You’ve heard the horror stories about data breaches, leaked customer lists, hacked admin panels, and marketing automation platforms getting used for spam or fraud. And if you’re planning to launch a white-label ActiveCampaign app, it’s normal to ask one big question first:
Is it actually safe?
In 2026, app security is no longer a “nice-to-have.” It directly impacts your customer trust, deliverability reputation, legal compliance, and even payment processing approvals. One weak API or misconfigured server can expose sensitive CRM data like emails, phone numbers, tags, purchase history, campaign logs, and automation triggers.
In this guide, I’ll give you an honest assessment of white-label ActiveCampaign app security, the real risks to watch for, and practical steps to make your platform compliant and secure. And yes, I’ll also show what “security-first” looks like when you build with Miracuves.
Understanding White-Label ActiveCampaign App Security Landscape
A white-label ActiveCampaign app is not just an email marketing tool. It becomes a full customer-data platform that stores and processes sensitive business information. That’s why security expectations are much higher than normal apps.
What “White-Label Security” Actually Means
White-label security means the provider is giving you a ready app framework, but the responsibility of protecting data is shared.
Security depends on:
- Code quality of the app
- Cloud infrastructure setup
- Authentication and admin controls
- Data storage and encryption
- Update and patch management
Common Security Myths vs Reality
Many buyers assume:
- “White-label apps are insecure by default” (Not always true)
- “Custom development is always safer” (Not always true)
- “If the app works, it must be secure” (Wrong)
- “Security is only about SSL” (Very incomplete)
Reality is simple: a white-label app can be enterprise-grade secure, but only if built with compliance, audits, and secure architecture from day one.
Why People Worry About White-Label ActiveCampaign Apps
The concern is valid because these apps handle:
- Customer email lists (high-value breach target)
- Automation workflows (can be exploited for abuse)
- API connections (easy entry point for attackers)
- Admin access (high privilege risk)
- Campaign analytics and segmentation (business-sensitive data)
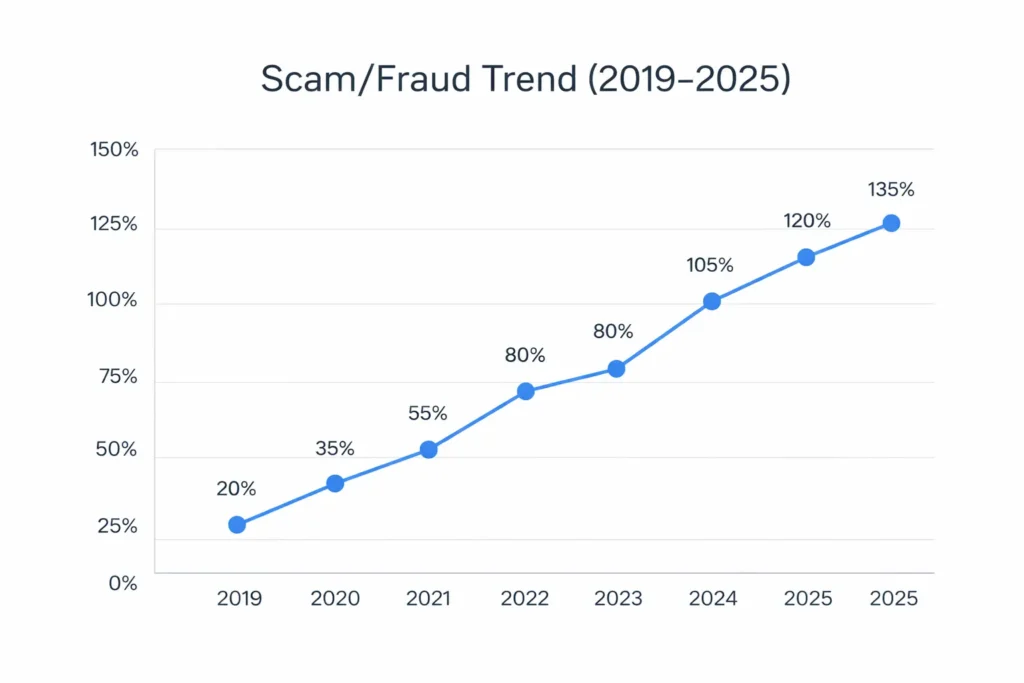
Current Threat Landscape for Marketing Automation Platforms (2026)
In 2026, the biggest threats for this type of app are:
- Credential stuffing and account takeovers
- API abuse and token leaks
- Misconfigured databases exposing contacts
- Malicious integrations and webhooks
- Spam abuse causing domain/IP blacklisting
- Insider threats through admin misuse
Security Standards in 2026 (What Buyers Expect)
Modern buyers expect:
- Strong encryption (in transit + at rest)
- Secure authentication (2FA, OAuth, SSO options)
- Role-based access control (RBAC)
- Regular vulnerability testing
- Audit logs for admin actions
- GDPR-ready privacy controls
Real-World Statistics on App Security Incidents
Across SaaS and CRM-style platforms, the most common real-world causes of breaches are:
- Weak passwords and stolen credentials
- Unpatched vulnerabilities
- Misconfigured cloud storage
- Over-permissioned admin roles
- Exposed API keys
That’s why security is not just a “developer task.” It is an operational system.
Key Security Risks & How to Identify Them
A white-label ActiveCampaign app becomes a high-risk platform because it holds customer databases, automation rules, and campaign delivery controls. If attackers access even one admin account, they can damage your business in hours.
Data Protection & Privacy Risks
High-risk data areas include:
User Personal Information
Your app stores:
- Names, emails, phone numbers
- Tags, segments, behavioral activity
- CRM notes and deal history
Risk: database exposure or unauthorized exports.
Payment Data Security
If your app includes billing, upgrades, subscriptions, or payment links:
- Card data must never be stored directly
- Tokenization must be used via payment gateways
Risk: PCI violations and chargeback disputes.
Location Tracking Concerns
Most marketing automation apps do not need live location, but they may collect:
- IP addresses
- device identifiers
- login activity locations
Risk: privacy complaints if not disclosed properly.
GDPR/CCPA Compliance
If you serve EU or California users, your app must support:
- consent capture
- data deletion requests
- data export requests
- lawful basis tracking
Risk: regulatory penalties and legal complaints.
Technical Vulnerabilities
This is where most white-label apps fail if security is not built-in.
Code Quality Issues
Common problems:
- insecure file uploads
- weak input validation
- hardcoded secrets
- poor session handling
Server Security Gaps
Infrastructure issues include:
- open ports
- weak firewall rules
- no WAF protection
- missing rate limits
API Vulnerabilities
Marketing automation apps depend heavily on APIs. Risks include:
- broken authentication
- insecure tokens
- missing throttling
- exposed endpoints
Third-Party Integrations
Webhooks and integrations can become entry points if:
- tokens are leaked
- webhook payloads are not validated
- permissions are too broad
Business Risks
Security issues are not only technical. They become business disasters.
Legal Liability
If customer data leaks, you may be responsible even if the provider built the app.
Reputation Damage
One incident can destroy trust permanently, especially in CRM and email marketing platforms.
Financial Losses
Direct losses include:
- downtime
- incident response costs
- refunds and cancellations
- spam blacklisting recovery
Regulatory Penalties
If GDPR or privacy rules are violated, penalties can be severe depending on region and severity.
Risk Assessment Checklist (Quick Scan)
Use this checklist before choosing or launching your white-label ActiveCampaign app:
- Does the app support 2FA for admin logins?
- Is user data encrypted at rest and in transit?
- Are API keys stored securely (not hardcoded)?
- Is RBAC available (admin, manager, user roles)?
- Are audit logs enabled for critical actions?
- Is there rate limiting for login and API requests?
- Are backups automated and tested regularly?
- Is there a security patch/update policy in writing?
- Are GDPR/CCPA features built-in (export/delete/consent)?
- Is penetration testing done at least yearly?
Security Standards Your White-Label ActiveCampaign App Must Meet
If you want enterprise clients, agency partners, or regulated businesses to trust your white-label ActiveCampaign app, security cannot be “promised.” It must be proven through standards, controls, and audits.

Essential Certifications (What Matters in 2026)
ISO 27001 Compliance
Shows the provider follows a structured Information Security Management System (ISMS).
Best for: long-term security governance and enterprise trust.
SOC 2 Type II
Proves security controls work over time, not just on paper.
Best for: SaaS credibility and B2B onboarding.
GDPR Compliance
Required if you serve EU users or handle EU customer data.
Includes consent, lawful basis, retention, and deletion controls.
HIPAA (If Applicable)
Only required if your platform processes health-related data (rare for marketing apps).
But some healthcare marketers may demand it.
PCI DSS for Payments
If you process subscriptions, billing, or upgrades:
- you must use PCI-compliant payment gateways
- you must never store raw card data
Technical Requirements (Non-Negotiable Security Controls)
End-to-End Encryption
Minimum expectations:
- TLS 1.2+ for data in transit
- encryption at rest for databases and backups
Secure Authentication (2FA/OAuth)
Must include:
- strong password policies
- 2FA for admin and high-risk roles
- OAuth for integrations
- optional SSO for enterprise buyers
Regular Security Audits
A secure provider will offer:
- vulnerability scanning
- configuration reviews
- code security review
Penetration Testing
Pen testing validates real-world exploitability, especially for:
- admin panels
- API endpoints
- automation triggers
- file uploads
SSL Certificates
SSL is baseline, but the real requirement is:
- proper certificate management
- HSTS enforcement
- no mixed-content issues
Secure API Design
For ActiveCampaign-type platforms, APIs must include:
- authentication + scoped tokens
- rate limiting
- input validation
- logging and anomaly detection
Security Standards Comparison Table
| Standard / Control | What It Proves | Required For | Priority |
|---|---|---|---|
| ISO 27001 | Security management system | Enterprise clients | High |
| SOC 2 Type II | Controls work consistently | SaaS trust + partnerships | High |
| GDPR | Legal privacy compliance | EU data handling | High |
| PCI DSS | Payment safety | Subscriptions + billing | High |
| HIPAA | Healthcare data protection | Medical/health marketing | Medium |
| Penetration Testing | Real exploit resistance | Risk validation | High |
| 2FA + RBAC | Access control security | Admin + team safety | High |
| Encryption (Transit + Rest) | Data confidentiality | All apps | High |
Red Flags: How to Spot Unsafe White-Label Providers
If a provider cannot clearly explain their security controls, you should assume the risk will fall on you. In a white-label ActiveCampaign app, one weak vendor decision can expose thousands of contacts and destroy deliverability trust.
Warning Signs (High-Risk Red Flags)
No Security Documentation
If they cannot provide:
- security policy
- architecture overview
- data handling explanation
That is a serious risk.
Cheap Pricing Without Explanation
Low pricing often means:
- no audits
- weak infrastructure
- no monitoring
- no update policy
No Compliance Certifications
Even if they are “working on it,” the lack of proof is a risk for serious buyers.
Outdated Technology Stack
Old frameworks and unsupported libraries increase:
- vulnerability exposure
- patch delays
- compatibility failures
Poor Code Quality
Signs include:
- slow admin panels
- frequent bugs
- unstable automation flows
- missing error logs
No Security Updates Policy
If they do not commit to:
- patch timelines
- vulnerability response
- version upgrades
You will be exposed long-term.
Lack of Data Backup Systems
Without backups:
- ransomware becomes fatal
- accidental deletion becomes permanent
- recovery time becomes unpredictable
No Insurance Coverage
Serious providers should have:
- cyber liability coverage
- professional indemnity protection
This shows maturity and accountability.
Evaluation Checklist (Before You Sign Any Deal)
Questions to Ask Providers
- How do you store and encrypt contact data?
- Do you support 2FA for admins and users?
- What access control system do you use (RBAC)?
- How often do you run security audits and pen tests?
- What is your patching timeline for critical vulnerabilities?
- How do you secure APIs and integrations?
- What logging and monitoring is enabled by default?
- What is your incident response process?
Documents to Request
- security overview document
- data processing agreement (DPA)
- compliance proof (SOC 2, ISO, GDPR readiness)
- backup and disaster recovery plan
- penetration testing summary (at least executive report)
Testing Procedures You Should Perform
- request a staging demo with admin access
- run basic API security checks
- test login throttling and brute-force protection
- validate audit logs for admin actions
- check role permissions (least privilege)
Due Diligence Steps
- confirm where data is hosted (region + cloud provider)
- confirm who can access production databases
- confirm update frequency and support SLAs
- confirm ownership of code + exit plan
Read more : – Business Model of ActiveCampaign : Complete Strategy Breakdown 2025
Best Practices for Secure White-Label ActiveCampaign App Implementation
Even the most secure white-label ActiveCampaign app can become unsafe if implementation is rushed. Security is not just how the app is built, but how it is launched, configured, and maintained.
Pre-Launch Security (Must Do Before Going Live)
Security Audit Process
Before launch, verify:
- authentication flow security
- admin permission boundaries
- database access rules
- API endpoint protection
Code Review Requirements
A proper review should check:
- input validation
- secure session handling
- secrets management
- automation trigger abuse prevention
Infrastructure Hardening
Minimum baseline:
- firewall rules locked down
- WAF enabled
- database not publicly accessible
- private network setup for internal services
Compliance Verification
Confirm:
- GDPR consent flows exist
- privacy policy matches real data handling
- data retention rules are defined
- export/delete request process works
Staff Training Programs
Your internal team should know:
- phishing prevention
- admin account protection
- handling support requests safely
- incident escalation process
Post-Launch Monitoring (Security is Ongoing)
Continuous Security Monitoring
You should track:
- login anomalies
- suspicious exports
- unusual API traffic
- spam-like automation behavior
Regular Updates and Patches
Security updates must be:
- scheduled monthly (minimum)
- immediate for critical issues
- tested before production release
Incident Response Planning
You need a clear plan for:
- isolating affected systems
- rotating API keys and tokens
- notifying impacted users
- reporting to regulators if required
User Data Management
Implement:
- role-based data access
- export controls
- deletion workflows
- permission-based segmentation visibility
Backup and Recovery Systems
Backups must be:
- encrypted
- automated
- tested for restore
- stored in separate secure locations
Security Implementation Timeline (Practical Rollout)
| Phase | Timeline | What You Must Complete |
|---|---|---|
| Planning | Week 1 | risk review, compliance needs, security roles |
| Build Setup | Week 2 | RBAC, 2FA, encryption, secure infra baseline |
| Testing | Week 3 | pen testing, API testing, audit logs validation |
| Compliance | Week 4 | GDPR readiness, DPA, privacy policy alignment |
| Launch | Week 5 | monitoring, alerting, backups, incident plan |
| Ongoing | Monthly | patching, audits, access reviews, log analysis |
Legal & Compliance Considerations
A white-label ActiveCampaign app is not only a technology product. It is also a legal responsibility because you are handling customer data, communication logs, and automation actions that can impact privacy rights and business compliance.
Regulatory Requirements (What You Must Cover)
Data Protection Laws by Region
Key requirements depend on where your users are located:
- EU (GDPR): strict rules on consent, storage, and user rights
- UK (UK GDPR): similar to GDPR, separate enforcement
- USA (CCPA/CPRA + state laws): privacy rights, opt-outs, transparency
- India (DPDP Act): consent-based processing and data protection duties
- Middle East (varies): data residency expectations in some countries
Industry-Specific Regulations
Most marketing automation apps are general SaaS, but risk increases if you serve:
- healthcare businesses
- finance and lending businesses
- education platforms with minors
In such cases, additional compliance expectations may apply.
User Consent Management
Your app must support:
- consent capture (opt-in)
- unsubscribe controls
- lawful basis tracking where needed
- suppression list handling
This is critical because automation platforms can be abused if consent is weak.
Privacy Policy Requirements
Your privacy policy must clearly state:
- what data you collect
- why you collect it
- where it is stored
- how long it is retained
- who it is shared with (integrations)
- how users can request deletion/export
Terms of Service Essentials
Your terms should include:
- acceptable use policy (anti-spam rules)
- limitation of liability
- uptime and support expectations
- restrictions on abusive automation
- account termination rules for violations
Liability Protection (How to Reduce Business Risk)
Insurance Requirements
Strong businesses typically maintain:
- cyber liability insurance
- professional indemnity insurance
- errors and omissions coverage
This reduces financial damage if incidents happen.
Legal Disclaimers
You should clearly define:
- what your platform guarantees
- what the customer is responsible for
- what happens during service interruptions
User Agreements
Your onboarding should include:
- consent to data processing
- permission to send communications
- acknowledgment of anti-spam policies
Incident Reporting Protocols
You need a process for:
- internal escalation
- user notification
- regulator reporting (if required)
- documentation of actions taken
Regulatory Compliance Monitoring
Compliance is not “one-time.” You should review:
- privacy law updates
- security policy updates
- retention and deletion logs
- vendor and integration access
Compliance Checklist by Region (Quick Reference)
| Region | Key Compliance Focus | Must-Have Controls |
|---|---|---|
| EU | GDPR | consent, export/delete, DPA, breach reporting |
| UK | UK GDPR | similar to EU + local enforcement readiness |
| USA | CCPA/CPRA | opt-out, disclosure, data access requests |
| India | DPDP | consent tracking, breach response, secure storage |
| Global | Anti-spam rules | unsubscribe, suppression lists, abuse monitoring |
Why Miracuves White-Label ActiveCampaign App is Your Safest Choice
When you launch a white-label ActiveCampaign app, you are not only building a marketing platform. You are building a trust system. Clients will store their most valuable asset inside it: customer data. That’s why choosing a security-first provider is the smartest business decision.
Miracuves Security Advantages
Enterprise-Grade Security Architecture
Miracuves builds white-label ActiveCampaign apps with a security-first foundation:
- secure role-based access control
- strict admin permission boundaries
- protected APIs and token-based security
Regular Security Audits and Security Controls
Security is maintained through:
- periodic vulnerability assessments
- secure infrastructure reviews
- continuous improvement cycles
GDPR/CCPA Compliant by Default
Miracuves ensures your platform supports:
- consent management
- data export and deletion requests
- privacy-first data handling workflows
24/7 Monitoring Readiness
For production-grade deployments, monitoring focuses on:
- suspicious login activity
- automation abuse patterns
- unusual data exports
- API traffic anomalies
Encrypted Data Transmission
Your app includes:
- SSL/TLS encryption for all communication
- secure session handling
- protected API communication
Secure Payment Processing
If your app includes subscriptions or billing:
- PCI-aligned payment gateway integration
- no storage of sensitive card data
- secure billing workflows
Regular Security Updates
Miracuves follows a structured update approach:
- critical fixes prioritized
- patching cycles planned
- long-term maintainability supported
Insurance Coverage Included (Risk-First Mindset)
Miracuves operates with a risk-aware delivery model, helping businesses reduce exposure and improve accountability.
Final Thought
Don’t compromise on security. Miracuves white-label ActiveCampaign app solutions come with enterprise-grade security built-in. Our 600+ successful projects have maintained zero major security breaches. Get a free security assessment and see why businesses trust Miracuves for safe, compliant platforms.
A white-label ActiveCampaign app can be safe, scalable, and enterprise-ready in 2026, but only if security is treated as a core product feature, not an add-on. The real risk is not choosing white-label, the risk is choosing a provider who cannot prove security controls, compliance readiness, and long-term update support.
If you want to launch with confidence, build with a security-first team like Miracuves so your platform stays trusted, compliant, and protected as you grow.
FAQs
1. How secure is white-label vs custom development?
A white-label ActiveCampaign app can be as secure as custom development if it includes strong authentication, encryption, audits, and regular updates. Security depends on implementation quality, not the build type.
2. What happens if there’s a security breach?
You must isolate systems, secure access, investigate logs, notify affected users, and report to regulators if required. A clear incident response plan reduces damage and downtime.
3. Who is responsible for security updates?
The provider handles core app security patches, but your business is responsible for enforcing admin controls, access policies, and safe usage. Miracuves supports structured update cycles.
4. How is user data protected in white-label apps?
User data is protected using encryption in transit and at rest, role-based access, secure APIs, audit logs, and backup systems. These controls prevent leaks and unauthorized access.
5. What compliance certifications should I look for?
You should prioritize ISO 27001, SOC 2 Type II, GDPR readiness, and PCI DSS alignment if payments are involved. These are the strongest trust signals in 2026.
6. Can white-label apps meet enterprise security standards?
Yes, if the app includes 2FA, RBAC, monitoring, pen testing, secure infrastructure, and compliance controls. Enterprise security is achievable with the right provider.
7. How often should security audits be conducted?
At minimum, conduct vulnerability scans monthly and penetration testing yearly. High-growth platforms should audit more frequently, especially after major releases.
8. What’s included in Miracuves security package?
Miracuves provides secure architecture, encryption, strong authentication options, compliance-ready features, monitoring readiness, and ongoing security updates for safe operations.
9. How to handle security in different countries?
You must align with local privacy laws, support consent management, and follow data residency requirements where needed. A compliance checklist by region is essential.
10. What insurance is needed for app security?
Cyber liability insurance and professional indemnity coverage are recommended. Insurance helps protect your business financially if incidents occur.
Related Articles