You’ve heard the horror stories—fintech startups losing user data overnight, wallets drained by unseen vulnerabilities, and cloned banking apps hit by compliance violations. In the digital finance era, security isn’t optional—it’s survival.
As more businesses turn to white-label Revolut clones to enter the neobank and digital-wallet market quickly, one question echoes louder than ever:
“Are these ready-made financial platforms truly secure?”
In 2026, with global cyberattacks on fintech systems increasing by over 60%, users expect not just sleek UX —but uncompromising data safety, transaction integrity, and regulatory compliance. Any lapse could mean millions in losses or a permanent trust deficit.
This guide gives you an honest look at white-label Revolut clone security—how it works, where the real risks lie, and what modern protection standards must be in place.
By the end, you’ll know exactly how to choose (or secure) a fintech platform that meets today’s toughest security and compliance expectations.
Understanding White-Label Revolut Clone Security Landscape
What “White-Label Security” Actually Means
In fintech, white-label security refers to the integrated protection measures built into a ready-made financial platform before customization. Unlike custom-built apps—where every layer of security must be designed from scratch—a white-label Revolut clone inherits a foundational security framework: encrypted APIs, authentication layers, payment gateways, and regulatory compliance modules.
However, the real security depends on how the provider maintains, audits, and upgrades this foundation. Many clones are built fast—but not all are built securely.
Common Security Myths vs. Reality
| Myth | Reality |
|---|---|
| “White-label apps are less secure than custom ones.” | Enterprise-grade clones can match or exceed custom builds if they follow ISO 27001 and SOC 2 standards. |
| “Since it’s prebuilt, I don’t need extra audits.” | Every fintech deployment must undergo independent penetration testing before launch. |
| “Using secure APIs means the app is safe.” | APIs are only one layer—data encryption, authentication, and cloud security also matter. |
Why People Worry About White-Label Fintech Apps
Financial apps handle the most sensitive data—user identities, payment cards, bank accounts, and KYC records. The fear is valid: one overlooked vulnerability can lead to massive financial losses or legal penalties under GDPR and PSD2.
Some providers cut corners with outdated frameworks or lack documentation on encryption standards—making due diligence a critical step for founders and CTOs.
Current Threat Landscape (2026)
- API Exploits: Over 40% of fintech breaches in 2024 originated from unsecured or exposed APIs.
- Phishing & Credential Theft: Targeted attacks on mobile banking users increased by 56%.
- Third-Party Risks: 1 in 3 financial apps experienced data exposure via integrated analytics SDKs.
- Cloud Misconfigurations: 22% of incidents were caused by insecure cloud storage of transaction logs.
Security Standards in 2026
Modern fintech security demands multi-layer protection:
- End-to-end encryption using AES-256
- Two-factor or biometric authentication
- Continuous transaction anomaly detection
- Zero-trust network architecture
- Real-time threat intelligence
- Compliance with GDPR, PCI DSS, and SOC 2 Type II
Real-World Statistics
- Global fintech losses from cyber incidents exceeded $12 billion in 2024.
- 67% of startups reported at least one attempted data breach.
- Apps with routine penetration testing had 72% fewer incidents.
- 88% of users said “data safety” was their top concern before installing a finance app.
Key Security Risks & How to Identify Them
When it comes to a white-label Revolut clone, the greatest misconception is that security risks lie only in the app code. In reality, vulnerabilities often emerge across three layers — data, technology, and business operations.
Let’s break them down.
1. Data Protection & Privacy Risks
User Personal Information
White-label fintech apps process KYC data, government IDs, and transaction records. If stored improperly, these can be exposed through unsecured databases or shared servers.
Payment Data Security
Fintech clones must comply with PCI DSS to secure cardholder information. Any deviation can result in card fraud, chargebacks, and loss of banking partnerships.
Location Tracking Concerns
Since many apps use geolocation for fraud detection and compliance checks, weak access controls or improper anonymization can lead to unauthorized data collection.
GDPR/CCPA Compliance
Failure to offer user consent management or data deletion options under regulations like GDPR (EU) and CCPA (California) can lead to millions in fines.
2. Technical Vulnerabilities
Code Quality Issues
Some clone vendors recycle unvetted source code across clients, leaving behind old bugs and insecure libraries. Always demand code audit reports.
Server Security Gaps
Unpatched servers or shared hosting increase the attack surface, particularly for API endpoints handling financial transactions.
API Vulnerabilities
Poor API authentication and unencrypted requests are among the leading causes of fintech data breaches. APIs must use OAuth 2.0, JWT, and rate limiting.
Third-Party Integrations
Integrating analytics, chat, or marketing tools without sandboxing or reviewing permissions can open backdoors into sensitive systems.
3. Business & Legal Risks
Legal Liability
A breach may expose your startup—not the white-label provider—to lawsuits and regulatory penalties if due diligence wasn’t documented.
Reputation Damage
Trust is the currency of fintech. One leaked transaction log can permanently impact user confidence and investor relations.
Financial Losses
Recovery costs, user compensation, and downtime can drain hundreds of thousands of dollars—especially for uninsured startups.
Regulatory Penalties
Authorities like the FCA (UK), FINTRAC (Canada), and RBI (India) impose strict operational guidelines. Noncompliance may result in license revocation.
White-Label Revolut Clone – Risk Assessment Checklist
| Category | Checkpoints | Status |
|---|---|---|
| Data Protection | Encryption (AES-256), GDPR consent forms, secure backups | ☐ |
| Payment Security | PCI DSS compliance, tokenized payments, fraud monitoring | ☐ |
| Infrastructure | Cloud security hardening, SSL/TLS, DDoS protection | ☐ |
| Code Integrity | Static & dynamic code testing, dependency scans | ☐ |
| Third-Party Apps | Permission audits, sandboxing, vendor certifications | ☐ |
| Legal & Compliance | Privacy policy, ToS, audit logs, compliance mapping | ☐ |
| Monitoring & Updates | Patch frequency, vulnerability management | ☐ |
Security Standards Your White-Label Revolut Clone Must Meet
Building trust in a fintech product isn’t about glossy UI or fast onboarding—it’s about compliance, encryption, and resilience.
A white-label Revolut clone handling real transactions must satisfy both international security frameworks and technical protection standards to qualify as a safe platform in 2026.
Essential Certifications & Compliance Frameworks
ISO 27001 — Information Security Management System
This is the global benchmark for secure data handling. It ensures that your provider has documented controls for risk management, data classification, and incident response.
SOC 2 Type II — Operational Trustworthiness
Audits the vendor’s infrastructure, monitoring, and change-management practices to verify long-term reliability—crucial for apps dealing with payment processing and PII.
GDPR & CCPA Compliance
Ensures transparent data usage, explicit user consent, and data-erasure options. For fintech, GDPR compliance isn’t optional—it’s required for EU operations and partnerships.
PCI DSS (Version 4.0)
Mandatory for any app storing, processing, or transmitting card data. It enforces network segmentation, intrusion detection, and encryption at rest and in transit.
HIPAA (If Applicable)
If the Revolut-style app integrates healthcare-related payments or wellness insurance wallets, HIPAA compliance becomes relevant for PHI protection.
Technical Requirements for 2026-Ready Security
| Security Measure | Purpose | Required Standard/Action |
|---|---|---|
| End-to-End Encryption | Protects user data during transfer and storage | AES-256 or RSA-2048 minimum |
| Secure Authentication | Prevents unauthorized access | Multi-factor (2FA), OAuth 2.0, or biometric login |
| Regular Security Audits | Detects vulnerabilities before exploitation | Quarterly third-party penetration testing |
| Penetration Testing | Validates real-world defense | Conducted by certified ethical hackers |
| SSL Certificates | Secures data in motion | TLS 1.3 across all endpoints |
| Secure API Design | Prevents injection and replay attacks | Use of signed JWT, rate limiting, zero-trust access |
| Cloud Security Controls | Ensures infrastructure isolation | Role-based access, encrypted storage, audit trails |
| Incident Response Plan | Minimizes breach impact | 24/7 monitoring, escalation matrix, forensics logs |
Security Standards Comparison Table
| Standard | Scope | Mandatory for Fintech | Covers |
|---|---|---|---|
| ISO 27001 | Global information security | Yes | Risk, access, encryption, incident management |
| SOC 2 Type II | Cloud & operational processes | Yes | System reliability, confidentiality, monitoring |
| GDPR / CCPA | Data privacy & user consent | Yes (Region-based) | Personal data rights, deletion, portability |
| PCI DSS v4.0 | Payment transaction security | Yes | Network, encryption, authentication |
| HIPAA | Healthcare payment data | Optional | Health information, PHI protection |
When evaluating providers, confirm third-party audit certificates and request the latest security-compliance reports.
At Miracuves, all Revolut-style builds are developed within ISO 27001-certified frameworks, audited for SOC 2 Type II, and aligned with GDPR + PCI DSS v4.0 by default—ensuring your fintech launch is regulatory-ready from day one.
Red Flags — How to Spot Unsafe White-Label Providers
When it comes to fintech, security negligence can’t be undone.
Choosing the wrong white-label Revolut clone provider could expose your business to hidden vulnerabilities, compliance gaps, or unfixable code risks. Here’s how to identify warning signs before signing the deal.
Common Red Flags to Watch For
1. No Security Documentation
If the provider cannot show ISO 27001, SOC 2, or PCI DSS compliance papers — walk away. Proper vendors maintain transparent documentation for audits and data protection.
2. Cheap Pricing Without Explanation
If the pricing seems too good to be true, it often is. Substandard clones cut costs by removing essential security layers like encryption, code audits, or dedicated hosting.
3. No Compliance Certifications
Financial apps without GDPR or PCI DSS compliance expose you to penalties and reputational damage. Always request up-to-date compliance validation.
4. Outdated Technology Stack
Legacy frameworks or unpatched libraries leave exploitable gaps. Check whether the app runs on current frameworks like Node.js LTS, Kotlin, Swift 5+, and TLS 1.3.
5. Poor Code Quality or Lack of Review
Providers who refuse external code audits or don’t follow version control systems (Git, CI/CD) are security liabilities.
6. No Security Update Policy
Ask how often they roll out patches. Fintech systems should receive monthly vulnerability updates and emergency zero-day patches.
7. Lack of Data Backup Systems
Without encrypted cloud backups and recovery plans, you risk permanent loss after a breach or outage.
8. No Insurance Coverage
Professional vendors offer cyber liability insurance, ensuring your business is protected financially in case of data compromise.
White-Label Revolut Clone – Provider Evaluation Checklist
| Category | Key Questions to Ask | Expected Answer |
|---|---|---|
| Security Framework | Which compliance frameworks do you follow (ISO 27001, SOC 2, PCI DSS)? | Certified & verified |
| Infrastructure | Is your hosting environment isolated or shared? | Dedicated / isolated |
| Audit Frequency | How often do you perform security audits? | Quarterly minimum |
| Data Protection | How is user data encrypted and stored? | AES-256 / RSA-2048 |
| Access Control | Do you use role-based permissions and MFA for admins? | Yes |
| Incident Response | What is your breach response time and protocol? | <4 hours, documented |
| Insurance | Is cyber liability insurance included? | Yes |
| Update Policy | How frequently do you patch or upgrade? | Monthly / as needed |
| Third-Party Reviews | Are your SDKs and APIs audited independently? | Yes, annually |
Due Diligence Steps Before Choosing a Provider
- Request security audit reports and certification proofs.
- Conduct an independent code review before deployment.
- Ask for GDPR mapping documents and privacy policy templates.
- Verify server location compliance (EU, US, India regulations).
- Include security SLAs in your contract.
- Confirm post-launch support and update cadence.
A secure fintech partnership isn’t just about features — it’s about accountability, documentation, and continuous compliance.
Miracuves operates with full transparency: every client receives detailed audit logs, certification proofs, and risk-management guarantees before deployment.
Best Practices for Secure White-Label Revolut Clone Implementation
Building and launching a Revolut-style app safely isn’t only about compliance — it’s about discipline throughout the development lifecycle.
From pre-launch audits to post-launch monitoring, every phase requires structure, documentation, and ongoing vigilance.
Pre-Launch Security Practices
1. Comprehensive Security Audit
Before going live, conduct both static and dynamic application testing (SAST & DAST) to identify vulnerabilities in code, APIs, and server configurations.
2. Code Review Requirements
Implement a dual-review policy — one internal and one external. Third-party audits ensure unbiased verification of encryption standards, logic flaws, and access control.
3. Infrastructure Hardening
Secure the deployment environment:
- Enable firewalls and intrusion detection systems
- Use role-based access control (RBAC)
- Disable default ports and test for misconfigurations
- Enforce TLS 1.3 with HSTS policies
4. Compliance Verification
Before launch, verify certifications for:
- GDPR (user data consent and deletion rights)
- PCI DSS (cardholder data security)
- SOC 2 Type II (infrastructure reliability)
5. Staff Security Training
Human error remains the top breach vector. Conduct team training on phishing awareness, access hygiene, and incident escalation procedures.
Post-Launch Monitoring & Maintenance
1. Continuous Security Monitoring
Adopt SIEM (Security Information & Event Management) tools for 24/7 real-time detection of suspicious activity, failed logins, or fraud attempts.
2. Regular Updates & Patch Management
Schedule monthly updates and critical-patch turnarounds within 48 hours of CVE disclosure. Automate dependency scanning for libraries and APIs.
3. Incident Response Planning
Have a formalized plan including:
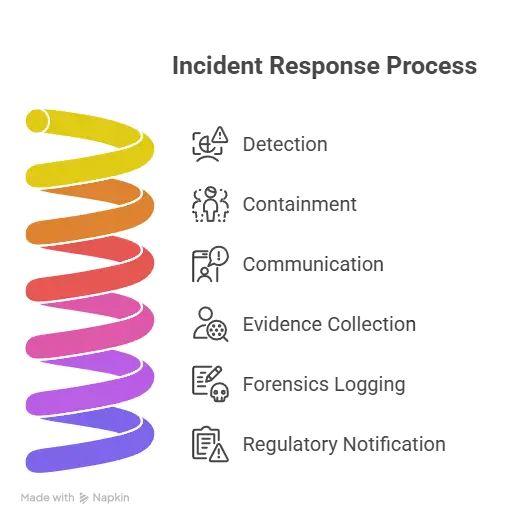
4. User Data Management
Encrypt data both at rest and in transit. Establish a data retention policy and anonymize inactive user records after the legally required duration.
5. Backup & Recovery Systems
Perform daily encrypted backups stored across geo-redundant data centers. Test disaster recovery drills quarterly to validate uptime and rollback efficiency.
Security Implementation Timeline
| Phase | Focus Area | Key Deliverables | Timeline |
|---|---|---|---|
| Week 1–2 | Security architecture planning | Threat model, compliance map | |
| Week 3–5 | Code audit & penetration testing | Reports, mitigation checklist | |
| Week 6–7 | Infrastructure hardening | Firewalls, SSL, RBAC setup | |
| Week 8 | Compliance validation | ISO/SOC/PCI audit verification | |
| Post-Launch (Ongoing) | Continuous monitoring & updates | Logs, patch reports, SLA reviews | Continuous |
At Miracuves, this workflow is baked into every deployment.
Our Revolut clone clients receive pre-launch audit certificates, continuous monitoring dashboards, and guaranteed patch delivery under a defined SLA — turning security into a measurable, managed process.
Legal & Compliance Considerations
Security alone doesn’t protect a fintech business — legal compliance completes the shield.
A white-label Revolut clone operates in a regulated environment where data handling, user consent, and regional compliance frameworks dictate how safely you can grow and scale.
Regulatory Requirements by Region
| Region | Primary Regulation | Key Focus |
|---|---|---|
| European Union (EU) | GDPR + PSD2 | User data privacy, Strong Customer Authentication (SCA), open banking APIs |
| United Kingdom (UK) | UK GDPR + FCA Guidelines | Financial conduct, customer due diligence, AML compliance |
| United States (US) | CCPA + GLBA + FinCEN | Data privacy, consumer financial protection, anti-money laundering |
| India | RBI + DPDP Act 2023 | Data localization, payment aggregator licensing, KYC verification |
| Canada | PIPEDA + FINTRAC | Cross-border data transfer, financial reporting, AML laws |
| Middle East (UAE, KSA) | NESA + ADGM + SAMA Regulations | Cloud hosting restrictions, data residency, bank-level encryption |
These frameworks ensure transparency, accountability, and user protection — all of which must be reflected in your Revolut-style app’s architecture, contracts, and operations.
Core Legal Elements Every Fintech App Needs
1. User Consent Management
Collect explicit consent for all data processing, sharing, and marketing activities. Provide users with easy-to-access opt-out and data deletion controls.
2. Privacy Policy Requirements
Clearly state:
- What data is collected
- How it’s stored and shared
- Retention duration
- Rights of access, rectification, and erasure
3. Terms of Service (ToS) Essentials
Include disclaimers for:
- Third-party integrations
- Downtime or transaction delays
- Jurisdiction and dispute resolution clauses
4. Data Processing Agreements (DPAs)
When using third-party processors (e.g., AWS, Stripe), ensure all contracts include GDPR Article 28-compliant clauses defining security responsibilities.
5. Cross-Border Data Flow
Verify that all international data transfers comply with Standard Contractual Clauses (SCCs) and local hosting requirements where applicable.
Liability Protection Strategies
1. Cyber Insurance Coverage
Covers direct losses, business interruption, and legal expenses resulting from data breaches or system failures. Miracuves includes cyber-risk coverage in enterprise deployments.
2. Incident Reporting Protocols
Set clear internal processes for notifying regulators and users within 72 hours of a confirmed breach (as required by GDPR and most global frameworks).
3. Legal Disclaimers & User Agreements
Protect your company against misuse or unauthorized modifications by clients or users.
4. Regulatory Compliance Monitoring
Appoint a Data Protection Officer (DPO) or Compliance Manager to oversee ongoing legal adherence and documentation.
Compliance Checklist by Region
| Checklist Item | EU | US | India | UK | MENA |
|---|---|---|---|---|---|
| GDPR / Local Privacy Law | Yes | Optional | Yes (DPDP) | Yes | Yes |
| Payment Security (PCI DSS) | Yes | Yes | Yes | Yes | Yes |
| AML / KYC Verification | Yes | Yes | Yes | Yes | Yes |
| Data Localization | Optional | No | Yes | Optional | Yes |
| Breach Notification (72h Rule) | Yes | Optional | Optional | Yes | Optional |
| DPO Appointment | Yes | Optional | Optional | Yes | Optional |
Read more : – Pre-launch vs Post-launch Marketing for Revolut Clone Startups
Legal readiness builds institutional trust.
Miracuves’ Revolut clone implementations come with GDPR-mapped privacy documentation, region-specific compliance frameworks, and built-in consent management, ensuring your launch aligns with every major regulatory expectation.
Why Miracuves White-Label Revolut Clone Is Your Safest Choice
In a market flooded with generic fintech templates and short-term vendors, Miracuves stands apart as a “security-first” white-label technology provider.
Our Revolut-style fintech clone isn’t just built to perform — it’s engineered to withstand modern cyber threats, meet regulatory benchmarks, and protect business credibility.
Miracuves Security Advantages
1. Enterprise-Grade Security Architecture
Every deployment runs on a zero-trust cloud environment with strict network segmentation, containerized microservices, and AES-256 data encryption — ensuring total isolation between tenants.
2. Regular Security Audits & Certifications
We perform quarterly penetration testing and annual SOC 2 Type II audits, with third-party verifications confirming our ISO 27001-aligned security posture.
3. GDPR / CCPA Compliance by Default
All builds include pre-configured data-protection modules for consent management, cookie control, data export, and erasure requests — ready for EU and US jurisdictions.
4. 24/7 Security Monitoring
A dedicated Security Operations Center (SOC) tracks API activity, transaction anomalies, and potential intrusions around the clock, with instant alerting and automated mitigation.
5. Encrypted Data Transmission & Storage
All communication channels — from API calls to payment gateways — are protected via TLS 1.3 and RSA 2048 encryption, with tokenized storage for sensitive credentials.
6. Secure Payment Processing
Miracuves integrates PCI DSS v4.0-compliant gateways supporting fraud detection, device fingerprinting, and dynamic CVV protection for digital cards.
7. Regular Security Updates & Patch Management
Our continuous-integration pipeline ensures every client deployment receives monthly patch releases, emergency zero-day fixes, and dependency updates.
8. Built-In Cyber Insurance Coverage
All enterprise clients are covered under Miracuves’ cyber liability insurance, providing protection against potential data-breach damages and legal costs.
What This Means for Your Business
Partnering with Miracuves means your white-label Revolut clone isn’t just “compliant” — it’s continuously protected, auditable, and verifiably secure.
You gain faster regulatory approval, improved investor confidence, and the ability to scale globally without fear of data exposure or legal setbacks.
Don’t compromise on security.
Miracuves white-label Revolut clone solutions come with enterprise-grade protection baked in — from encrypted infrastructure to compliance documentation.
Our 600 + successful deployments have maintained zero major security breaches to date.
Get a free security assessment today and see why businesses trust Miracuves for safe, compliant fintech platforms.
Read more : – How to Hire the Best Revolut Clone Developer
conclusion
In the fast-moving world of fintech, trust is the ultimate currency.
Users don’t just choose apps for convenience — they choose platforms that safeguard their identity, money, and privacy. A single breach can undo years of brand building and investor confidence.
That’s why, in 2026, security is not a feature — it’s the foundation of every sustainable white-label Revolut clone. Compliance frameworks, encryption protocols, and insurance coverage are no longer optional add-ons; they’re the backbone of user confidence and regulatory approval.
The businesses that thrive will be the ones that treat security as a culture, not a checklist — continuously auditing, updating, and improving.
With Miracuves, that mindset comes standard. You’re not just deploying a white-label fintech app — you’re launching a future-proof, compliance-verified, enterprise-grade banking solution built for global security demands.
FAQs
1. Is a white-label Revolut clone secure?
Yes. When built under ISO 27001, SOC 2 Type II, and PCI DSS standards, it’s as secure as any custom fintech app — sometimes safer due to proven architecture.
2. What if a breach happens?
Miracuves offers 24/7 monitoring, 4-hour response, and insurance-backed coverage to contain and report incidents within 72 hours.
3. Who manages security updates?
We handle all patches and vulnerability fixes under a monthly SLA, ensuring zero outdated components.
4. How is user data protected?
All data is AES-256 encrypted, transferred via TLS 1.3, tokenized, and stored in geo-redundant servers.
5. What compliance is required?
Fintech apps must follow GDPR/CCPA, PCI DSS v4.0, and SOC 2 Type II for full legal and regulatory coverage.
6. Can it meet enterprise standards?
Yes — our modular, microservice-based build passes independent audits and penetration tests quarterly.
7. What’s in Miracuves’ security package?
ISO-certified development, GDPR-ready data systems, 24/7 SOC monitoring, penetration testing, and cyber insurance.
Related Articles:








