You’ve heard the horror stories about data breaches, leaked user chats, stolen API keys, and AI apps exposing private customer data.
And if you’re planning to launch a white-label DeepSeek app, you’re probably asking the most important question first:
Is it actually safe?
In 2026, AI apps aren’t treated like “just another mobile app.” They process sensitive prompts, business documents, user identities, and sometimes payment data. One weak security decision can turn into a serious legal and reputation disaster.
This guide gives you an honest security assessment of white-label DeepSeek-style apps, the real risks, and the exact standards you must demand before launch.
And I’ll also show you how Miracuves approaches white-label AI apps with a security-first architecture, so you can scale confidently without gambling on safety.
Understanding White-Label DeepSeek App Security Landscape
What White-Label Security Actually Means
White-label app security means the underlying platform must be built with strong defenses even when the branding is customized. It is not just about interface — it’s about architecture.
Common Security Myths vs Reality
Many think white-label apps are inherently unsafe or “insecure by default.” The reality is that security depends on implementation, not label.
Why People Worry About White-Label Apps
Concerns come from lack of transparency, poorly documented architectures, and past breaches in lesser-quality offerings.
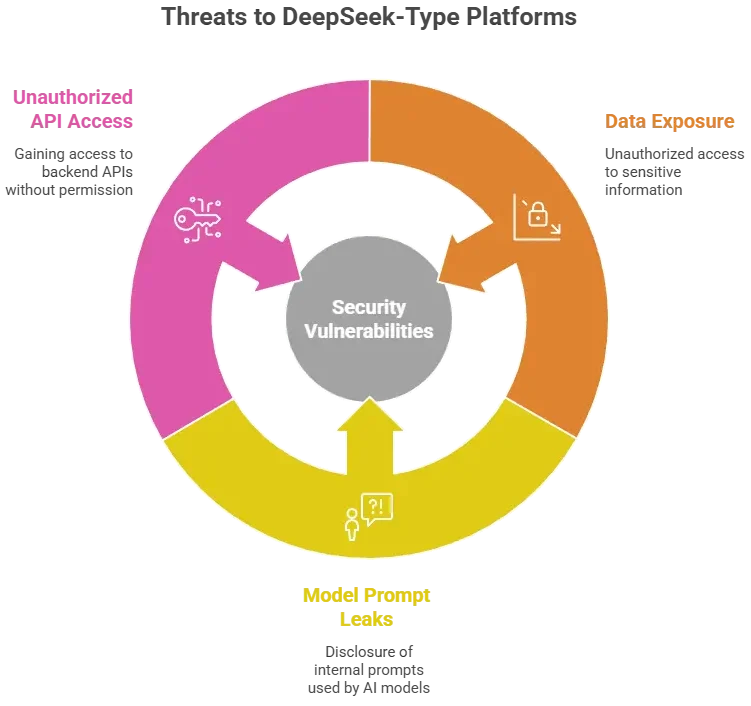
Security Standards in 2026
Expectations now include encrypted data flows, secure AI integrations, and strong authentication across all endpoints.
Real-World Statistics on App Security Incidents
Recent reports show a significant percentage of AI and SaaS apps experience some form of incident without proper safeguards.
Read more : – Business Model of DeepSeek : Complete Strategy Breakdown 2025
Key Security Risks & How to Identify Them
High-Risk Area 1: Data Protection and Privacy
User Personal Information
White-label DeepSeek apps handle names, emails, prompts, and sometimes business documents. Weak encryption or poor access control exposes this data.
Payment Data Security
If subscriptions or API credits are involved, insecure payment handling can lead to PCI violations and fraud.
Location and Usage Tracking
Analytics without proper anonymization can violate privacy laws.
GDPR and CCPA Compliance
Failure to manage consent, deletion requests, and data storage regions creates legal risk.
High-Risk Area 2: Technical Vulnerabilities
Code Quality Issues
Reused or outdated code increases exploit chances.
Server Security Gaps
Misconfigured cloud storage and open ports are common attack points.
API Vulnerabilities
Unprotected AI APIs allow abuse, data scraping, or prompt injection.
Third-Party Integrations
Each external service increases the attack surface.
High-Risk Area 3: Business Risks
Legal Liability
Data leaks can trigger lawsuits and regulatory action.
Reputation Damage
AI trust loss spreads fast and is hard to recover from.
Financial Losses
Downtime, fines, and compensation add up quickly.
Regulatory Penalties
Non-compliance can result in heavy fines in multiple regions.
Risk Assessment Checklist
• Is user data encrypted at rest and in transit
• Are AI APIs access-controlled
• Is compliance documented
• Are logs monitored in real time
• Are backups automated and secure
Security Standards Your White-Label DeepSeek App Must Meet
Essential Certifications
ISO 27001 Compliance
Ensures structured information security management and risk control.
SOC 2 Type II
Validates long-term security, availability, and confidentiality controls.
GDPR Compliance
Mandatory for handling EU user data, including consent and right-to-erasure.
HIPAA (If Applicable)
Required if the app processes healthcare or medical-related data.
PCI DSS for Payments
Essential for secure subscription billing and payment processing.
Technical Security Requirements
End-to-End Encryption
Protects user prompts, AI responses, and stored data.
Secure Authentication
OAuth, role-based access, and optional 2FA reduce unauthorized access.
Regular Security Audits
Identifies vulnerabilities before attackers do.
Penetration Testing
Simulated attacks to test real-world defenses.
SSL Certificates
Encrypts all data transfers between users and servers.
Secure API Design
Rate limiting, token validation, and access scopes are mandatory.
Security Standards Comparison Table
Basic providers often lack certifications, while enterprise-ready platforms follow ISO, SOC 2, and GDPR by default.
Red Flags: How to Spot Unsafe White-Label Providers
Warning Signs
No Security Documentation
If they can’t explain their security architecture clearly, assume it’s weak.
Cheap Pricing Without Explanation
Low pricing often means no audits, no compliance, and minimal monitoring.
No Compliance Certifications
A serious provider can show SOC 2, ISO 27001, or at least a compliance roadmap.
Outdated Technology Stack
Old frameworks and unpatched libraries are one of the biggest breach causes.
Poor Code Quality
Messy code means hidden vulnerabilities, weak authentication, and unstable APIs.
No Security Updates Policy
If updates are “optional,” your app will become insecure within months.
Lack of Data Backup Systems
No backups means one incident can permanently destroy your platform.
No Insurance Coverage
If they carry no cyber insurance, you may take full financial liability.

Read more : – DeepSeek Revenue Model: How DeepSeek Makes Money in 2026
Evaluation Checklist: What to Ask Providers
Questions to Ask
• How do you store and encrypt user prompts and responses
• Do you log admin access and user actions
• How do you handle API key security
• What is your incident response plan
Documents to Request
• SOC 2 report or ISO certificate
• Pen-test report (recent)
• Data processing agreement (DPA)
• Privacy policy templates
Testing Procedures
• Ask for a demo environment
• Test rate limits and login security
• Run basic vulnerability scans
Due Diligence Steps
• Verify compliance claims
• Review hosting region and data storage
• Confirm patch schedule and monitoring tools
Best Practices for Secure White-Label DeepSeek App Implementation
Pre-Launch Security Practices
Security Audit Process
Conduct a full audit covering infrastructure, APIs, and AI integrations before launch.
Code Review Requirements
Ensure all core modules and third-party libraries are reviewed and updated.
Infrastructure Hardening
Secure cloud configurations, firewalls, and access roles.
Compliance Verification
Confirm GDPR, CCPA, and regional compliance before onboarding users.
Staff Training Programs
Teams should understand data handling, access control, and incident response.
Post-Launch Security Monitoring
Continuous Security Monitoring
Real-time alerts help detect suspicious behavior early.
Regular Updates and Patches
AI apps require frequent security updates due to evolving threats.
Incident Response Planning
Clear procedures reduce damage during a breach.
User Data Management
Access controls and retention policies must be enforced.
Backup and Recovery Systems
Automated backups ensure fast recovery after incidents.
Security Implementation Timeline
Week 1–2: Audit and compliance checks
Week 3–4: Hardening and testing
Ongoing: Monitoring, updates, and audits
Legal and Compliance Considerations
Regulatory Requirements
Data Protection Laws by Region
EU requires GDPR compliance, the US follows CCPA and state-level laws, while other regions enforce local data residency rules.
Industry-Specific Regulations
Finance, healthcare, and enterprise AI usage may require additional controls.
User Consent Management
Clear opt-ins and consent logs are mandatory for data processing.
Privacy Policy Requirements
Policies must clearly explain data usage, storage, and deletion rights.
Terms of Service Essentials
Define acceptable use, AI limitations, and user responsibilities.
Liability Protection
Insurance Requirements
Cyber liability insurance protects against breach-related costs.
Legal Disclaimers
Limit responsibility for user-generated prompts and outputs.
User Agreements
Strong contracts reduce misuse and legal exposure.
Incident Reporting Protocols
Some regions require breach disclosure within 72 hours.
Regulatory Compliance Monitoring
Laws evolve, so compliance must be reviewed regularly.
Compliance Checklist by Region
EU: GDPR, DPA, breach reporting
US: CCPA, state privacy laws
Global: Data residency and consent tracking
Why Miracuves White-Label DeepSeek App is Your Safest Choice
Miracuves Security Advantages
Enterprise-Grade Security Architecture
Built with secure cloud infrastructure, role-based access, and hardened APIs.
Regular Security Audits and Certifications
Ongoing audits ensure alignment with ISO and SOC security standards.
GDPR and CCPA Compliant by Default
Privacy controls, consent management, and data deletion are built-in.
24/7 Security Monitoring
Continuous monitoring helps prevent breaches before impact.
Encrypted Data Transmission
All user prompts, responses, and metadata are encrypted.
Secure Payment Processing
PCI-compliant payment handling protects financial data.
Regular Security Updates
Proactive patching keeps the app protected against new threats.
Insurance Coverage Included
Cyber risk coverage reduces your financial exposure.
Final Thought
Don’t compromise on security. Miracuves white-label DeepSeek app solutions come with enterprise-grade protection built in. With 600+ successful projects and zero major security breaches, Miracuves helps you launch safe, compliant AI platforms.
Launching a white-label DeepSeek app in 2026 is not just a technical decision, it’s a trust decision. Security shortcuts may save money early, but they create long-term risk.
Choosing a provider that treats security as a foundation, not an add-on, protects your users, your brand, and your business future.
FAQs
1. How secure is white-label vs custom development
White-label apps can be equally secure if built with enterprise security standards and regular audits.
2. What happens if there is a security breach
A proper provider follows an incident response plan, user notification, and regulatory reporting timelines.
3. Who is responsible for security updates
The white-label app provider handles core security updates, while the business manages operational security.
4. How is user data protected
Data is encrypted, access-controlled, and stored according to regional compliance laws.
5. What compliance certifications should I look for
ISO 27001, SOC 2 Type II, GDPR, and PCI DSS are essential.
6. Can white-label apps meet enterprise security standards
Yes, when built with secure architecture, audits, and monitoring.
7. How often should security audits be conducted
At least once a year, with continuous monitoring in between.
8. What is included in Miracuves security package
Audits, compliance support, encrypted infrastructure, monitoring, and insurance coverage.
9. How to handle security in different countries
Use region-based data storage and follow local data protection laws.
10. What insurance is needed for app security
Cyber liability and data breach insurance are recommended.
Related Articles