You’ve heard the horror stories about data breaches, leaked customer information, and payment fraud. And if you’re planning to launch a white-label Rakuten-style app, you’re probably thinking one thing:
“Is this going to be safe… or am I walking into a security disaster?”
That fear is valid.
In 2026, shopping and cashback-style platforms are bigger targets than ever. These apps handle sensitive user data, payment details, transaction history, and sometimes even location tracking. A single weak link can lead to customer trust collapse, legal penalties, and financial damage.
In this guide, I’ll give you an honest assessment of white-label Rakuten app safety, the real risks you must watch for, and practical security steps to protect your business. And yes, we’ll also cover how Miracuves builds security-first white-label solutions so you don’t have to gamble with compliance or customer data.
Understanding White-Label Rakuten App Security Landscape
What “White-Label Security” Actually Means
White-label Rakuten app security refers to the protection framework built into a ready-made cashback and affiliate commerce platform that businesses rebrand and launch as their own.
Security depends entirely on:
- Code quality
- Server infrastructure
- Data handling architecture
- Compliance implementation
- Update and monitoring practices
A white-label app is not automatically unsafe. It becomes risky only when built without enterprise-grade security standards.
Why People Worry About White-Label Apps
Cashback and affiliate commerce platforms:
- Store user identities
- Handle payment data
- Track transactions
- Integrate third-party APIs
- Process referral commissions
That creates multiple entry points for cyber threats.
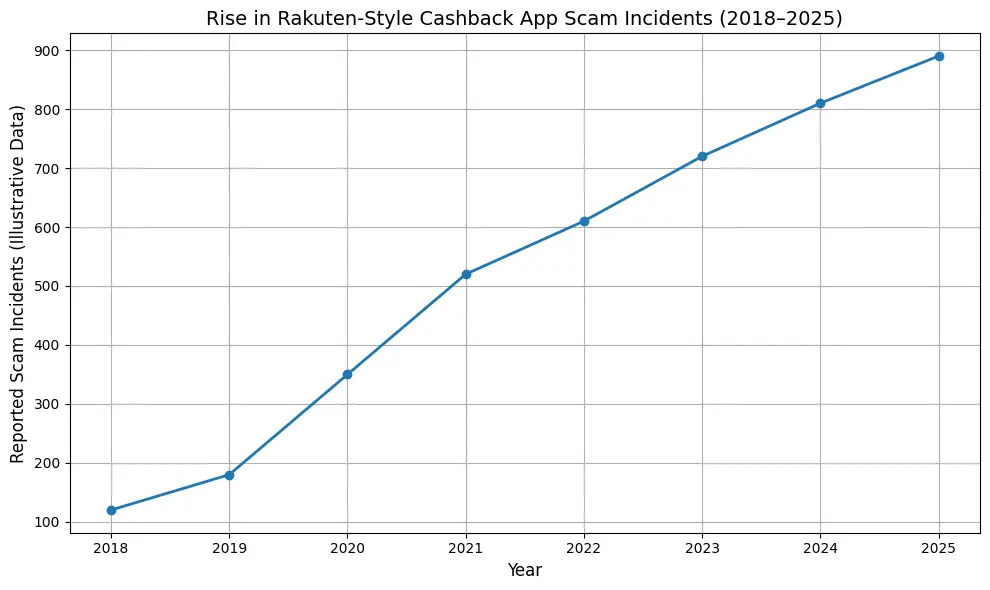
Current Threat Landscape for Cashback & Affiliate Platforms (2026)
In 2025–2026 reports from cybersecurity firms show:
- Over 60% of web application breaches involved API vulnerabilities
- E-commerce and affiliate platforms remain in the top 3 most targeted industries
- Misconfigured cloud storage continues to cause large-scale data exposure
Rakuten-style apps are especially vulnerable to:
- Payment fraud
- Account takeovers
- API manipulation
- Cashback exploitation bots
- Affiliate commission abuse
Security Standards in 2026
In 2026, serious white-label Rakuten app providers must align with:
- ISO 27001 for information security management
- SOC 2 Type II for operational security controls
- GDPR and CCPA for user data protection
- PCI DSS 4.0 for payment security
- OWASP Top 10 mitigation standards
Anything less is outdated.
Real-World Statistics on App Security Incidents
Recent global studies show:
- 43% of cyberattacks target web applications
- Average cost of a data breach crossed $4.4 million globally
- Payment-related breaches carry higher regulatory penalties
For a cashback app, even one breach can erase years of brand trust.
Key Security Risks & How to Identify Them
Data Protection & Privacy Risks
Rakuten-style cashback apps collect more sensitive data than most people realize.
User Personal Information
High-risk data includes:
- Name, phone, email
- Address (sometimes)
- Shopping behavior and purchase history
If this leaks, the business faces reputation loss and legal action.
Payment Data Security
Even if your app uses a payment gateway, risks still exist:
- Card token exposure
- Weak checkout API security
- Insecure transaction logs
For 2026, PCI DSS 4.0 compliance is not optional if payments are involved.
Location Tracking Concerns
Some cashback apps use location for:
- Nearby offers
- Store-based cashback
- Fraud detection
If location data is stored insecurely, it becomes a serious privacy risk.
GDPR/CCPA Compliance
Major compliance risks:
- Collecting data without consent
- No user data deletion option
- Weak privacy policy
- Poor cookie and tracking disclosure
Technical Vulnerabilities
Code Quality Issues
Many unsafe white-label apps have:
- Hardcoded API keys
- Weak validation logic
- Outdated dependencies
This is where most breaches begin.
Server Security Gaps
Common problems:
- Misconfigured cloud storage
- No firewall rules
- Weak admin panel security
- No separation between production and testing servers
API Vulnerabilities
Rakuten-style apps heavily depend on APIs:
- Cashback calculation APIs
- Affiliate partner APIs
- Payment APIs
- User profile APIs
The biggest threats:
- Broken authentication
- Broken access control
- API request manipulation
- Data leakage via API responses
Third-Party Integrations
Affiliate platforms often connect with:
- Payment gateways
- Offer providers
- Coupon providers
- Analytics tools
Each integration increases risk if not audited.
Business Risks
Legal Liability
If user data leaks, liability can fall on:
- Your company (brand owner)
- The white-label provider
- Both (depending on contracts)
Reputation Damage
A cashback app depends on trust.
One breach can permanently reduce user retention.
Financial Losses
Loss comes from:
- Fraud refunds
- Chargebacks
- System downtime
- Legal fees
- Customer compensation
Regulatory Penalties
In 2026, privacy laws are stricter and faster:
- GDPR fines can reach 4% of annual revenue
- CCPA penalties can stack per affected user
Risk Assessment Checklist (Quick Self-Test)
Use this checklist before choosing any white-label Rakuten app provider:
- Is data encrypted at rest and in transit?
- Are APIs protected with OAuth 2.0 or token-based auth?
- Is there role-based access control for admin users?
- Does the provider offer penetration testing reports?
- Are regular security updates included?
- Is PCI DSS compliance supported for payments?
- Are logs monitored 24/7 for suspicious activity?
- Is there a documented incident response plan?
- Are backups automated and tested?
- Is GDPR/CCPA compliance built-in by default?
If the provider cannot answer even 3 of these clearly, that’s a red flag.
Read more : – Business Model of Rakuten : Complete Strategy Breakdown 2025
Security Standards Your White-Label Rakuten App Must Meet
If a provider claims their white-label Rakuten app is “secure,” these are the standards they should be able to discuss confidently.
ISO 27001 Compliance
ISO 27001 ensures the company follows a structured Information Security Management System (ISMS).
This matters because it proves security is not random or “developer dependent.”
What it covers:
- Risk management
- Access controls
- Incident handling
- Vendor security
- Data protection policies
SOC 2 Type II
SOC 2 Type II is one of the strongest proof points for SaaS and platform security in 2026.
It validates:
- Security controls
- Availability controls
- Confidentiality and privacy processes
- Monitoring and audit trails over time (not just one-time)
GDPR Compliance
Required if you handle EU users.
Key requirements:
- User consent collection
- Data minimization
- Right to access and deletion
- Breach reporting timelines
- Data processing agreements (DPA)
HIPAA (If Applicable)
Not required for most Rakuten-style apps.
But if your platform includes health-related rewards, insurance rewards, or medical cashback programs, HIPAA may apply.
PCI DSS for Payments
Mandatory if you process payments, store card tokens, or handle recurring billing.
In 2026, PCI DSS 4.0 is the expected standard.
Technical Requirements
This is where many white-label providers fail.
End-to-End Encryption
Minimum expected:
- TLS 1.2+ (ideally TLS 1.3)
- Encrypted database storage for sensitive fields
- Encryption keys managed securely (not stored in code)
Secure Authentication (2FA/OAuth)
A safe Rakuten-style app should include:
- OAuth 2.0 / OpenID Connect
- Optional 2FA for users
- Mandatory 2FA for admin accounts
- Secure password policies + hashing (bcrypt/argon2)
Regular Security Audits
Security audits should happen:
- Before launch
- After major updates
- At least quarterly for production systems
Penetration Testing
Pen tests help identify:
- API exploitation risks
- Injection vulnerabilities
- Session hijacking issues
- Admin panel weaknesses
A serious provider should share:
- Pen test summary reports
- Fix verification proof
SSL Certificates
Basic but non-negotiable:
- HTTPS everywhere
- HSTS enabled
- No mixed content issues
Secure API Design
Your white-label Rakuten app must protect APIs against:
- Broken access control
- Rate-limit bypass
- Replay attacks
- Token theft
- Excessive data exposure
Security Standards Comparison Table
| Standard / Requirement | What It Protects | Must-Have for Rakuten App? | Risk If Missing |
|---|---|---|---|
| ISO 27001 | Company-wide security management | Strongly recommended | Weak security culture |
| SOC 2 Type II | Operational controls and audits | Highly recommended | No proof of controls |
| GDPR | EU user privacy and rights | Required if EU users | Heavy fines + lawsuits |
| CCPA | California consumer privacy | Required if US users | Legal penalties |
| PCI DSS 4.0 | Payment and card data security | Required if payments | Fraud + compliance failure |
| OWASP Top 10 | Web/app vulnerabilities | Mandatory baseline | Easy hacking entry |
| Pen Testing | Real-world attack simulation | Mandatory | Hidden vulnerabilities |
| Encryption | Data protection | Mandatory | Data leak risk |
| 2FA / OAuth | Account security | Mandatory | Account takeovers |
Red Flags — How to Spot Unsafe White-Label Providers
Choosing the wrong white-label Rakuten app provider can expose your business to long-term risk. Security issues usually leave visible signs. You just need to know what to look for.
Warning Signs
No Security Documentation
If the provider cannot share:
- Security architecture overview
- Compliance certificates
- Audit summaries
- Data handling policies
That’s a major red flag.
Cheap Pricing Without Explanation
Enterprise-grade security costs money.
If pricing is dramatically lower than market average without technical clarity, corners are likely being cut in infrastructure or testing.
No Compliance Certifications
If they say:
“We follow best practices”
but cannot show ISO, SOC 2, or PCI DSS alignment, treat it as unverified claims.
Outdated Technology Stack
Warning indicators:
- Old PHP versions
- Deprecated libraries
- No dependency update process
- No documented patch cycle
Outdated stacks are among the top causes of exploitation.
Poor Code Quality
Signs include:
- Slow performance
- Frequent bugs
- Poor API responses
- No structured logging
Security issues often hide behind unstable systems.
No Security Updates Policy
Ask directly:
“How often do you release security patches?”
If the answer is unclear or reactive-only, risk increases significantly.
Lack of Data Backup Systems
A secure white-label Rakuten app must have:
- Automated backups
- Encrypted storage
- Restore testing procedures
No backup strategy equals business continuity risk.
No Insurance Coverage
Professional providers carry:
- Cyber liability insurance
- Professional indemnity coverage
Without insurance, financial exposure may fall entirely on you.
Evaluation Checklist
Before signing with any provider, ask these questions.
Questions to Ask Providers
- Are you ISO 27001 certified or aligned?
- Do you have SOC 2 Type II reports?
- Is PCI DSS 4.0 supported?
- How do you secure APIs?
- Is data encrypted at rest and in transit?
- Do you support GDPR/CCPA compliance by default?
- What is your incident response time?
Documents to Request
- Security whitepaper
- Compliance certificates
- Penetration testing summary
- Data processing agreement (DPA)
- SLA document
Testing Procedures
- Conduct third-party vulnerability scans
- Test admin panel security
- Review API authentication
- Perform load and stress testing
- Review access control models
Due Diligence Steps
- Check client references
- Review previous security incidents
- Verify compliance authenticity
- Confirm cloud infrastructure provider
- Review backup and disaster recovery process
If a provider resists transparency, that alone is enough to reconsider.
Best Practices for Secure White-Label Rakuten App Implementation
A white-label Rakuten app can be secure, but only if security is treated as a system, not a one-time feature.
This section covers what you should do before launch and after launch to reduce risk.
Pre-Launch Security
Security Audit Process
Before you launch, you need a full security audit covering:
- App codebase
- APIs
- Admin panel
- Cloud infrastructure
- Database and storage security
A serious provider (like Miracuves) should already have this built into the delivery process.
Code Review Requirements
Code review should include:
- OWASP Top 10 checks
- Dependency vulnerability scan
- Authentication and session handling review
- Input validation review
This is how you prevent issues like SQL injection, XSS, and token leaks.
Infrastructure Hardening
Your hosting environment must include:
- Web Application Firewall (WAF)
- DDoS protection
- Secure VPC setup
- IAM role-based permissions
- Database access restrictions
- Zero public access to storage buckets
Most breaches happen because servers are misconfigured, not because the app was “hacked like in movies.”
Compliance Verification
Before launch, confirm:
- GDPR consent flows are working
- Privacy policy is accurate
- Cookie tracking disclosure exists
- Payment systems align with PCI DSS requirements
Staff Training Programs
Even the best security fails if the team is careless.
Train staff on:
- Phishing and social engineering
- Admin access hygiene
- Secure password and 2FA policies
- Data handling rules
Post-Launch Monitoring
Continuous Security Monitoring
A secure Rakuten-style app must monitor:
- Suspicious logins
- Cashback abuse patterns
- Fraud transactions
- API rate-limit violations
- Admin panel access logs
This is one of the biggest differences between safe and unsafe providers.
Regular Updates and Patches
Security patching should be:
- Scheduled (monthly minimum)
- Emergency-based for critical CVEs
- Documented and tracked
If your provider does not have a patch process, the app becomes unsafe over time.
Incident Response Planning
You need:
- A breach response plan
- A communication strategy
- A reporting workflow for GDPR/CCPA
- A dedicated technical escalation team
In 2026, slow breach response can cause more damage than the breach itself.
User Data Management
Best practices include:
- Data minimization (collect only what’s needed)
- Secure deletion workflows
- Clear consent tracking
- Export/download options for compliance
Backup and Recovery Systems
Your business continuity depends on:
- Daily automated backups
- Encrypted backups
- Recovery testing every month
- Disaster recovery strategy (multi-region if possible)
Security Implementation Timeline
| Timeline | What Should Happen | Goal |
|---|---|---|
| Week 1 | Security audit + risk assessment | Identify weak areas early |
| Week 2 | Code review + vulnerability scanning | Remove OWASP risks |
| Week 3 | Infrastructure hardening + access control setup | Prevent server breaches |
| Week 4 | Compliance checks + pen testing | Confirm launch readiness |
| Post-launch (ongoing) | Monitoring + updates + incident response drills | Stay secure long-term |
Legal & Compliance Considerations
Security is not just technical in 2026. For a white-label Rakuten app, legal compliance is part of safety. If compliance is weak, your platform becomes a liability even if the code is strong.
Regulatory Requirements
Data Protection Laws by Region
Here’s what typically applies in 2026:
- European Union: GDPR
- United Kingdom: UK GDPR + Data Protection Act
- United States: CCPA/CPRA (California) + state privacy laws
- Canada: PIPEDA
- India: DPDP Act (Digital Personal Data Protection Act)
- Australia: Privacy Act + Notifiable Data Breaches scheme
- Middle East: Increasing privacy regulations (varies by country)
If you plan to scale globally, your app must support multi-region compliance from day one.
Industry-Specific Regulations
Rakuten-style apps may also fall under:
- Consumer protection laws
- Advertising and affiliate disclosure rules
- Financial and payments regulations (depending on features)
If you offer wallet systems, stored credits, or cashback balance withdrawals, regulations can become stricter.
User Consent Management
A compliant app must support:
- Clear consent checkboxes
- Consent logs (timestamp + version)
- Marketing opt-in controls
- Withdrawal of consent
This is one of the most common compliance gaps in white-label apps.
Privacy Policy Requirements
Your privacy policy must clearly explain:
- What data is collected
- Why it is collected
- Who it is shared with (affiliate partners)
- How long it is stored
- How users can delete their data
If the provider gives you a generic privacy template, that is risky.
Terms of Service Essentials
Terms must cover:
- Cashback eligibility rules
- Fraud and abuse policies
- Account suspension conditions
- Refund and dispute handling
- Partner offer limitations
This protects you from cashback exploitation and legal disputes.
Liability Protection
Insurance Requirements
For 2026, serious platforms commonly carry:
- Cyber liability insurance
- Professional indemnity insurance
- Errors and omissions coverage
This matters because breach-related claims can be financially devastating.
Legal Disclaimers
You should include disclaimers for:
- Affiliate offer accuracy
- Cashback timing
- Partner service availability
- Third-party tracking limitations
This reduces disputes and chargeback risk.
User Agreements
Your agreements should clearly define:
- User responsibilities
- Fraud consequences
- Data usage rights
- Dispute resolution process
Incident Reporting Protocols
A compliant app must support:
- Breach detection logging
- Regulatory reporting timelines
- Customer notification procedures
For GDPR, breach reporting may need to happen within 72 hours.
Regulatory Compliance Monitoring
Compliance is not “set and forget.”
You need:
- Regular policy reviews
- Updated consent flows
- Tracking for new privacy laws
- Ongoing vendor compliance checks
Compliance Checklist by Region
| Region | Key Laws | Must-Have Compliance Features |
|---|---|---|
| EU | GDPR | Consent logs, deletion rights, DPA |
| UK | UK GDPR | Same as GDPR + UK-specific handling |
| USA | CCPA/CPRA + state laws | Opt-out, disclosure, deletion rights |
| Canada | PIPEDA | Consent + transparency |
| India | DPDP Act | Consent + secure storage + deletion |
| Australia | Privacy Act | Breach reporting + privacy controls |
Why Miracuves White-Label Rakuten App is Your Safest Choice
Launching a white-label Rakuten app is not just about features. It’s about trust, compliance, and long-term protection. That’s where Miracuves stands apart.
Miracuves Security Advantages
Enterprise-Grade Security Architecture
Miracuves builds every white-label Rakuten app with:
- Secure cloud infrastructure
- Role-based access control
- Hardened production environments
- Segregated testing and live servers
Security is structured, not optional.
Regular Security Audits and Certifications
Our development and deployment process aligns with:
- ISO 27001 security practices
- SOC 2-aligned operational controls
- OWASP Top 10 mitigation
- PCI DSS-ready payment integrations
Security is verified, not assumed.
GDPR/CCPA Compliant by Default
We integrate:
- Consent management flows
- Data deletion tools
- Privacy-first architecture
- Secure user data storage
Compliance is built into the framework.
24/7 Security Monitoring
Miracuves solutions include:
- Suspicious activity monitoring
- API abuse detection
- Fraud pattern tracking
- Admin access monitoring
We don’t wait for problems. We detect them early.
Encrypted Data Transmission
All white-label Rakuten apps from Miracuves use:
- TLS 1.2+ encryption
- Encrypted sensitive database fields
- Secure key management
User data stays protected in transit and at rest.
Secure Payment Processing
We support:
- PCI DSS-aligned gateways
- Tokenization systems
- Secure webhook validation
- Fraud detection integrations
Payment security is non-negotiable.
Regular Security Updates
Our update policy includes:
- Continuous patch management
- Vulnerability monitoring
- Dependency updates
- Critical CVE response handling
Your platform remains secure even as threats evolve.
Insurance Coverage Included
Miracuves-backed projects are supported by:
- Professional liability safeguards
- Structured legal agreements
- Security-first development SLAs
You are not left exposed.
Final Thought
Don’t compromise on security. Miracuves white-label Rakuten app solutions come with enterprise-grade security built in. Our 600+ successful projects have maintained zero major security breaches.
Get a free security assessment and see why businesses trust Miracuves for safe, compliant platforms.
If you choose the right provider, you get a fast launch, strong compliance, and a platform users can trust. If you choose the wrong one, even one small vulnerability can turn into a costly breach.
That’s why Miracuves focuses on security-first white-label Rakuten app development, so you can grow confidently without carrying hidden risks.
FAQs
1. How secure is white-label vs custom development?
White-label can be more secure if the provider follows ISO 27001, SOC 2 controls, and regular penetration testing. Custom is only safer when built by a highly mature security team.
2. What happens if there’s a security breach?
You may face user trust loss, legal reporting requirements, fines, and financial damages. A secure provider helps with incident response, investigation, and patching immediately.
3. Who is responsible for security updates?
In most cases, the white-label provider must handle core platform updates, while your business manages admin access, policies, and user-side controls. Miracuves includes regular security updates in the package.
4. How is user data protected in white-label apps?
Through encryption, secure APIs, role-based access control, logging, monitoring, and compliance-driven data handling practices.
5. What compliance certifications should I look for?
ISO 27001 alignment
SOC 2 Type II
GDPR/CCPA compliance support
PCI DSS readiness for payments
6. Can white-label apps meet enterprise security standards?
Yes, if the platform is designed for compliance, uses hardened infrastructure, and includes continuous security monitoring.
7. How often should security audits be conducted?
Before launch
After major updates
Quarterly for production systems
8. What’s included in Miracuves security package?
Secure architecture
GDPR/CCPA-ready framework
Encryption and secure APIs
Regular updates
Monitoring support
Audit and compliance assistance
9. How to handle security in different countries?
Consent logging
Data residency options
Local privacy policy updates
Regulatory reporting workflows
10. What insurance is needed for app security?
Cyber liability insurance
Professional indemnity insurance
Errors and omissions coverage
Related Articles