You’ve heard the horror stories about data breaches — millions of user profiles exposed, passwords leaked, and personal data sold to advertisers.
Now imagine that happening in your white-label Facebook app — the one you launched to connect communities, build engagement, or power a new social experience. In 2025, when privacy regulations are stricter and user trust is fragile, app safety isn’t just a checkbox — it’s your business’s survival line.
As white-label social platforms rise in popularity, so do the concerns around their security. Entrepreneurs love the idea of launching fast with ready-made app solutions, but many fear hidden vulnerabilities, weak encryption, or non-compliance risks that could lead to costly breaches.
This article takes an honest look at white-label Facebook app security — what can go wrong, how to prevent it, and how to make sure your platform stands strong against modern cyber threats. You’ll find real standards, proven protections, and the security framework trusted by Miracuves — a company that builds compliant, enterprise-grade apps without compromise.
Understanding White-Label Facebook App Security Landscape
When we talk about white-label app security, most people imagine basic encryption or password protection — but the reality runs much deeper. A white-label Facebook app inherits the complexity of a global social platform, handling everything from private messages to live video streams, user-generated content, and location data. Understanding its security landscape means looking beyond surface features to the hidden framework that protects every interaction.
What “white-label security” actually means
White-label app security isn’t just about code ownership — it’s about accountability. When a development company offers a white-label Facebook app, they’re giving you a pre-built framework that must still be hardened, audited, and customized to meet compliance laws like GDPR or CCPA. Security doesn’t come “out of the box”; it requires continuous adaptation to evolving threats.
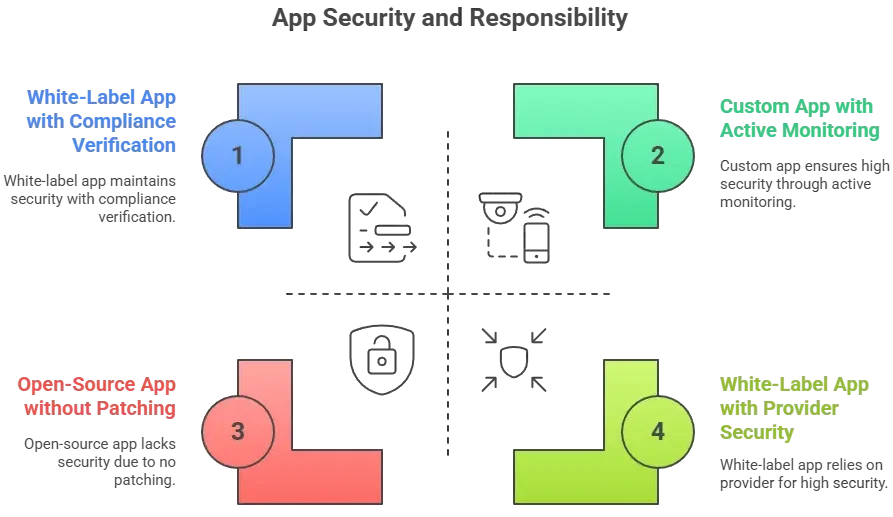
Why people worry about white-label apps
- Limited visibility into backend security measures
- Inconsistent update schedules
- Potential reuse of codebases across multiple clients
- Non-compliance with privacy or regional data protection laws
- Lack of independent third-party security audits
Current threat landscape for social networking apps (2025)
Social apps, including Facebook-style platforms, face a growing number of targeted threats:
- Data scraping attacks exploiting public APIs
- Malicious bots collecting user content or session data
- Deepfake-based identity theft during verification or live streaming
- Cloud misconfigurations leading to exposed storage buckets
- Phishing campaigns targeting admin dashboards
According to a 2025 report by Cybersecurity Ventures, social media apps remain among the top three industries for data breaches, accounting for 18% of total global cyberattacks last year alone.
Security standards in 2025
Leading white-label developers now align with global compliance standards such as ISO 27001, SOC 2 Type II, and GDPR, alongside region-specific regulations like CCPA (California), PDPB (India), and Digital Markets Act (EU). Encryption, zero-trust authentication, and AI-driven threat monitoring have become standard expectations — not luxuries.
Key Security Risks & How to Identify Them
Running a white-label Facebook app comes with tremendous growth potential — but also significant exposure. Social networking platforms are magnets for cybercriminals due to the large amount of user data, community interactions, and integrated third-party systems they manage daily. Understanding these risks is the first step toward proactive defense.
Read more : – Top 5 Mistakes Startups Make When Building a Facebook Clone
High-risk areas to monitor carefully
1. Data protection & privacy
Your app stores and processes sensitive data — from user identities to behavioral analytics. Any weakness here can lead to reputational and legal disasters.
- User personal information: Names, photos, contact details, and social connections must be stored with AES-256 encryption and never logged in plaintext.
- Payment data security: If you support in-app purchases or ads, PCI DSS compliance and tokenized payments are mandatory.
- Location tracking concerns: Always anonymize or request explicit consent for location data to avoid privacy violations.
- GDPR/CCPA compliance: Users must be able to view, export, and delete their data — “right to be forgotten” compliance isn’t optional in 2025.
2. Technical vulnerabilities
Even a well-coded app can be compromised if infrastructure or integrations are poorly managed.
- Code quality issues: Weak or unreviewed code can create injection points for malicious scripts. Always demand code audit reports.
- Server security gaps: Insecure cloud storage, weak firewalls, or missing SSL certificates can expose the app backend.
- API vulnerabilities: Facebook-style apps rely heavily on APIs for content sharing and authentication — insecure endpoints can lead to massive data leaks.
- Third-party integrations: Plugins, analytics tools, or ad SDKs can introduce new attack surfaces if not sandboxed or vetted.
3. Business risks
Security isn’t only technical — it’s also strategic. A single data incident can cost your business millions in recovery and reputation loss.
- Legal liability: Breaches can result in lawsuits, fines, and regulatory investigations.
- Reputation damage: Users lose trust quickly after a privacy failure. Restoring credibility may take years.
- Financial losses: Average breach cost for social platforms in 2025 exceeds $4.2 million (IBM Security Report).
- Regulatory penalties: GDPR fines can reach up to €20 million or 4% of annual global revenue, whichever is higher.
White-label Facebook app risk assessment checklist
| Risk Area | Key Question | Assessment Action |
|---|---|---|
| Data storage | Is user data encrypted at rest and in transit? | Verify encryption protocols and SSL/TLS certificates. |
| Access control | Who can access admin or developer dashboards? | Implement 2FA and role-based access control. |
| API management | Are APIs protected against injection or DDoS? | Conduct regular penetration testing. |
| Compliance | Is the app GDPR/CCPA certified? | Request compliance documentation. |
| Incident readiness | Do you have a data breach response plan? | Simulate scenarios and train staff quarterly. |
Security Standards Your White-Label Facebook App Must Meet
A secure white-label Facebook app doesn’t just rely on good code — it depends on certified, verifiable, and continuously audited standards. These frameworks protect not only user data but also your brand’s credibility and compliance posture in a world of tightening regulations.
Essential certifications to demand from your white-label app provider
- ISO 27001 Compliance:
The gold standard for information security management. It ensures that the developer follows strict policies around data storage, encryption, access control, and risk management. - SOC 2 Type II Certification:
Validates that a company maintains security, availability, confidentiality, and processing integrity over time — not just in theory but through ongoing audits. - GDPR Compliance:
Mandatory for handling data of EU residents. The app must ensure user consent, right to data deletion, and transparent processing records. - HIPAA (if applicable):
Essential if your platform handles health-related communities, ensuring secure storage and sharing of health data. - PCI DSS Compliance:
Required for apps handling payments, ad transactions, or wallet top-ups — guaranteeing encryption and tokenization of all financial data.
Technical requirements for a secure white-label Facebook app
- End-to-end encryption:
All communications — including chat messages, posts, and media uploads — should be encrypted from sender to receiver. - Secure authentication (2FA/OAuth):
Users must have the option for two-factor authentication, and the platform should support OAuth 2.0 for safe third-party login. - Regular security audits:
Every quarter, both internal and external audits should be performed to uncover vulnerabilities before attackers do. - Penetration testing:
Simulated attacks identify weaknesses in real time, ensuring your platform is ready for actual threats. - SSL certificates:
Mandatory for all data exchanges between client and server — ensuring no plain-text information travels across the web. - Secure API design:
Every API endpoint should have proper authentication, rate limiting, and input validation to prevent data scraping and abuse.
Security standards comparison table
| Standard | Purpose | Required For | Renewal Cycle |
|---|---|---|---|
| ISO 27001 | Information Security Management | All apps handling user data | Every 3 years (with annual audits) |
| SOC 2 Type II | Operational and Data Security | Enterprise-grade platforms | Annual |
| GDPR | Data Privacy Compliance | Apps with EU users | Continuous compliance |
| HIPAA | Health Information Security | Health-related apps | Annual |
| PCI DSS | Payment Data Security | Apps with payments or ads | Annual |
A provider that can’t show these certifications or regular audit reports is putting your platform and your users at risk. A secure app should always be verifiable, not just promised.
Red Flags – How to Spot Unsafe White-Label Providers
Not every white-label developer builds with the same level of discipline or accountability. Some focus on fast delivery or low pricing — but beneath that convenience, serious security blind spots can lurk. Knowing how to identify unsafe providers before signing a contract can save your business from future breaches, fines, and brand damage.
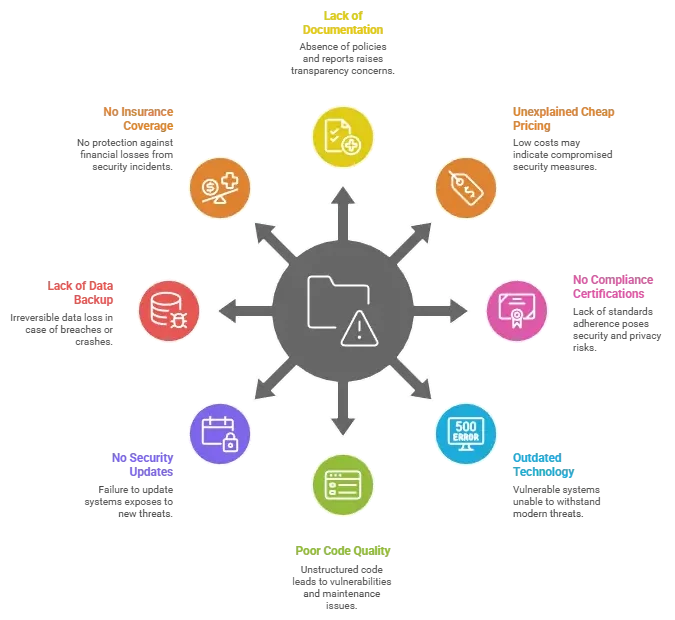
Evaluation checklist for choosing a safe white-label Facebook app provider
| Evaluation Area | What to Ask | Why It Matters |
|---|---|---|
| Security Policy | “Can you share your latest ISO/SOC 2 audit report?” | Confirms ongoing compliance. |
| Code Review | “Do you perform independent security audits?” | Ensures neutral vulnerability testing. |
| Data Management | “Where is data hosted and how is it encrypted?” | Reveals storage and privacy practices. |
| Updates & Maintenance | “How often are patches and updates released?” | Continuous protection against evolving threats. |
| Backup & Recovery | “Do you maintain real-time backups and DR plans?” | Prevents data loss during outages or breaches. |
| Liability Protection | “Do you offer cyber insurance coverage?” | Shields you from financial and legal damages. |
Due diligence steps before signing
- Request written documentation of all certifications and testing.
- Verify hosting locations comply with GDPR and local data laws.
- Conduct a third-party audit if possible before deployment.
- Include service-level security obligations in the contract.
- Require post-launch monitoring and vulnerability management clauses.
The right provider won’t just sell you an app — they’ll partner with you to maintain ongoing safety and compliance.
Read more : –Top Facebook Features Explained
Best Practices for Secure White-Label Facebook App Implementation
Building a white-label Facebook app is only half the journey — securing it is a continuous process. Whether you’re preparing for launch or managing post-deployment operations, following a structured security roadmap helps you minimize risks, maintain compliance, and protect your users’ trust.
Pre-launch security best practices
- Comprehensive security audit:
Before your app goes live, conduct a full-scale security audit that examines code, APIs, and server configurations. This identifies vulnerabilities early and prevents costly post-launch issues. - Independent code review:
Bring in third-party security experts to review your app’s source code. They can catch unsafe dependencies, outdated libraries, or logic flaws that internal teams might overlook. - Infrastructure hardening:
Secure your hosting environment with firewalls, SSL, intrusion detection systems (IDS), and distributed denial-of-service (DDoS) protection. Misconfigured cloud servers are a leading cause of data leaks. - Compliance verification:
Validate GDPR, CCPA, and ISO 27001 compliance before collecting user data. Include automated consent tracking and transparent privacy disclosures. - Staff training and access control:
Train developers, admins, and moderators on secure handling of user data. Use role-based permissions and enforce two-factor authentication for all administrative access.
Post-launch monitoring and protection
- Continuous security monitoring:
Implement real-time intrusion detection, log monitoring, and alert systems to catch unusual patterns before they become breaches. - Regular updates and patches:
Cyber threats evolve daily. Schedule monthly updates to fix vulnerabilities in frameworks, SDKs, and dependencies. - Incident response planning:
Prepare a crisis plan for potential breaches. Define who investigates, how users are informed, and what actions are taken to mitigate exposure. - User data management:
Regularly purge inactive or redundant data. Encrypt backups and ensure user content remains protected even after deletion requests. - Backup and recovery systems:
Automate backups daily and store them in multiple secure regions. Test your disaster recovery process quarterly to confirm that full restoration is possible within hours.
Security implementation timeline
| Phase | Action Item | Responsibility | Timeframe |
|---|---|---|---|
| Phase 1 | Security & code audit | Developer + Auditor | Week 1–2 |
| Phase 2 | Infrastructure hardening | DevOps team | Week 3 |
| Phase 3 | Compliance validation | Legal + IT | Week 4 |
| Phase 4 | Pre-launch penetration test | External vendor | Week 5 |
| Phase 5 | Go-live + monitoring setup | DevOps + Security team | Week 6 |
| Ongoing | Patching, updates, backups | Internal team | Monthly |
A secure launch is never an accident — it’s the result of intentional processes, verified compliance, and disciplined execution. Miracuves follows this same layered approach to ensure every deployment remains airtight and future-ready.
Read more : – Facebook App Marketing Strategy: How to Win
Legal & Compliance Considerations
Even the most technically secure white-label Facebook app can face serious consequences if it fails to meet legal and regulatory obligations. Security and compliance are intertwined — one protects your systems, the other protects your organization from fines, lawsuits, and reputational harm. In 2025, global regulators are more aggressive than ever about enforcing data protection laws, making compliance a non-negotiable aspect of app ownership.
Regulatory requirements to follow
- Data protection laws by region
- Europe (GDPR): Requires user consent for all personal data usage, full transparency, and “right to be forgotten.”
- United States (CCPA/CPRA): Users must be informed of how data is sold or shared, with easy opt-out mechanisms.
- India (DPDP Act 2023): Mandates data localization, user consent logs, and government breach notifications.
- Middle East & APAC: Countries like UAE and Singapore enforce strong cross-border data transfer and retention controls.
- Industry-specific regulations
- Apps that handle financial transactions, healthcare data, or advertising analytics may fall under PCI DSS, HIPAA, or DMA requirements.
- White-label platforms supporting ad monetization must disclose data-sharing with third-party networks under local advertising laws.
- User consent management
- Build consent banners and preference dashboards that record explicit opt-ins for cookies, location access, and analytics tracking.
- Maintain audit trails showing when and how users granted permissions.
- Privacy policy requirements
- Clearly explain data collection, processing, and sharing practices in simple language.
- Include details on retention periods, user rights, and breach response procedures.
- Terms of service essentials
- Define acceptable use, content moderation policies, and account suspension conditions.
- Include disclaimers for third-party integrations and community-generated content.
Liability protection for app owners
- Insurance requirements
Obtain cyber liability insurance covering data breaches, ransomware recovery, and regulatory penalties. Many investors now require this before funding social or messaging platforms. - Legal disclaimers
Explicitly limit liability for user-generated content and clarify that users remain responsible for their posts, uploads, and activities. - User agreements
Use click-wrap agreements to ensure legal enforceability. Keep records of acceptance dates and versions for all registered users. - Incident reporting protocols
Establish a 72-hour disclosure policy (in line with GDPR) and notify users and authorities of any confirmed breach within the legal timeframe. - Regulatory compliance monitoring
Appoint a Data Protection Officer (DPO) or compliance lead to oversee audits, vendor agreements, and documentation updates.
Compliance checklist by region
| Region | Core Regulation | Key Compliance Action | Reporting Window |
|---|---|---|---|
| European Union | GDPR | Consent logs, user rights dashboard, breach report | 72 hours |
| United States | CCPA/CPRA | Opt-out management, “Do Not Sell” link, privacy audit | 30 days |
| India | DPDP Act | Data localization, consent recordkeeping, DPO appointment | 72 hours |
| Canada | PIPEDA | Transparent privacy notices, retention limits | 10 days |
| Australia | Privacy Act 1988 | Breach notification, consent documentation | 30 days |
Neglecting legal compliance isn’t just risky — it’s business suicide in the social app landscape. Aligning your white-label Facebook app with these standards is not optional; it’s foundational to sustainable growth.
Read more : – How to Hire the Best Facebook Clone Developer
Why Miracuves White-Label Facebook App Is Your Safest Choice
When it comes to building a social platform that handles sensitive user data, real-time interactions, and massive engagement — trust is everything. Miracuves takes that trust seriously, embedding enterprise-grade security into every white-label Facebook app it develops. The result? A solution that’s not only scalable and customizable but also certified, compliant, and ready to face 2025’s toughest digital threats.
Miracuves security advantages
- Enterprise-grade security architecture
Every white-label app from Miracuves is built on a layered security model — combining data encryption, firewalls, intrusion detection, and access control systems that meet ISO and SOC 2 Type II benchmarks. - Regular security audits and certifications
Miracuves undergoes continuous internal and third-party audits to identify vulnerabilities before deployment. Reports are available for clients upon request to ensure total transparency. - GDPR/CCPA compliant by default
All apps come with pre-built consent management, data anonymization, and privacy dashboard modules — ensuring legal compliance from day one. - 24/7 security monitoring
A dedicated monitoring infrastructure tracks suspicious activity and performance anomalies in real time, ensuring instant response to any irregularities. - Encrypted data transmission
From private messages to media uploads, all user communications are encrypted using AES-256 and transmitted through SSL-secured channels. - Secure payment processing
Miracuves integrates PCI DSS–compliant gateways, ensuring all financial transactions remain tokenized, verified, and traceable without exposing card data. - Regular security updates
Every deployment includes free patch updates and security enhancements for one year — keeping your app current with evolving frameworks and threat intelligence. - Insurance coverage included
All enterprise clients are protected under Miracuves’ cyber liability framework, offering additional assurance against rare incidents or system compromise.
Why businesses trust Miracuves
- 600+ successful projects delivered with zero major security breaches
- Trusted by startups, enterprises, and global brands in fintech, mobility, and social tech
- Proven compliance expertise across ISO 27001, SOC 2 Type II, and GDPR
- Transparent architecture with full source-code ownership and regular audits
Conclusion :
Don’t compromise on security. Miracuves white-label Facebook app solutions come with enterprise-grade protection built right in — not as an add-on. With zero data breaches across hundreds of projects, Miracuves sets the gold standard for safe, compliant social platforms.
To schedule your consultation or request a detailed compliance report.
Miracuves empowers businesses to build and scale with confidence, combining speed, affordability, and enterprise-grade protection. From encryption to compliance, every layer of your app is fortified with best-in-class security so you can focus on what matters most — growth, innovation, and community.
In an era where data is the new currency, your users’ trust is your most valuable asset. Protect it, and your platform will thrive. Neglect it, and no amount of marketing will save it.
FAQs
1. Is insurance really necessary?
Yes — it protects your business from legal, financial, and reputational fallout in case of breaches.
2. How secure is a white-label app compared to custom development?
Equally secure — if it follows ISO, SOC 2, and GDPR standards with regular audits.
3. What happens if there’s a security breach?
A response plan is activated within 72 hours to contain, report, and resolve the issue.
4. Who handles security updates?
Miracuves provides free updates and patches for one year, with extended options available.
5. How is user data protected?
Encrypted using AES-256 and transmitted via SSL; stored on ISO 27001-certified servers.
6. Which compliance certifications should I check for?
ISO 27001, SOC 2 Type II, GDPR, and PCI DSS for payment-enabled apps.
7. Can a white-label app meet enterprise-level security?
Yes — Miracuves apps meet enterprise benchmarks with layered protection and continuous monitoring.
8. How often should security audits be done?
At least quarterly; Miracuves conducts internal reviews every 90 days.
9. What’s included in Miracuves’ security package?
Encryption, 2FA, SSL, code audits, penetration testing, and cyber-insurance coverage.
10. How does Miracuves handle security globally?
Region-specific compliance (GDPR, CCPA, DPDP Act) is built into each deployment.
Related Articles :