You have probably heard the horror stories about data breaches, leaked customer information, hacked payment systems, and food delivery apps being taken offline overnight. When you invest in a white-label Zomato app, the first question that quietly worries every founder is simple — is my app actually safe?
In 2025, app security is no longer just a technical concern. It is a business survival factor. With rising cybercrime, stricter data protection laws, and customers becoming increasingly privacy-conscious, one serious security failure can permanently destroy user trust, brand reputation, and legal standing.
Food delivery platforms handle extremely sensitive data every minute — customer names, phone numbers, live locations, order history, and online payments. That makes a white-label Zomato app a prime target for cyberattacks if security is not built correctly from day one.
This guide provides an honest, practical assessment of white-label Zomato app security in 2025 — what the real risks are, what safety standards truly matter, and how you can confidently protect your users, revenue, and brand with the right security-first approach.
You will also see how enterprise-grade providers like Miracuves eliminate these risks through built-in compliance, hardened infrastructure, and continuous monitoring.
Understanding White-Label Zomato App Security Landscape
What “White-Label Zomato App Security” Actually Means
White-label Zomato app security refers to the complete set of technical, legal, and operational safeguards built into a pre-developed food delivery platform that is rebranded and deployed for your business. Unlike custom-built apps where security is designed from scratch, a white-label Zomato app relies on the provider’s existing infrastructure, codebase, hosting environment, and compliance framework. Your safety directly depends on how professionally that foundation has been engineered and maintained.
Security here is not limited to preventing hacking. It includes:
- How user data is collected, stored, and transmitted
- How payments are processed
- How restaurant and delivery partner information is protected
- How system access is controlled
- How fast vulnerabilities are detected and patched
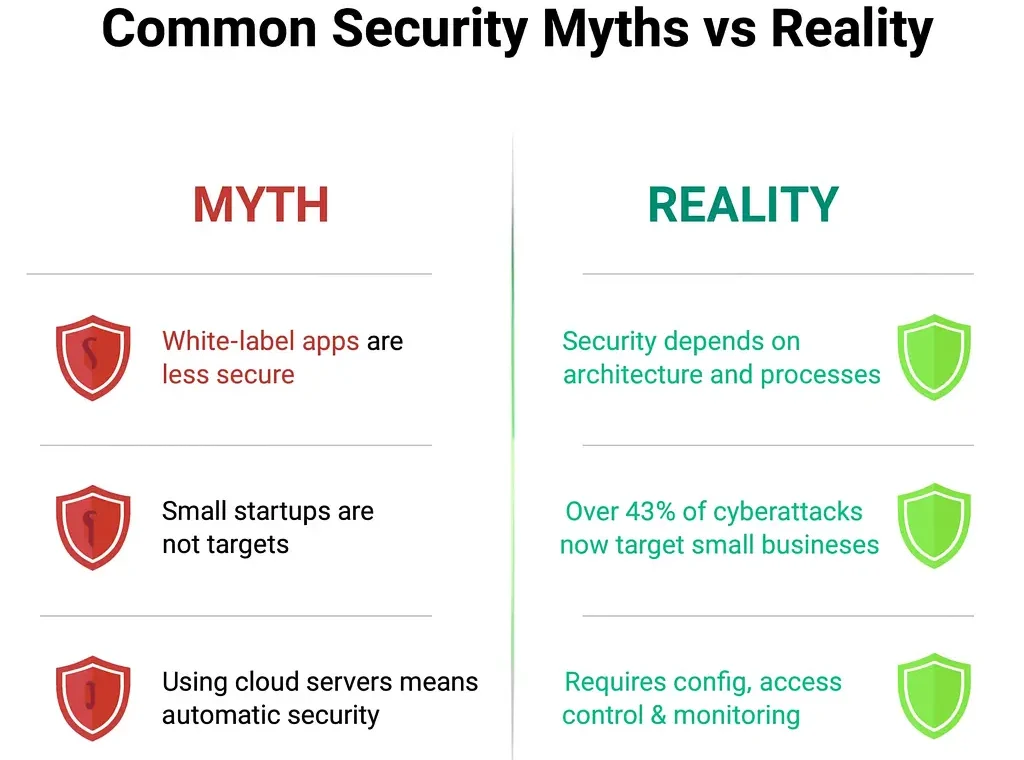
Why People Worry About White-Label Apps
Entrepreneurs worry about white-label Zomato apps mainly because:
- They do not directly control the source code
- They rely on third-party hosting and APIs
- They handle real-money transactions
- They store high-risk personal and location data
- They operate under strict regulatory frameworks
These fears are valid because a single weak link, such as an exposed API or insecure database configuration, can compromise the entire platform.
Current Threat Landscape for Food Delivery Apps in 2025
In 2025, food delivery apps face increasingly advanced cyber threats. The most common attack vectors include:
- API exploitation to steal order and user data
- Credential stuffing attacks on user accounts
- Payment gateway interception attacks
- Fake restaurant onboarding for fraud
- Location data harvesting
- DDoS attacks during peak ordering hours
- Ransomware targeting backend servers
Cybercriminals focus heavily on food delivery platforms because they combine financial data, behavioral data, and real-time location intelligence in a single ecosystem.
Security Standards in 2025 for White-Label Food Delivery Apps
Modern white-label Zomato apps must align with updated global security norms such as:
- Zero-trust security architecture
- Mandatory encryption for data at rest and in transit
- Multi-factor authentication for users and admin panels
- Secure DevOps (DevSecOps) pipelines
- Continuous vulnerability scanning
- AI-based fraud detection systems
Security is no longer a one-time setup. It is an ongoing operational discipline.
Real-World Statistics on App Security Incidents
Recent global cybersecurity reports show that:
- Over 62 percent of mobile app breaches in 2024 involved APIs
- Food and retail delivery platforms are among the top five most targeted sectors
- More than 40 percent of attacks exploited misconfigured cloud servers
- Data breach recovery costs now average several million dollars per incident
- Nearly 70 percent of users abandon an app permanently after a serious data breach
These numbers highlight that white-label Zomato app security is not a theoretical concern. It is a financially measurable business risk.
Key Security Risks & How to Identify Them
A white-label Zomato app operates at the intersection of payments, personal data, real-time logistics, and multi-party access. This makes its risk surface significantly broader than most standard mobile apps. Understanding where the real dangers lie is the first step toward preventing costly failures.
Data Protection & Privacy Risks
User Personal Information
Food delivery apps collect names, phone numbers, email addresses, home addresses, and order histories. If databases are not properly encrypted or access-controlled:
- Hackers can extract bulk customer data
- Users become victims of identity theft and spam
- Your business becomes legally liable for data exposure
Payment Data Security
Payment data is the most targeted asset in a Zomato-style app.
- Card numbers, UPI details, and transaction tokens must never be stored in raw form
- Improper payment gateway integration can expose financial credentials
- Non-compliance with PCI DSS can lead to heavy fines and permanent payment gateway bans
Location Tracking Concerns
Live location tracking is essential for deliveries but extremely sensitive.
- Continuous tracking creates privacy risks if data is logged improperly
- Location leaks can lead to stalking, theft, and personal safety threats
- Many breaches now involve historical location data misuse
GDPR and CCPA Compliance Failures
If your white-label Zomato app serves users in the EU or California:
- Improper consent management violates GDPR and CCPA
- Lack of data deletion mechanisms exposes you to regulatory penalties
- Data processing without legal basis can result in operational shutdowns
Technical Vulnerabilities
Code Quality Issues
Low-quality or reused code often contains:
- Hard-coded credentials
- SQL injection vulnerabilities
- Insecure file uploads
- Weak authentication logic
These weaknesses are frequently exploited within weeks of public launch.
Server Security Gaps
Common backend weaknesses include:
- Open database ports
- Weak firewall rules
- Outdated operating systems
- Poor cloud permission controls
Misconfigured servers remain one of the largest causes of app data breaches globally.
API Vulnerabilities
APIs power user apps, delivery partner apps, restaurant dashboards, and admin panels.
- Excessive API permissions expose whole systems
- Missing rate limits allow data scraping attacks
- Improper token validation enables account takeovers
Third-Party Integrations
White-label Zomato apps depend on multiple external services:
- Payment gateways
- Mapping services
- SMS and notification providers
- Analytics platforms
Each third-party integration increases the overall attack surface if not vetted properly.
Business Risks
Legal Liability
A single data breach can trigger:
- Consumer lawsuits
- Regulatory investigations
- Contract termination by payment gateways and restaurant partners
Reputation Damage
Food delivery is a trust-driven business.
- One breach can permanently destroy your brand credibility
- Negative press travels faster than customer acquisition efforts
Financial Losses
Direct and indirect losses include:
- Regulatory fines
- Compensation to affected users
- Infrastructure recovery costs
- Lost revenue from suspended operations
Regulatory Penalties
Non-compliance with data protection laws can result in:
- Multi-million-dollar fines
- Forced platform shutdowns
- Criminal accountability in certain jurisdictions
Risk Assessment Checklist
Use this checklist to identify whether your white-label Zomato app is exposed to high-risk vulnerabilities:
- Is all user and payment data encrypted both at rest and in transit
- Are API endpoints protected with proper authentication and rate limits
- Is two-factor authentication enabled for admin access
- Are servers regularly patched and monitored
- Is GDPR and CCPA compliance implemented with proper consent logs
- Are third-party services security-audited
- Is regular penetration testing conducted
- Is there a documented incident response plan
- Are daily automated backups in place
- Is access to production systems strictly role-based
If even a few of these checks fail, your app is operating under elevated security risk.
Security Standards Your White-Label Zomato App Must Meet
Security in 2025 is no longer optional or “best effort.” Regulatory authorities, payment networks, cloud providers, and users now expect food delivery platforms to meet strict, verifiable security standards. A white-label Zomato app that fails to meet these benchmarks is exposed to legal shutdowns, payment bans, and permanent reputational damage.
Essential Certifications
ISO 27001 Compliance
ISO 27001 is the global benchmark for Information Security Management Systems (ISMS). It confirms that:
- All data handling processes are formally documented
- Risk assessments are continuously performed
- Access controls are enforced across infrastructure
- Incident response procedures are tested and audited
A white-label Zomato app without ISO 27001 certification lacks enterprise-grade governance.
SOC 2 Type II
SOC 2 Type II certification verifies long-term operational security across:
- Data confidentiality
- System availability
- Processing integrity
- Privacy safeguards
This standard proves that security is not just designed but actively maintained over time.
GDPR Compliance
GDPR is mandatory for any app serving European users. It requires:
- Explicit user consent for data collection
- Right to access and delete user data
- Clear legal basis for all data processing
- Breach notification within strict time limits
Non-compliance can result in fines up to 4 percent of global annual revenue.
HIPAA (If Applicable)
If your white-label Zomato app handles any medical food orders, hospital deliveries, or health-related data, HIPAA becomes applicable. It mandates:
- Strict access controls
- Detailed audit trails
- Encrypted health data storage
PCI DSS for Payments
PCI DSS is mandatory for all platforms processing card payments. It ensures:
- Secure storage of payment tokens
- Network segmentation for financial systems
- Continuous vulnerability scanning
- Restricted access to payment data
Without PCI DSS compliance, payment gateways can terminate your account immediately.
Technical Security Requirements
End-to-End Encryption
All sensitive data must be encrypted:
- TLS 1.3 encryption for data in transit
- AES-256 encryption for data at rest
- Encrypted backups and logs
This prevents interception even if network traffic is compromised.
Secure Authentication (2FA and OAuth)
Modern white-label Zomato apps must implement:
- Two-factor authentication for admins and restaurant partners
- OAuth-based secure login mechanisms
- Token expiration and refresh policies
This significantly reduces account takeover risks.
Regular Security Audits
Security audits must be conducted:
- Before launch
- After every major update
- At fixed quarterly or bi-annual intervals
Audits detect vulnerabilities before attackers do.
Penetration Testing
Professional ethical hackers simulate real-world attacks to:
- Identify exploitable vulnerabilities
- Test API security
- Validate firewall effectiveness
- Challenge authentication workflows
Penetration testing is now a regulatory expectation, not an optional practice.
SSL Certificates
All domains, subdomains, APIs, and dashboards must use:
- Valid SSL certificates
- Auto-renewal systems
- HSTS enforcement
Any unsecured endpoint becomes an instant breach entry point.
Secure API Design
APIs must follow:
- Token-based authentication
- Strict input validation
- Role-based access control
- Rate limiting and throttling
- IP whitelisting for sensitive routes
Weak APIs remain one of the top causes of food delivery app breaches.
Security Standards Comparison Table
| Security Standard | Mandatory for Food Apps | Purpose | Risk If Missing |
|---|---|---|---|
| ISO 27001 | Yes | Overall security governance | Weak internal controls |
| SOC 2 Type II | Highly Recommended | Long-term operational security | Investor and enterprise trust loss |
| GDPR | Yes (EU users) | Data protection and privacy | Heavy regulatory fines |
| HIPAA | Conditional | Health data protection | Legal prosecution |
| PCI DSS | Yes | Secure payment processing | Payment gateway suspension |
| TLS 1.3 Encryption | Yes | Secure data transmission | Data interception attacks |
| 2FA & OAuth | Yes | Identity protection | Account takeover |
| Penetration Testing | Yes | Vulnerability detection | Undetected security flaws |
Failing to meet even one of these standards creates a legal, technical, and financial vulnerability that can destabilize your entire white-label Zomato app operation.
Read more : – How to Develop a Food Delivery App Like Zomato: Features, Costs, and Timeline
Red Flags: How to Spot Unsafe White-Label Providers
Choosing the wrong white-label Zomato app provider is one of the most dangerous mistakes a founder can make. Many platforms look attractive on the surface but hide serious security weaknesses underneath. Recognizing early warning signs can save you from legal trouble, financial loss, and brand destruction.
Major Warning Signs of an Unsafe White-Label Provider
No Security Documentation
If a provider cannot share clear security policies, audit reports, or compliance documentation, it indicates:
- No structured security framework
- No accountability in case of breach
- High operational risk
Professional providers always maintain written security architecture and compliance records.
Cheap Pricing Without Technical Justification
Extremely low pricing often means:
- Shared overloaded servers
- No encryption implementation
- No security testing budget
- No long-term maintenance commitment
Security infrastructure requires continuous investment. Unrealistically cheap platforms usually cut corners in the most dangerous areas.
No Compliance Certifications
If the provider is not aligned with:
- ISO 27001
- SOC 2
- GDPR
- PCI DSS
Your app remains legally exposed even if the interface looks modern.
Outdated Technology Stack
Red flags include:
- Old PHP or Node.js versions
- Unsupported frameworks
- Unpatched databases
- Deprecated encryption libraries
Outdated technology dramatically increases exploit probability.
Poor Code Quality
Low-grade code often shows:
- Hard-coded API keys
- Reused open-source modules without audits
- No version control discipline
- No testing pipelines
Poor code quality leads directly to data breaches.
No Security Updates Policy
If the provider does not offer:
- Regular vulnerability patches
- Emergency hotfix deployment
- Scheduled system upgrades
Your app becomes increasingly vulnerable over time even without active attacks.
Lack of Data Backup Systems
Absence of automated backups means:
- Total data loss during ransomware attacks
- No recovery after system crashes
- High business continuity risk
Backups must be encrypted, geo-redundant, and periodically tested.
No Cyber Insurance Coverage
Serious vendors carry cyber-liability insurance to cover:
- Breach recovery costs
- Legal expenses
- Regulatory penalties
Absence of insurance exposes you personally to lawsuit risks.
Evaluation Checklist Before Selecting a White-Label Provider
Use this due diligence checklist before signing any agreement.
Questions to Ask the Provider
- Do you hold ISO 27001 or SOC 2 certification
- Is your platform GDPR and PCI DSS compliant
- How often do you perform security audits and penetration tests
- What is your incident response time during a breach
- Who is responsible for ongoing security updates
- Where is data hosted and in which jurisdiction
- Do you provide encrypted backups with disaster recovery plans
Documents to Request
- Security architecture documentation
- Compliance certificates
- Penetration testing reports
- Data protection policy
- Disaster recovery and backup plan
- Cyber insurance policy details
Testing Procedures
- Independent vulnerability assessment
- API security testing
- Load and stress testing
- Payment gateway security verification
- Admin panel access control review
Due Diligence Steps
- Verify server locations and cloud providers
- Cross-check compliance claims with certifying bodies
- Review past breach history
- Speak with existing clients about uptime and incident handling
- Perform legal review of data processing agreements
If a provider resists any of these verification steps, that resistance itself becomes a critical red flag.
Best Practices for Secure White-Label Zomato App Implementation
A white-label Zomato app is only as secure as the way it is implemented, configured, and maintained. Even the most secure platform can become vulnerable if best practices are ignored during deployment or post-launch operations. Security must be treated as a continuous process, not a one-time setup.
Pre-Launch Security Preparation
Security Audit Process
Before going live, a complete security audit must be conducted covering:
- Application source code vulnerabilities
- Server and cloud infrastructure security
- Database encryption and access control
- API authentication and authorization layers
- Admin panel and third-party access permissions
This audit identifies hidden gaps that are not visible during normal testing.
Code Review Requirements
Every line of critical code must be reviewed to ensure:
- No hard-coded credentials exist
- Secure authentication and token management is used
- Input validation and sanitization is enforced
- Error handling does not expose system details
Independent code reviews significantly reduce exploitation risk.
Infrastructure Hardening
Your cloud infrastructure must be hardened before deployment:
- Firewalls and network segmentation enabled
- Admin access restricted by IP whitelisting
- Production and staging environments separated
- Auto-scaling and DDoS protection activated
Infrastructure hardening protects the platform from large-scale external attacks.
Compliance Verification
All regulatory requirements must be verified before launch:
- GDPR consent management systems
- PCI DSS-compliant payment workflows
- Data retention and deletion mechanisms
- Regional data residency compliance
Launching without formal compliance verification exposes you to immediate legal risk.
Staff Security Training Programs
Human error remains one of the biggest security threats. All staff must be trained on:
- Password and credential safety
- Phishing and social engineering threats
- Secure system access protocols
- Incident reporting procedures
Even the strongest technical systems fail if internal access is misused.
Post-Launch Security Monitoring
Continuous Security Monitoring
After launch, your white-label Zomato app must run under constant surveillance:
- Real-time threat detection systems
- Automated log analysis
- Intrusion detection and prevention systems
- Unusual traffic and fraud pattern alerts
Continuous monitoring allows early detection before major damage occurs.
Regular Updates and Patches
Security updates must be applied:
- For the app framework
- For server operating systems
- For third-party integrations
- For payment gateway connections
Unpatched vulnerabilities remain the primary cause of long-term data breaches.
Incident Response Planning
A documented incident response plan must clearly define:
- Breach detection procedures
- Immediate containment methods
- User and authority notification timelines
- Forensic investigation workflows
- Recovery and system restoration processes
Fast, structured response reduces legal exposure and customer impact.
User Data Management
Proper data handling policies must enforce:
- Minimal data collection principles
- Secure archival and deletion cycles
- Encrypted storage of sensitive records
- Restricted internal data access
Poor data management practices often trigger regulatory violations.
Backup and Recovery Systems
Your backup systems must ensure:
- Automated daily encrypted backups
- Geo-redundant storage locations
- Periodic disaster recovery simulations
- Rapid restoration capability during outages
Backups protect your business from ransomware, system failures, and accidental data loss.
Security Implementation Timeline

Legal & Compliance Considerations
Security in a white-label Zomato app is not only a technical responsibility but also a strict legal obligation. Regulatory authorities now actively audit food delivery platforms for data protection, payment safety, and user privacy compliance. Non-compliance can lead to operational bans, financial penalties, and even criminal liability in certain regions.
Regulatory Requirements
Data Protection Laws by Region
Your white-label Zomato app must comply with region-specific data protection regulations based on where your users are located.
- India:
Digital Personal Data Protection Act (DPDPA) mandates lawful data processing, user consent, breach reporting, and strict storage controls. - European Union:
General Data Protection Regulation (GDPR) governs data collection, storage, consent, breach disclosure timelines, and user rights. - United States:
CCPA and CPRA regulate how personal data is collected, stored, shared, and deleted, especially for California residents. - Middle East:
Data localization and privacy laws require regional data hosting and strict access controls. - APAC Region:
Countries such as Singapore and Australia enforce strong consumer data protection frameworks with heavy penalties for breaches.
Failure to comply with regional laws can result in forced app shutdowns and cross-border legal disputes.
Industry-Specific Regulations
Food delivery apps also fall under:
- Consumer protection laws
- Electronic transaction regulations
- Digital payment compliance frameworks
- Online marketplace liability laws
These govern chargebacks, refunds, partner onboarding, and grievance redressal systems.
User Consent Management
Legal compliance requires:
- Explicit opt-in consent for data collection
- Clearly defined consent purposes
- Ability for users to withdraw consent
- Consent logs for legal audits
Silent or implied consent models are no longer legally sufficient in many regions.
Privacy Policy Requirements
Your app must publicly disclose:
- What data is collected
- Why it is collected
- How it is stored and processed
- With whom it is shared
- How long it is retained
- How users can request deletion
Privacy policies must be transparent, accessible, and aligned with actual backend practices.
Terms of Service Essentials
Proper terms of service must cover:
- User obligations and restrictions
- Platform liability limits
- Dispute resolution mechanisms
- Payment and refund policies
- Suspension and termination clauses
Weak legal documentation exposes founders to uncontrolled litigation.
Liability Protection
Insurance Requirements
For full legal risk coverage, a white-label Zomato app business should carry:
- Cyber liability insurance
- Data breach insurance
- Professional indemnity insurance
- Third-party liability insurance
These policies cover legal defense costs, breach recovery expenses, and regulatory penalties.
Legal Disclaimers
Disclaimers must be built into:
- User onboarding screens
- Payment flows
- Partner agreements
- Service limitation notices
These help limit the financial exposure of the platform owner during disputes.
User Agreements
Separate legally binding agreements are required for:
- End users
- Restaurant partners
- Delivery personnel
Each agreement must clearly define:
- Data usage rights
- Payment responsibilities
- Dispute handling frameworks
- Liability allocation
Incident Reporting Protocols
Data protection laws now require:
- Breach reporting within fixed timelines
- Notifications to regulatory authorities
- Notifications to affected users
- Documented forensic investigation records
Delaying or hiding breach disclosures often results in additional penalties.
Regulatory Compliance Monitoring
Legal compliance is ongoing and requires:
- Continuous policy updates
- Legal audits
- Regulation tracking
- Vendor compliance verification
What is compliant today can become illegal tomorrow if regulations change.
Compliance Checklist by Region
India
- DPDPA-compliant consent management
- Breach notification mechanisms
- Secure local or approved cross-border hosting
- Lawful data processing policies
European Union
- GDPR user consent records
- Right to access and erasure tools
- Data processing agreements with vendors
- Data Protection Officer appointment
United States
- CCPA and CPRA disclosure compliance
- Opt-out of data selling mechanisms
- Consumer data access tools
- Privacy request response workflow
Middle East
- Saudi and UAE data localization frameworks
- Government audit access readiness
- Encrypted cross-border data transfers
Global Payments
- PCI DSS compliance
- Secure chargeback resolution system
- Fraud prevention frameworks
Without verified legal compliance across these areas, even a technically secure white-label Zomato app remains legally unsafe.
Why Miracuves White-Label Zomato App is Your Safest Choice
Security is only as strong as the engineering culture behind it. While many white-label Zomato app providers focus mainly on speed and pricing, Miracuves is built on a security-first development philosophy that treats data protection, compliance, and risk mitigation as core product features, not add-ons.
Miracuves Security Advantages
Enterprise-Grade Security Architecture
Miracuves builds every white-label Zomato app on a hardened, enterprise-grade architecture that includes:
- Segmented cloud infrastructure
- Isolated databases for each deployment
- Environment-level access restrictions
- Zero-trust access controls
This ensures that even if one environment is compromised, it does not affect others.
Regular Security Audits and Certifications
Miracuves platforms undergo:
- Scheduled vulnerability assessments
- Independent penetration testing
- Continuous code security reviews
- Compliance alignment with global standards
Security is validated repeatedly, not assumed.
GDPR and CCPA Compliant by Default
Every Miracuves white-label Zomato app is shipped with:
- Built-in user consent management
- Data access and deletion workflows
- Data processing agreements
- Privacy-compliant storage policies
This saves founders from retrofitting compliance later.
24/7 Security Monitoring
Miracuves deploys round-the-clock monitoring through:
- Intrusion detection systems
- Real-time traffic analysis
- Automated threat alerts
- Continuous log monitoring
Suspicious activities are detected and addressed immediately.
Encrypted Data Transmission
All data across the platform is protected using:
- TLS encryption for data in transit
- Strong encryption for sensitive data at rest
- Encrypted backup storage
This prevents interception and unauthorized data extraction.
Secure Payment Processing
Miracuves integrates only with:
- PCI DSS-compliant payment gateways
- Tokenized payment workflows
- Fraud detection systems
- Chargeback protection frameworks
Payment credentials are never exposed or stored insecurely.
Regular Security Updates
Security patches and platform updates are applied:
- As soon as vulnerabilities are identified
- Without requiring manual intervention by clients
- With zero-downtime deployment strategies
Your app remains protected against newly discovered threats.
Insurance Coverage Included
Miracuves-backed deployments include:
- Cyber risk insurance protection
- Liability coverage for security incidents
- Legal support frameworks for breach response
This adds an additional layer of business-level risk mitigation.
Conclusion
Don’t compromise on security. Miracuves white-label Zomato app solutions come with enterprise-grade security built in from day one. With over 600 successful projects and a zero-record of major security breaches, Miracuves delivers platforms that are safe, compliant, and built for long-term trust. Get a free security assessment and see why businesses rely on Miracuves for secure, regulation-ready food delivery platforms.
A white-label Zomato app can be both fast to launch and fully secure — but only when security, compliance, and risk management are treated as priorities from day one. In 2025, safety is no longer a technical feature; it is a business requirement that directly impacts trust, growth, and survival. Choosing a security-first provider is not optional anymore — it is the foundation of long-term success.
FAQs
1. How secure is a white-label Zomato app compared to custom development
A properly built white-label Zomato app with ISO, GDPR, and PCI DSS compliance can be as secure as or more secure than custom development when managed by a certified provider.
2. What happens if there is a security breach
An incident response plan is activated, affected systems are isolated, authorities are notified as per law, users are informed, and recovery is handled through backups and cyber insurance.
3. Who is responsible for security updates
The white-label app provider is responsible for core platform security updates, while the business owner must follow operational security practices.
4. How is user data protected in a white-label Zomato app
User data is protected through encryption at rest and in transit, role-based access control, secure servers, and compliance-driven data handling policies.
5. What compliance certifications should I look for
ISO 27001, SOC 2 Type II, GDPR, PCI DSS, and regional data protection laws based on your target market.
6. Can a white-label Zomato app meet enterprise security standards
Yes, when built with secure architecture, continuous monitoring, penetration testing, and verified compliance frameworks.
7. How often should security audits be conducted
At least once before launch and then quarterly or after every major system update.
8. What is included in Miracuves’ security package
Enterprise-grade architecture, compliance readiness, encrypted data flow, secure payments, regular audits, 24/7 monitoring, and breach response support.
9. How is security managed across different countries
Security is aligned with regional data protection laws such as DPDPA, GDPR, CCPA, and Middle East data localization frameworks.
10. What insurance is needed for app security
Cyber liability insurance, data breach insurance, professional indemnity insurance, and third-party liability coverage.
Related Article: