Pre-Launch: Penetration testing, monitoring setup, staff training
- Post-Launch (Ongoing): Continuous monitoring, patching, audits
Security is not a launch feature — it’s a permanent operational responsibility.
Legal & Compliance Considerations
For a white-label Turo-style app, legal and compliance readiness is just as important as technical security. Even a small data incident can trigger legal action if compliance foundations are weak.
Regulatory Requirements
Data Protection Laws by Region
Your legal obligations depend on where your users are located:
- EU / UK: GDPR applies to identity documents, location data, and payment-related information
- United States: CCPA/CPRA applies to California users; other states are introducing privacy laws
- Asia-Pacific: Countries like India, Singapore, and Australia enforce local data protection rules
- Global Operations: Cross-border data transfer restrictions must be respected
Ignoring regional laws can result in service bans and heavy penalties.
Industry-Specific Regulations
A Turo-style app may trigger additional rules related to:
- Digital identity verification
- Online payments and refunds
- Consumer protection laws
- Vehicle rental and insurance disclosures
These are often enforced at local or state levels.
User Consent Management
Legal compliance requires:
- Explicit consent for data collection
- Clear opt-in for marketing communication
- Transparent handling of location tracking
- Easy consent withdrawal mechanisms
Consent must be recorded and auditable.
Privacy Policy Requirements
Your privacy policy must clearly explain:
- What data is collected and why
- How long data is stored
- Who data is shared with
- How users can request deletion or access
Generic templates are risky and often non-compliant.
Terms of Service Essentials
Terms should define:
- Platform responsibilities vs user responsibilities
- Liability limitations
- Dispute resolution processes
- Suspension and termination rules
These documents protect the business during disputes.
Liability Protection
Insurance Requirements
Founders should consider:
- Cyber liability insurance
- Professional indemnity coverage
- Data breach response coverage
Insurance helps cover legal fees, fines, and notification costs.
Legal Disclaimers
Clear disclaimers help reduce exposure by:
- Defining platform role clearly
- Limiting responsibility for third-party actions
- Explaining service limitations
Disclaimers must align with actual app behavior.
User Agreements
Well-structured agreements clarify:
- Data ownership
- User obligations
- Acceptable use policies
- Consequences of misuse
Incident Reporting Protocols
A compliant app must define:
- Internal reporting timelines
- User notification procedures
- Regulatory reporting obligations
- Documentation requirements
Delayed reporting often increases penalties.
Ongoing Compliance Monitoring
Compliance is continuous. Best practices include:
- Annual legal reviews
- Policy updates after feature changes
- Monitoring regulatory updates
- Periodic internal audits
Compliance Checklist by Region
- GDPR compliance mapping completed
- CCPA/CPRA user rights workflows implemented
- Consent logs stored securely
- Data deletion and export automated
- Privacy policy reviewed by legal counsel
- Incident response aligned with regulatory timelines
Read more : – How to Build an App Like Turo: A Developer’s Guide
Why Miracuves White-Label Turo App Is Your Safest Choice
Security is not treated as an add-on at Miracuves. It is designed into the core architecture of every white-label Turo-style app from day one. This approach reduces risk not just at launch, but throughout the entire lifecycle of the platform.
Miracuves Security Advantages
Enterprise-Grade Security Architecture
Each app is deployed with isolated infrastructure, ensuring:
- No shared databases between clients
- Strict separation of environments
- Role-based access control at every layer
This eliminates cross-client data exposure risks.
Regular Security Audits and Compliance Alignment
Miracuves follows structured security processes aligned with:
- ISO 27001 information security principles
- SOC 2 Type II–aligned operational controls
- GDPR and CCPA data protection requirements
Security is reviewed continuously, not only at launch.
Privacy-First and Compliance-Ready by Default
Every white-label Turo app includes:
- Built-in consent management
- Data minimization practices
- Automated data deletion and access workflows
- Clear audit trails for compliance checks
This significantly reduces regulatory risk for founders.
Encrypted Data Transmission and Storage
Miracuves enforces:
- End-to-end encryption for all sensitive data
- Secure key management practices
- Encrypted backups and recovery systems
User identity data, payment references, and location information remain protected at all times.
Secure Payment Processing
Payment flows are designed to:
- Minimize PCI exposure using tokenization
- Protect transaction data and webhooks
- Monitor refund and dispute abuse
This reduces fraud and chargeback risks.
24/7 Monitoring and Proactive Protection
Security does not stop after launch. Miracuves provides:
- Continuous monitoring of suspicious activity
- Alerting for abnormal admin or user behavior
- Regular vulnerability patching and updates
Issues are detected early, before they escalate.
Insurance and Risk Coverage Awareness
Miracuves platforms are designed with:
- Clear incident response procedures
- Documentation support for insurance claims
- Operational readiness for breach scenarios
This protects both the platform and its users.
Final Thought
Don’t compromise on security. Miracuves white-label Turo app solutions are built with enterprise-grade safety, compliance-ready architecture, and continuous protection. With 600+ successful deployments and zero major security breach incidents reported, Miracuves is trusted by businesses that take user safety and legal compliance seriously.
Get a free security assessment and understand how your car-sharing platform can launch with confidence, not risk.Choosing a security-first partner like Miracuves significantly reduces technical, legal, and reputational risk. When user trust, vehicle safety, and regulatory compliance are on the line, cutting corners is never worth it.
FAQs
1. How secure is a white-label Turo app compared to custom development?
A white-label Turo app can be just as secure as custom development when built with isolated infrastructure, audited code, and compliance-first architecture. Security depends on execution, not the development model.
2. What happens if there is a security breach?
A proper incident response plan includes immediate containment, user notification, regulatory reporting, and system remediation. Providers like Miracuves support structured breach handling to reduce damage and downtime.
3. Who is responsible for security updates?
Post-launch security updates are a shared responsibility, but the provider must deliver regular patches, vulnerability fixes, and infrastructure updates as part of ongoing maintenance.
4. How is user data protected in a white-label Turo app?
User data is protected using encryption at rest and in transit, strict access controls, secure APIs, and continuous monitoring to prevent unauthorized access.
5. What compliance certifications should I look for?
At minimum, look for ISO 27001-aligned security practices, SOC 2 Type II readiness, GDPR compliance, CCPA support, and PCI DSS–compliant payment handling.
6. Can a white-label Turo app meet enterprise security standards?
Yes. With proper architecture, audits, and monitoring, a white-label Turo app can meet the same enterprise-grade security standards as large mobility platforms.
7. How often should security audits be conducted?
Security audits should be done before launch, after major updates, and at least annually, with continuous monitoring running in parallel.
8. What is included in Miracuves’ security package?
Miracuves includes secure architecture, compliance-ready design, encrypted data handling, regular updates, monitoring support, and incident response readiness.
9. How do you manage security across different countries?
Security is managed through region-specific compliance mapping, data handling controls, consent management, and adaptable legal documentation per market.
10. What insurance is needed for app security?
Cyber liability and professional indemnity insurance are recommended to cover data breaches, legal claims, and regulatory penalties.
Related Articles: