You’ve heard the horror stories about data breaches, leaked medical records, ransomware attacks on hospitals, and healthcare platforms being shut down for non-compliance. When it comes to launching a white-label Practo app, these fears become even more real because you are not just handling user profiles—you are responsible for highly sensitive health data.
In 2025, healthcare apps face stricter regulations, higher cyber-attack volumes, and zero tolerance from users when it comes to privacy violations. A single security flaw can lead to massive financial penalties, permanent brand damage, and legal action across multiple jurisdictions.
This is why safety is not just a technical requirement anymore—it is the foundation of trust for any digital healthcare platform. A white-label Practo app must protect patient data, secure payment records, ensure doctor verification integrity, and fully comply with global healthcare regulations.
In this guide, you will get an honest, no-marketing-fluff assessment of how safe a white-label Practo app really is in 2025. We will break down real security risks, current compliance requirements, and the exact steps needed to build a secure platform. You will also learn how Miracuves positions security as a core architecture principle rather than an afterthought.
Understanding White-Label Practo App Security Landscape
When people talk about the security of a white-label Practo app, they are often referring to two different things at once: the security built into the base platform by the development provider, and the security maintained by the business owner after launch. True safety depends on both.
A white-label Practo app is a pre-built healthcare platform that is customized for branding and operations. While the core architecture is shared, real security depends on how the app is deployed, hosted, maintained, and governed. Security is not “automatic” just because the app is pre-built. It must be actively engineered, audited, and monitored.
What “White-Label Security” Actually Means
White-label security means that the foundational security framework is designed and implemented by the development provider before delivery. This includes:
- Secure application architecture
- Encrypted data storage and transmission
- Role-based access control for doctors, patients, and admins
- Secure payment and consultation systems
- Compliance-ready data handling workflows
However, the business owner still controls:
- Hosting environment
- User access policies
- Ongoing updates and patches
- Data retention and deletion policies
- Incident response procedures
A secure white-label Practo app is the result of both strong development practices and responsible operational management.
Why People Worry About White-Label Practo Apps
The concern around white-label Practo app security is driven by three major factors:
- High sensitivity of medical records
- Increasing frequency of healthcare cyberattacks
- Heavy regulatory penalties for non-compliance
Users are trusting the app with diagnosis history, prescriptions, lab reports, payment details, and location data. A single breach compromises not just privacy but patient safety and legal compliance.
Current Threat Landscape for Practo-Type Platforms in 2025
In 2025, digital healthcare platforms face some of the highest cyber risk levels across all industries. The most common threats include:
- Ransomware attacks on patient databases
- API breaches exposing appointment and prescription data
- Man-in-the-middle attacks during video consultations
- Credential stuffing attacks on doctor and admin panels
- Insider threats through misused access rights
- Third-party integrations leaking patient data
Healthcare platforms remain the most valuable target for cybercriminals because medical data sells for significantly more than financial data on illegal markets.
Security Standards in 2025 for Healthcare Apps
Modern healthcare platforms are expected to meet enterprise-grade security benchmarks, including:
- Zero-trust network architecture
- Encrypted databases using AES-256
- Encrypted data in transit using TLS 1.3
- Secure API gateways and rate limiting
- Continuous vulnerability scanning
- Role-based and least-privilege access policies
Security is now treated as a regulatory obligation, not a feature.
Real-World Statistics on App Security Incidents
Recent global security reports show:
- Healthcare remains the number one industry for data breaches by record volume
- Over 60 percent of healthcare breaches originate from misconfigured servers and APIs
- The average cost of a healthcare data breach now exceeds several million dollars per incident
- More than half of patients say they would permanently abandon a healthcare app after a single data leak
These numbers clearly explain why white-label Practo app security is now a board-level risk, not just a technical issue.
Key Security Risks & How to Identify Them
A white-label Practo app operates at the intersection of healthcare, finance, and personal identity. This makes it one of the highest-risk digital platforms to operate if security is not handled correctly. Understanding where the real dangers exist is the first step toward building a truly safe system.
Below are the highest-risk areas that every business owner must evaluate before and after launching a white-label Practo app.
Data Protection & Privacy Risks
Patient data is the most legally protected and financially valuable information in any app ecosystem. A single weakness here can trigger regulatory penalties, lawsuits, and permanent brand damage.
User personal information
This includes names, contact details, age, medical history, prescriptions, and reports. Risks arise when:
- Data is stored without encryption
- Access permissions are poorly configured
- Admin panels lack proper activity logging
- Backup systems are unsecured
Payment data security
Consultation fees, lab bookings, and subscriptions require strong financial security. Risks include:
- Weak payment gateway integration
- Lack of PCI DSS compliance
- Storing card data on local servers
- Insecure transaction APIs
Location tracking concerns
Real-time location data for clinics, doctors, and users can be exploited if not protected.
- Unencrypted GPS data can be intercepted
- Location history can be misused by insiders
- Poor data retention policies increase exposure
GDPR, CCPA, and healthcare data laws
Failure to comply can result in:
- Massive regulatory fines
- Forced shutdowns in certain regions
- Loss of investor and user confidence
Technical Vulnerabilities
Many security breaches happen because of basic technical issues that go unnoticed until attackers exploit them.
Code quality issues
- Hard-coded credentials in source code
- Poor input validation
- Lack of secure coding standards
- Inadequate error handling revealing system details
Server security gaps
- Open ports and unsecured services
- Weak firewall rules
- Lack of intrusion detection systems
- Unpatched operating systems
API vulnerabilities
- No API authentication layers
- Missing rate limiting
- Exposed endpoints returning sensitive data
- Insecure webhooks with third-party services
Third-party integrations
- Diagnostic tools
- Video consultation services
- Payment providers
- Marketing automation platforms
Every integration becomes a potential entry point if not vetted and secured.
Business Risks
Security failures create consequences far beyond technical damage.
Legal liability
Business owners remain legally responsible for:
- Patient data leaks
- Unauthorized data transfers
- Consent violations
- Medical data mishandling
Reputation damage
Healthcare trust is fragile. Even minor incidents can:
- Destroy user confidence
- Trigger negative media coverage
- Lead to mass user churn
- Block future partnerships
Financial losses
Security incidents result in:
- Regulatory fines
- Legal expenses
- Compensation payouts
- Lost revenue from downtime
- Increased cyber insurance premiums
Regulatory penalties
Regulators now actively monitor digital health platforms. Penalties may include:
- Per-user data violation fines
- Mandatory operational audits
- Temporary or permanent regional bans
Risk Assessment Checklist for a White-Label Practo App
Use the following checklist to immediately assess your exposure:
- Is all patient data encrypted at rest and in transit
- Are doctor and admin logins protected with multi-factor authentication
- Are API requests authenticated and rate-limited
- Is payment processing PCI DSS compliant
- Are access logs monitored daily
- Are vulnerability scans conducted regularly
- Are server patches applied automatically
- Is there a documented data breach response plan
- Is your platform compliant with regional healthcare data laws
- Is cyber insurance in place
If multiple answers are no or unknown, your white-label Practo app is operating at high risk.
Read more : – Practo Feature Breakdown: What Startups Can Learn
Security Standards Your White-Label Practo App Must Meet
For a white-label Practo app to be considered truly secure in 2025, it must meet strict global security and healthcare compliance standards. These are not optional enhancements anymore. They are minimum operational requirements for running any legitimate digital healthcare platform.
Failing to meet these standards can result in legal shutdowns, blocked payment processing, app store removal, and massive financial penalties.
Essential Certifications for a Secure White-Label Practo App
ISO 27001 Compliance
This is the global standard for information security management. It ensures that the platform follows a structured system for:
- Risk assessment and mitigation
- Data protection governance
- Incident handling processes
- Continuous security improvement
SOC 2 Type II
This certification validates how your app handles:
- Security
- Availability
- Processing integrity
- Confidentiality
- Privacy
SOC 2 Type II is especially important for investor trust and enterprise hospital partnerships.
GDPR Compliance
Mandatory for any app serving users in the European Union. It controls:
- How patient data is collected
- How consent is recorded
- How data is stored and deleted
- How breaches are reported within strict timelines
CCPA Compliance
Required for serving users in California and increasingly followed as a global best practice. It ensures:
- User rights over personal data
- Transparency in data usage
- Protection against unauthorized data selling
HIPAA Compliance (If Applicable)
For apps operating in or serving the U.S. healthcare ecosystem, HIPAA governs:
- Electronic health information protection
- Secure access controls
- Audit trails for data access
- Breach notification standards
PCI DSS for Payments
Any white-label Practo app that processes card payments must comply with PCI DSS to protect:
- Cardholder data
- Transaction processing
- Payment API security
- Fraud detection mechanisms
Technical Security Requirements in 2025
A secure white-label Practo app must be built on modern security engineering principles.
End-to-End Encryption
- All patient data must be encrypted during transmission and storage
- AES-256 for data at rest
- TLS 1.3 for data in transit
Secure Authentication Systems
- Two-factor authentication for doctors and admins
- OAuth-based secure login flows
- Session expiration and device verification
Regular Security Audits
- Quarterly vulnerability assessments
- Annual third-party security certifications
- Continuous penetration testing
Penetration Testing
- Simulated cyberattacks on the app infrastructure
- API security testing
- Admin panel exploit validation
- Database compromise simulation
SSL Certificates
- Mandatory HTTPS across all app services
- Automatic certificate renewals
- Enforced secure transport policies
Secure API Design
- Token-based authentication
- Rate limiting
- Input validation
- Encrypted API payloads
- Zero trust access control
Security Standards Comparison Table
| Security Area | Minimum Requirement | Enterprise-Grade Requirement | Miracuves Standard |
|---|---|---|---|
| Data Encryption | SSL + basic encryption | AES-256 + TLS 1.3 | AES-256 + TLS 1.3 by default |
| Authentication | Password-based login | 2FA + OAuth | Multi-factor + OAuth |
| Compliance | Basic GDPR | GDPR + CCPA + HIPAA ready | Full multi-region compliance |
| Payment Security | Standard gateway integration | PCI DSS certified | PCI DSS certified |
| Vulnerability Scans | Annual | Continuous | Real-time monitoring |
| Penetration Testing | Optional | Quarterly | Scheduled quarterly |
| Audit Trails | Basic logs | Tamper-proof audit logs | Advanced forensic logging |
In 2025, regulators, investors, and enterprise healthcare partners expect white-label Practo apps to meet enterprise-grade security controls from day one. Anything less is considered high operational risk.
Red Flags: How to Spot Unsafe White-Label Providers
Choosing the wrong development partner is one of the biggest security risks for any white-label Practo app. Many platforms fail not because the business idea is weak, but because security was compromised at the foundation level by an unreliable provider. In 2025, unsafe white-label providers can expose you to regulatory shutdowns, financial penalties, and irreversible brand damage.
Understanding these red flags before signing any agreement can protect your entire investment.

No compliance certifications
If the provider has:
- No ISO 27001
- No SOC 2 reports
- No documented GDPR processes
Then the platform is not compliance-ready for regulated healthcare operations.
Outdated technology stack
Security vulnerabilities increase rapidly when:
- Legacy frameworks are used
- Unmaintained libraries are retained
- No automated patching exists
Poor code quality
Indicators include:
- Frequent bugs after deployment
- Crashing admin panels
- Inconsistent user permissions
- Direct database access used instead of secure APIs
No security updates policy
A safe white-label Practo app must receive:
- Regular vulnerability patches
- Dependency updates
- Server security upgrades
- Compliance-driven revisions
No data backup systems
Without reliable backups:
- Ransomware attacks can permanently destroy data
- System failures can cause irreversible loss
- Legal data retention rules cannot be met
No insurance coverage
Professional providers carry:
- Cyber liability insurance
- Data breach insurance
- Professional indemnity coverage
The absence of insurance exposes you to full financial liability during a security incident.
Evaluation Checklist Before Selecting a White-Label Provider
Questions to ask providers
- What encryption standards are used for patient data
- How often are security audits conducted
- Do you provide penetration testing reports
- How is admin access controlled
- What is your incident response process
- How quickly are security vulnerabilities patched
- Are your payment modules PCI DSS certified
- What regional data protection laws are supported
Documents to request
- ISO 27001 certification
- SOC 2 Type II report
- GDPR compliance declaration
- Data processing agreement
- Penetration testing summary
- Infrastructure security architecture
- Disaster recovery and backup policy
Testing procedures
Before final deployment:
- Conduct independent vulnerability assessments
- Perform API security validation
- Test role-based access controls
- Verify encryption during data transmission
- Simulate payment fraud scenarios
Due diligence steps
- Validate previous healthcare clients
- Review breach history
- Test live demo systems for vulnerabilities
- Confirm cloud infrastructure compliance
- Verify insurance certificates
Skipping these validation steps is the most common reason businesses unknowingly launch unsafe healthcare platforms.
Best Practices for Secure White-Label Practo App Implementation
A secure white-label Practo app is not created by software alone. It is the result of disciplined security planning before launch and continuous monitoring after deployment. Many healthcare app breaches happen not because the core system is broken, but because implementation and operations are careless.
Below are the best-practice security controls every serious healthcare platform must follow in 2025.
Pre-Launch Security Controls
Security audit process
Before going live, the full app infrastructure must go through:
- Source code security review
- Server configuration audits
- Database encryption verification
- API security testing
- Access control validation
This audit ensures that no default credentials, insecure endpoints, or misconfigured storage systems exist at launch.
Code review requirements
Every production build must be validated for:
- Secure input validation
- Protection against SQL injection and XSS
- Secure authentication flow enforcement
- Proper session and token handling
Independent security engineers should always validate healthcare app code before public access.
Infrastructure hardening
The hosting environment must be secured using:
- Firewall configuration and port restrictions
- Intrusion detection and prevention systems
- Isolated production and staging servers
- Secure containerization and workload isolation
Unhardened infrastructure remains one of the top causes of healthcare data breaches worldwide.
Compliance verification
Before launch, full verification must be completed for:
- GDPR data handling workflows
- Regional health data retention laws
- Consent management systems
- Breach notification protocols
- Right-to-delete and data portability features
Staff training programs
Human error remains a leading cause of security incidents. All staff with system access must undergo:
- Data handling compliance training
- Secure password and access management training
- Phishing and social engineering awareness
- Incident reporting procedures
Post-Launch Security Monitoring
Continuous security monitoring
A white-label Practo app must operate with:
- Real-time intrusion detection
- Automated threat monitoring
- Suspicious login behavior alerts
- API abuse detection
Security is no longer periodic. It is a continuous real-time responsibility.
Regular updates and patches
Post-launch security depends on:
- Timely operating system updates
- Dependency library upgrades
- Emergency vulnerability patches
- Payment module security updates
Delayed updates are one of the most common breach triggers in healthcare apps.
Incident response planning
Every platform must have:
- A documented data breach response plan
- Legal notification timelines
- Customer communication workflows
- Law enforcement escalation protocols
- Insurance claim activation procedures
Without this plan, even a minor security incident can spiral into a regulatory crisis.
User data management
Secure operations require:
- Encrypted backup storage
- Controlled retention limits
- Automated data deletion workflows
- Restricted internal access policies
Poor data lifecycle management increases both security exposure and legal liability.
Backup and recovery systems
A reliable healthcare platform must maintain:
- Automated daily encrypted backups
- Multi-region disaster recovery infrastructure
- Routine restore testing
- Guaranteed recovery time objectives
Backups protect your business against ransomware, system failures, and catastrophic data loss.
Security Implementation Timeline for a White-Label Practo App
Week 1
- Infrastructure provisioning
- Security architecture setup
- Encryption implementation
- Access control configuration
Week 2
- Compliance verification
- Third-party security audit
- Penetration testing
- Payment security validation
Launch Phase
- Live security monitoring activation
- Backup automation setup
- Incident response readiness
- Staff access policy enforcement
Ongoing Operations
- Monthly vulnerability scans
- Quarterly penetration testing
- Continuous log monitoring
- Annual compliance recertification
In 2025, security is not a launch task. It is a permanent operational discipline that determines whether your healthcare platform survives in the long term.
Legal & Compliance Considerations
Operating a white-label Practo app means you are legally responsible for protecting medical data, enforcing patient privacy rights, and complying with regional healthcare and data protection laws. Unlike entertainment or e-commerce platforms, healthcare apps face direct legal exposure for every record they store or transmit.
In 2025, regulators are actively monitoring digital health platforms. Non-compliance is no longer met with warnings – it results in fines, bans, and criminal liability in severe cases.
Regulatory Requirements by Region
India
Operating a healthcare app in India requires compliance with:
- Digital Personal Data Protection Act (DPDPA) 2023
- IT Act 2000 and IT Rules for data security
- Health Data Management Policy under National Digital Health Mission
- Consent-based data processing for medical records
- Mandatory breach reporting to authorities
European Union
For any users in the EU, your white-label Practo app must comply with:
- GDPR for personal and medical data protection
- Explicit consent for health data processing
- Right to access, correction, portability, and deletion
- Mandatory breach reporting within 72 hours
- Heavy per-user penalty structure for violations
United States
If your app serves U.S. users or healthcare providers:
- HIPAA compliance for protected health information
- HITECH Act breach notification requirements
- Secure audit trails for all medical data access
- Enforced business associate agreements
Middle East and Asia-Pacific
Many regions now follow GDPR-style health data laws:
- Local data residency requirements
- National cyber security frameworks
- Government-approved cloud infrastructure mandates
- Mandatory user consent and transparency rules
Industry-Specific Regulations
A white-label Practo app must also comply with:
- Telemedicine practice guidelines
- Electronic health record handling laws
- Online prescription standards
- Medical consultation archiving rules
- Clinical responsibility delegation principles
These regulations differ by country but apply equally to digital platforms as they do to physical healthcare institutions.
User Consent Management
Every compliant white-label Practo app must enforce:
- Explicit opt-in consent for medical data processing
- Separate consent for marketing communication
- Clear consent withdrawal mechanisms
- Transparent data usage disclosures
- Logged consent records for audits
Silent consent or hidden approvals are now considered unlawful in most regulated regions.
Privacy Policy Requirements
Your privacy policy must clearly disclose:
- What personal and medical data is collected
- How the data is stored and encrypted
- Who can access the data
- How long the data is retained
- How users can request deletion
- How breaches will be communicated
Regulators now actively audit privacy policies against real operational behavior.
Terms of Service Essentials
Legal protection depends on clearly defined:
- User responsibilities and limitations
- Medical liability disclaimers
- Platform usage boundaries
- Data ownership definitions
- Dispute resolution mechanisms
- Jurisdiction and governing law clauses
Weak or copied legal documents expose your platform to lawsuits.
Liability Protection Measures
Insurance requirements
Every serious healthcare platform should carry:
- Cyber liability insurance
- Data breach insurance
- Professional indemnity insurance
- Errors and omissions coverage
These policies protect your business from multimillion-dollar damage claims.
Legal disclaimers
Your app must clearly define:
- That the platform facilitates consultations
- That medical decisions remain between patient and doctor
- That emergency cases require immediate medical attention outside the app
User agreements
All users must explicitly agree to:
- Data usage rules
- Consultation limitations
- Payment policies
- Refund and cancellation terms
Incident reporting protocols
A fully compliant white-label Practo app must maintain:
- Internal breach logging
- Regulatory authority notification workflows
- User notification timelines
- Forensic investigation documentation
Regulatory compliance monitoring
Compliance is not static. Your platform must:
- Track changes in health data laws
- Apply ongoing legal updates
- Conduct periodic compliance audits
Compliance Checklist by Region
- Patient data encrypted at rest and in transit
- Explicit and logged user consent
- Regional data storage laws followed
- Breach notification procedures documented
- HIPAA and GDPR readiness verified
- Privacy policy aligned with operations
- Terms of service legally reviewed
- Insurance coverage active and validated
Failure in any of these areas can trigger regulatory investigation, service suspension, and long-term legal exposure.
Why Miracuves White-Label Practo App Is Your Safest Choice
Choosing the right technology partner is the single most important security decision you will make for your healthcare business. Even the best business model fails if the platform is not built on a hardened, compliant, and continuously monitored security foundation. Miracuves approaches white-label Practo app security as a core architecture principle, not a feature added later.
While many providers focus on fast delivery and low pricing, Miracuves follows a security-first engineering approach that aligns with global healthcare compliance standards from day one.
Miracuves Security Advantages
Enterprise-grade security architecture
Miracuves platforms are designed on enterprise security frameworks with layered protection across the application, server, database, and network levels. This architecture ensures that even if one layer is compromised, multiple independent defenses remain active.
Regular security audits and certifications
Miracuves conducts:
- Scheduled internal security audits
- Third-party vulnerability assessments
- Periodic penetration testing
- Infrastructure compliance verification
This continuous validation keeps your white-label Practo app aligned with evolving cyber threats.
GDPR and CCPA compliant by default
Every Miracuves healthcare app is built with:
- Explicit user consent management
- Right-to-access and right-to-delete workflows
- Secure data retention policies
- Transparent privacy controls
This ensures legal readiness for multi-region operations without expensive retrofitting.
24/7 security monitoring
Miracuves platforms operate with:
- Real-time intrusion detection
- Suspicious access alerts
- API abuse monitoring
- Automated threat response systems
Security incidents are detected and contained before they escalate into large-scale breaches.
Encrypted data transmission
All patient data, prescriptions, reports, and consultation records are protected with:
- AES-256 encryption for data at rest
- TLS 1.3 encryption for data in transit
- Secure key management policies
This ensures confidentiality across all user interactions.
Secure payment processing
Miracuves integrates:
- PCI DSS-compliant payment gateways
- Tokenized transaction handling
- Fraud detection systems
- Encrypted financial data workflows
This protects both your revenue and your users’ financial information.
Regular security updates
Miracuves provides:
- Automated dependency updates
- Emergency vulnerability patching
- Framework security upgrades
- Server hardening revisions
You are never left operating on outdated or exposed systems.
Insurance coverage included
Miracuves maintains:
- Professional indemnity insurance
- Cyber liability protection
- Data breach response coverage
This adds an additional financial safety net for your platform in the event of a major security incident.
Read more : – How to Hire the Best Practo Clone Developer
Conclusion
Do not compromise on security. Miracuves white-label Practo app solutions come with enterprise-grade security built into the core architecture. With over 600 successful healthcare and enterprise platforms delivered and zero major security breaches across live client systems, Miracuves is trusted by businesses that cannot afford regulatory or reputational risk. Get a free security assessment and see why organizations rely on Miracuves for building safe, compliant healthcare platforms.
A white-label Practo app can be just as secure as any enterprise-grade healthcare platform—if it is built on the right security architecture, maintained with continuous vigilance, and backed by full legal compliance. In 2025, security is not a technical add-on; it is the foundation of trust, growth, and long-term survival in digital healthcare. Choosing a security-first provider like Miracuves is not a cost decision—it is a business protection strategy.
FAQs
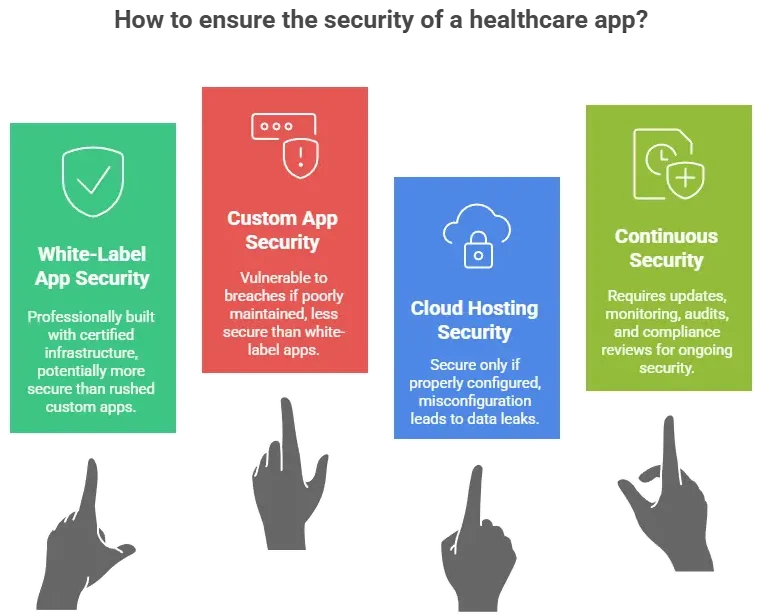
How secure is white-label vs custom development?
A professionally built white-label Practo app with certified infrastructure, audits, and compliance is often more secure than rushed custom development with unverified security practices.
What happens if there is a security breach?
An incident response plan is activated, affected systems are isolated, regulators are notified within legal timelines, users are informed, and forensic investigation is conducted to prevent recurrence.
Who is responsible for security updates?
Primary responsibility lies with the provider for core platform updates, while the business owner manages hosting, access control, and operational security policies.
How is user data protected in a white-label Practo app?
Data is protected using AES-256 encryption at rest, TLS 1.3 in transit, role-based access control, and continuous monitoring of all system activities.
What compliance certifications should I look for?
ISO 27001, SOC 2 Type II, GDPR compliance, HIPAA readiness where applicable, and PCI DSS for payment security.
Can a white-label Practo app meet enterprise security standards?
Yes, if it is built using enterprise-grade architecture, audited regularly, and operated under strict compliance governance.
How often should security audits be conducted?
Vulnerability scans should run continuously, penetration testing quarterly, and full compliance audits annually.
What is included in Miracuves security package?
Enterprise security architecture, encryption, compliance-ready workflows, continuous monitoring, regular audits, secure payment processing, and insurance-backed protection.
How to handle security in different countries?
By implementing region-specific data hosting, consent workflows, cross-border data transfer safeguards, and local regulatory compliance monitoring.
What insurance is needed for app security?
Cyber liability insurance, data breach insurance, professional indemnity, and errors and omissions coverage.
Related Articles: