You’ve heard the horror stories about crypto apps getting hacked, user wallets drained overnight, and businesses facing lawsuits due to weak security. When money, identity, and trust are involved, security is not optional.
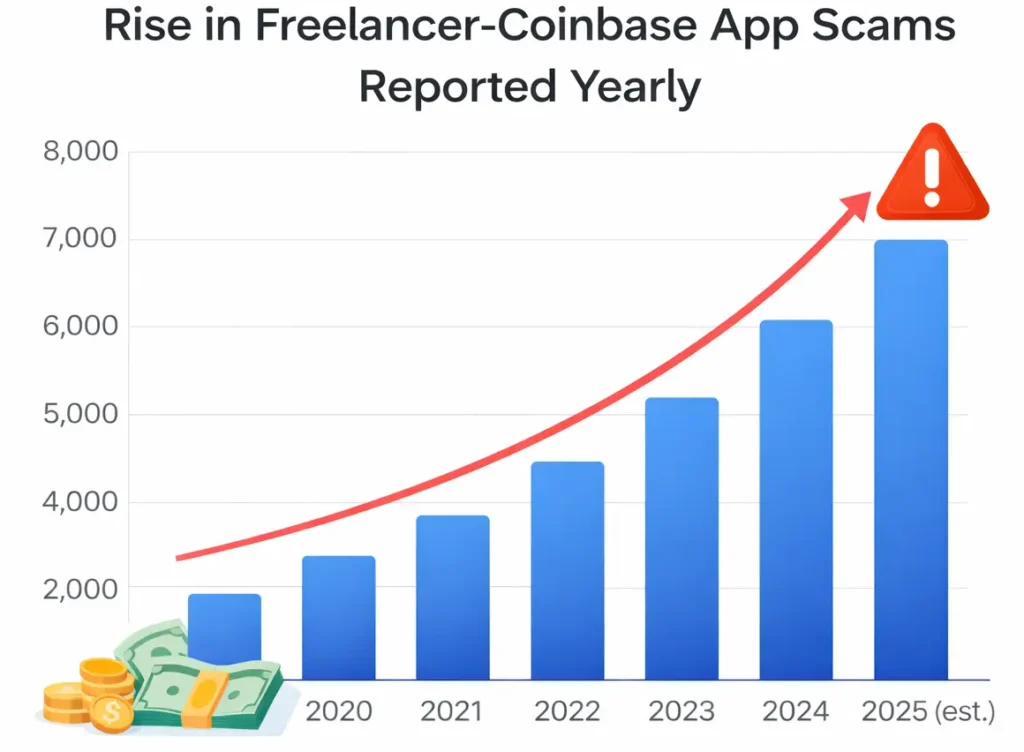
In 2026, white-label crypto trading apps like a Coinbase-style app are under constant attack from hackers, fraud rings, and compliance regulators. One weak link can cost millions.
This guide gives you a clear, honest assessment of white-label Coinbase app security, the real risks involved, and practical steps to stay safe. We’ll also show how Miracuves approaches security differently, putting protection first, not as an afterthought.
Understanding White-Label Coinbase App Security Landscape
What White-Label App Security Really Means
White-label app security refers to the protection mechanisms built into a ready-made crypto trading app that is rebranded for your business. The core architecture, backend logic, and security controls are shared, making the provider’s security standards critical.
Common Security Myths vs Reality
Many believe white-label apps are automatically insecure. In reality, poorly built white-label apps are risky, not the model itself. A security-first provider can offer enterprise-grade protection equal to custom-built platforms.
Read more : – Coinbase Revenue Model: How Coinbase Makes Money in 2026
Why Businesses Worry About White-Label Crypto Apps
Crypto apps handle user funds, identity data, and transaction history. Any vulnerability can lead to theft, regulatory penalties, or permanent loss of user trust.
Current Threat Landscape for Coinbase-Type Apps
Coinbase-style apps face wallet breaches, API abuse, phishing attacks, and smart fraud bots. Attackers now target backend infrastructure more than user interfaces.
Security Standards in 2026
Modern crypto apps are expected to follow zero-trust architecture, encrypted key management, continuous monitoring, and strict regulatory compliance.
Real-World Security Statistics
Over 60% of crypto app breaches in recent years were caused by weak APIs and misconfigured servers, not blockchain flaws. This makes backend security the top priority.
Key Security Risks & How to Identify Them
Data Protection & Privacy Risks
User Personal Information
KYC data such as IDs and addresses are prime targets for attackers if not encrypted properly.
Payment Data Security
Wallet keys, transaction logs, and fiat payment data must follow strict PCI DSS controls.
Location & Activity Tracking
Improper logging can expose user behavior patterns and trading history.
GDPR and CCPA Compliance
Failure to manage consent and data deletion can lead to heavy regulatory fines.
Technical Vulnerabilities
Code Quality Issues
Poorly written or reused code increases the risk of exploits and logic flaws.
Server Security Gaps
Misconfigured cloud servers are one of the leading causes of crypto app breaches.
API Vulnerabilities
Unsecured APIs allow attackers to manipulate trades, balances, or user accounts.
Third-Party Integrations
Payment gateways and analytics tools can become attack entry points.
Business-Level Risks
Legal Liability
Security breaches can trigger lawsuits and regulatory investigations.
Reputation Damage
One incident can permanently destroy user trust in a crypto platform.
Financial Losses
Losses include stolen assets, compensation costs, and downtime.
Regulatory Penalties
Non-compliance can result in license suspension or platform shutdowns.
Quick Risk Assessment Checklist
- Is all user data encrypted at rest and in transit?
- Are APIs protected with authentication and rate limits?
- Are regular security audits conducted?
- Is compliance documented and verifiable?
Read more : – Coinbase Marketing Strategy | Ride the Crypto Wave
Security Standards Your White-Label Coinbase App Must Meet
Essential Compliance Certifications
ISO 27001
Ensures a structured information security management system for handling sensitive crypto and user data.
SOC 2 Type II
Validates long-term security, availability, and confidentiality controls for cloud-based crypto apps.
GDPR Compliance
Required for handling EU user data, including consent management and right-to-erasure processes.
HIPAA (If Applicable)
Relevant only if the app integrates identity or health-linked financial services.
PCI DSS
Mandatory for handling card-based fiat deposits and withdrawals securely.
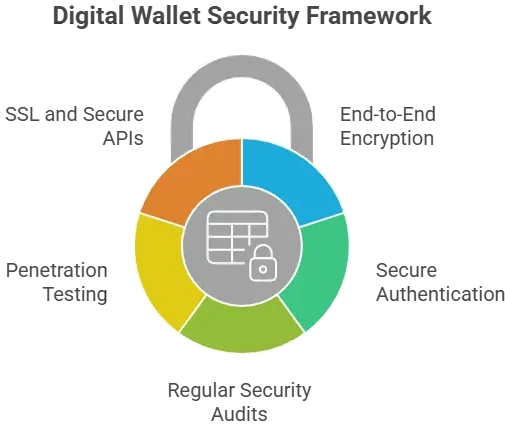
Security Standards Comparison Overview
A secure Coinbase-style app must meet the same standards as major crypto exchanges, not just basic mobile app security.
Red Flags: How to Spot Unsafe White-Label App Providers
Major Warning Signs
No Security Documentation
Providers who cannot explain their security architecture usually do not have one.
Unrealistically Cheap Pricing
Low cost often means skipped audits, weak infrastructure, and outdated protection.
Missing Compliance Certifications
Lack of ISO, SOC, or GDPR compliance is a serious risk indicator.
Outdated Technology Stack
Old frameworks are more vulnerable to modern attack methods.
Poor Code Quality
Unstructured and copied code increases exploit possibilities.
No Security Update Policy
Without regular patches, vulnerabilities remain open.
No Backup and Recovery Systems
Data loss after an incident can be irreversible.
No Cyber Insurance Coverage
Insurance is a sign of operational maturity and risk planning.
Provider Evaluation Checklist
Questions to Ask
- How is wallet and key security handled?
- How often are audits performed?
- What is the incident response process?
Documents to Request
- Compliance certificates
- Audit reports
- Data protection policies
Testing Procedures
- Demo penetration test results
- API security testing proof
Due Diligence Steps
- Verify past security incidents
- Review client case studies
Best Practices for Secure White-Label Coinbase App Implementation
Pre-Launch Security Measures
Security Audit Process
Conduct full code, infrastructure, and wallet audits before launch.
Code Review Standards
Ensure secure coding practices and removal of unused components.
Infrastructure Hardening
Use private networks, firewalls, and access control policies.
Compliance Verification
Confirm all regulatory and regional compliance requirements.
Team Security Training
Train staff on phishing, access management, and incident handling.
Post-Launch Security Monitoring
Continuous Monitoring
Track suspicious logins, transactions, and API usage in real time.
Regular Updates and Patches
Apply security fixes immediately after discovery.
Incident Response Planning
Define clear steps for breach detection and containment.
User Data Management
Limit access to sensitive data based on roles.
Backup and Recovery Systems
Maintain encrypted backups with tested restoration plans.
Security Implementation Timeline
Security must be planned before launch and continuously improved after release.
Legal & Compliance Considerations
Regulatory Requirements
Data Protection Laws by Region
Different regions enforce different data protection rules such as GDPR in Europe and CCPA in the United States.
Crypto Industry Regulations
Licensing, AML, and KYC regulations are mandatory for Coinbase-type apps.
User Consent Management
Clear consent collection and storage are legally required.
Privacy Policy Requirements
Policies must clearly explain data usage and storage practices.
Terms of Service Essentials
User rights, limitations, and dispute handling must be defined.
Liability and Risk Protection
Cyber Insurance Requirements
Insurance helps mitigate financial impact after a security incident.
Legal Disclaimers
Defines responsibility boundaries between the platform and users.
User Agreements
Clarifies data ownership and security responsibilities.
Incident Reporting Protocols
Timely reporting is required under most regulations.
Ongoing Compliance Monitoring
Regulations evolve and must be continuously tracked.
Regional Compliance Checklist
Compliance must be reviewed separately for each operating country.
Read more : – How to Hire the Best Coinbase Clone Developer
Why Miracuves White-Label Coinbase App Is Your Safest Choice
Miracuves Security Advantages
Enterprise-Grade Security Architecture
Built with multi-layer protection covering infrastructure, APIs, and user wallets.
Regular Security Audits and Certifications
Independent audits ensure continuous compliance with global standards.
GDPR and CCPA Compliance by Default
Privacy and consent management are built into the app from day one.
24/7 Security Monitoring
Threat detection systems actively monitor suspicious activity.
Encrypted Data Transmission
All sensitive data is encrypted in transit and at rest.
Secure Payment Processing
PCI DSS–compliant payment handling protects fiat transactions.
Routine Security Updates
Security patches are deployed regularly to address new threats.
Insurance Coverage Included
Cyber risk coverage reduces financial exposure.
Final Thought
Don’t compromise on security. Miracuves white-label Coinbase app solutions come with enterprise-grade security built in. With 600+ successful projects and zero major security breaches, Miracuves delivers safe, compliant crypto platforms. Get a free security assessment and see why businesses trust Miracuves.
Security is not a feature you add later to a white-label Coinbase app. It is the foundation that determines whether your platform survives in a highly regulated and attack-prone crypto market. Choosing a security-first provider like Miracuves helps you launch faster, stay compliant, and protect user trust from day one.
FAQs
1. How secure is a white-label Coinbase app compared to custom development?
A white-label Coinbase app can be equally secure if it follows enterprise security standards, regular audits, and compliance frameworks like ISO and SOC 2.
2. What happens if there is a security breach?
A proper incident response plan includes detection, containment, user notification, regulatory reporting, and recovery backed by insurance coverage.
3. Who is responsible for security updates?
The white-label app provider manages core security updates, while the business ensures operational security and compliance usage.
4. How is user data protected in a Coinbase-type app?
User data is protected using encryption, access controls, secure authentication, and compliance-driven data handling policies.
5. What compliance certifications should I look for?
ISO 27001, SOC 2 Type II, GDPR, CCPA, and PCI DSS are essential for crypto trading apps.
6. Can white-label apps meet enterprise security standards?
Yes, when built with security-first architecture, continuous monitoring, and third-party audits.
7. How often should security audits be conducted?
At least annually, with continuous vulnerability scanning throughout the year.
8. What is included in the Miracuves security package?
Audits, encryption, compliance readiness, monitoring, secure payments, updates, and insurance coverage.
9. How is security handled across different countries?
Compliance and data handling are adjusted based on regional laws and regulatory requirements.
10. What insurance is required for app security?
Cyber liability and data breach insurance are essential for financial and legal protection.
Related Articles








