You’ve heard the horror stories about data breaches, leaked customer locations, stolen payment details, and grocery apps suddenly going offline after a security incident. For founders planning to launch a white-label Blinkit app, one question dominates every serious conversation: Is it actually safe?
This concern is valid. On-demand grocery and quick-commerce apps handle some of the most sensitive data in the digital economy — real-time user locations, saved payment methods, order histories, household consumption patterns, and merchant settlement data. In 2026, a single security failure doesn’t just cause technical downtime; it can trigger regulatory penalties, brand erosion, and permanent loss of user trust.
At the same time, there’s a lot of misinformation around white-label app safety. Many people assume that a white-label Blinkit app is automatically less secure than a custom-built platform. Others believe security is “handled by the vendor” and requires no founder involvement at all. Both assumptions are dangerous.
In this guide, we’ll take an honest, security-first look at white-label Blinkit app safety in 2026. We’ll break down real risks, current threat landscapes, compliance expectations, and the exact security standards your app must meet to operate safely at scale. Most importantly, we’ll explain how choosing a security-engineered provider like Miracuves fundamentally changes the risk equation.
This is not a sales pitch disguised as content. It’s a practical, founder-level security assessment — so you can launch fast without compromising safety, compliance, or credibility.
Understanding White-Label Blinkit App Security Landscape
What White-Label Blinkit App Security Actually Means
White-label Blinkit app security does not mean “shared security” or “copied safety.” It refers to a pre-engineered app architecture where core features already exist, but security depends entirely on how the provider has designed data handling, infrastructure, and compliance layers.
A secure white-label Blinkit app includes:
- Isolated databases per client
- Encrypted user and order data
- Secure merchant and delivery partner access
- Controlled API communication between app modules
Security is not defined by whether an app is white-label or custom. It is defined by how well the system is architected and maintained.
Why Founders Worry About White-Label Blinkit App Security
Quick-commerce apps attract concern because they combine:
- Real-time location tracking
- Stored payment credentials
- High-frequency transactions
- Multiple user roles (customers, delivery partners, merchants, admins)
A vulnerability in any one layer can expose the entire ecosystem. In 2026, users are more privacy-aware, regulators are stricter, and attackers are more sophisticated.
Current Threat Landscape for Blinkit-Type Platforms
Data Breaches
Grocery and delivery apps are frequent targets due to stored personal data and predictable traffic patterns.
API Exploits
Order creation, wallet balance, and delivery assignment APIs are often abused if rate limiting and authentication are weak.
Account Takeovers
Poor authentication flows allow attackers to hijack user or delivery partner accounts.
Payment Fraud
Insecure payment integrations expose apps to chargebacks, token leakage, and wallet manipulation.
Security Standards Expected in 2026
In 2026, a white-label Blinkit app is expected to meet:
- Strong encryption at rest and in transit
- Secure cloud infrastructure with isolation
- Regular vulnerability assessments
- Documented incident response processes
Anything less is considered operationally negligent by enterprise partners and regulators.
Real-World Security Statistics (Quick-Commerce Apps)
- A significant percentage of consumer app breaches originate from API vulnerabilities
- Location-based services rank among the most targeted app categories
- Payment-related incidents remain the top cause of financial loss in on-demand apps
- Regulators are issuing higher fines for improper consent and data storage practices
These numbers make one thing clear: security is no longer optional or secondary for white-label Blinkit apps.
Key Security Risks & How to Identify Them
High-Risk Area 1: Data Protection & Privacy
User Personal Information
A white-label Blinkit app collects names, phone numbers, addresses, and order histories. If this data is stored without encryption or proper access controls, it becomes an immediate liability. Poor role-based access often allows internal misuse or accidental exposure.
Payment Data Security
Although payments are usually processed through gateways, insecure implementations can still expose transaction metadata, payment tokens, or webhook endpoints. This is one of the fastest ways apps fail compliance audits.
Location Tracking Concerns
Real-time location data of users and delivery partners is highly sensitive. Weak protection can lead to stalking risks, data resale, or regulatory violations under privacy laws.
GDPR and Regional Privacy Compliance
Non-compliance with GDPR, CCPA, or similar laws often happens due to:
- Missing consent logs
- Undefined data retention policies
- No user data deletion mechanisms
These gaps expose founders to fines and legal action.
High-Risk Area 2: Technical Vulnerabilities
Code Quality Issues
Low-quality or reused code increases the risk of:
- SQL injection
- Cross-site scripting
- Authentication bypass
White-label does not excuse poor engineering.
Server and Infrastructure Security Gaps
Common issues include:
- Shared hosting environments
- No firewall rules
- Missing intrusion detection systems
These weaknesses make brute-force and DDoS attacks easier.
API Vulnerabilities
Blinkit-type apps rely heavily on APIs. If APIs lack:
- Proper authentication
- Rate limiting
- Input validation
Attackers can manipulate orders, pricing, or delivery assignments.
Third-Party Integrations
Maps, SMS, analytics, and payment services introduce risk if API keys are exposed or not rotated regularly.
High-Risk Area 3: Business and Operational Risks
Legal Liability
A single breach can trigger lawsuits, regulatory investigations, and contract terminations with merchants or partners.
Reputation Damage
Users rarely forgive apps that mishandle their data. Trust loss spreads faster than feature adoption.
Financial Losses
Security incidents lead to:
- Refunds and chargebacks
- Downtime losses
- Emergency remediation costs
Regulatory Penalties
Non-compliance fines in 2026 are larger, faster, and more public than ever before.
White-Label Blinkit App Risk Assessment Checklist
Data Security
- Is all user and order data encrypted at rest and in transit?
- Are access levels strictly role-based?
Infrastructure
- Are servers isolated per client?
- Is there active monitoring and alerting?
APIs
- Are APIs authenticated and rate-limited?
- Are request logs audited regularly?
Compliance
- Is GDPR and regional privacy compliance documented?
- Are consent and deletion flows implemented?
If any of these answers are unclear, the app carries high hidden risk.
READ MORE : – Top Blinkit App Features Powering 10-Minute Delivery
Security Standards Your White-Label Blinkit App Must Meet
Essential Security Certifications
ISO 27001 Compliance
ISO 27001 ensures that the provider follows a structured information security management system. For a white-label Blinkit app, this means data access policies, risk management processes, and continuous security improvement are formally documented and audited.
Core Technical Security Requirements
End-to-End Encryption
All data transfers between user apps, delivery partner apps, merchant panels, and admin dashboards must be encrypted using modern protocols.
Secure Authentication Mechanisms
Security in 2026 demands:
- Strong password policies
- Token-based authentication
- Two-factor authentication for admins and merchants
Regular Security Audits
Security is not a one-time setup. A safe white-label Blinkit app undergoes periodic audits to identify new vulnerabilities.
Penetration Testing
Ethical hacking tests must be conducted to simulate real-world attacks and fix weaknesses before they are exploited.
SSL Certificates
Every endpoint, panel, and API must enforce HTTPS with valid SSL certificates.
Secure API Design
APIs must implement:
- Authentication and authorization
- Input validation
- Rate limiting
- Error handling without data exposure
Security Standards Comparison Overview
Basic Provider
- Limited or no certifications
- Shared infrastructure
- Minimal audit practices
Enterprise-Grade Provider
- ISO and SOC compliance
- Isolated infrastructure per client
- Continuous monitoring and testing
Only the second category meets modern expectations for a production-ready white-label Blinkit app.
Red Flags: How to Spot Unsafe White-Label Providers
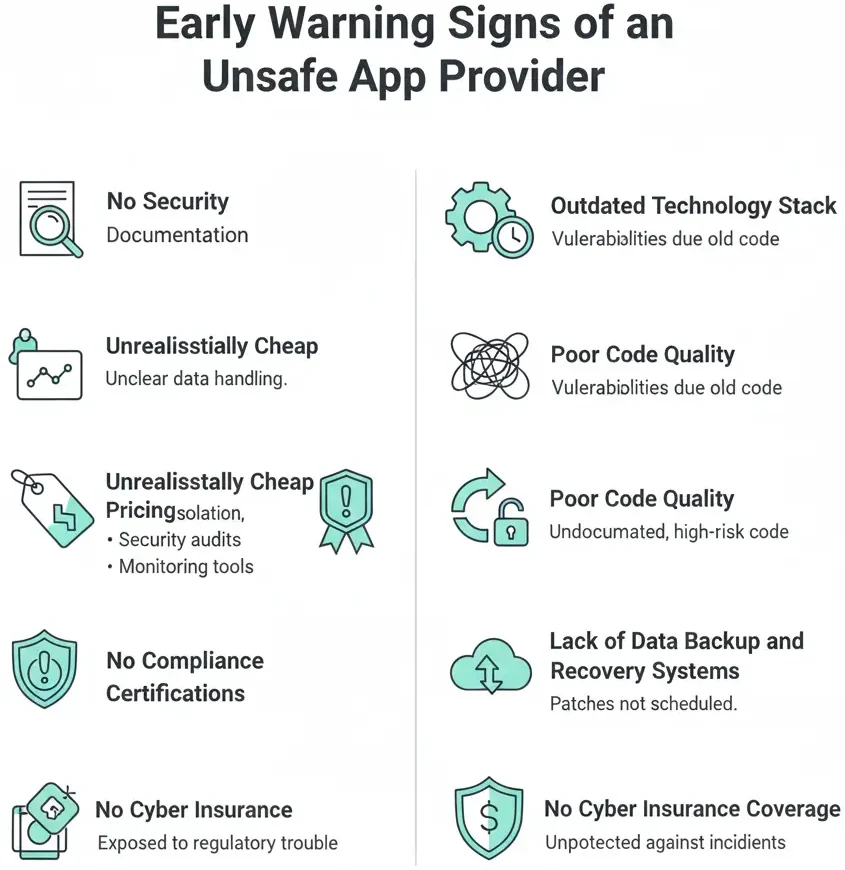
Critical Warning Signs You Should Never Ignore
No Security Documentation
If a provider cannot clearly explain how data is stored, encrypted, and accessed, it indicates a lack of mature security practices.
Unrealistically Cheap Pricing
Low pricing without a technical breakdown often means compromises on:
- Server isolation
- Security audits
- Monitoring tools
Security always has a cost.
No Compliance Certifications
Providers who dismiss ISO, SOC, or GDPR requirements expose you to future regulatory trouble.
Outdated Technology Stack
Old frameworks and unsupported libraries are common entry points for attackers.
Poor Code Quality
Messy, undocumented code increases the risk of vulnerabilities and makes audits difficult.
No Security Update Policy
If updates are “on request” instead of scheduled, vulnerabilities remain unpatched for long periods.
Lack of Data Backup and Recovery Systems
Without automated backups, a breach or failure can permanently destroy business data.
No Cyber Insurance Coverage
Professional providers carry insurance to protect clients against unforeseen incidents.
Evaluation Checklist Before Choosing a Provider
Questions You Must Ask
- How is user and order data encrypted?
- Are databases isolated per client?
- How often are security audits conducted?
- What happens if a breach occurs?
Documents You Should Request
- Security architecture overview
- Compliance certificates
- Audit and penetration test summaries
- Incident response policy
Testing You Should Perform
- Vulnerability scans
- API behavior testing
- Admin access reviews
Due Diligence Steps
- Verify past deployments
- Check breach history
- Review support response protocols
A provider who hesitates here is signaling high operational risk.
Best Practices for Secure White-Label Blinkit App Implementation
Pre-Launch Security Preparation
Comprehensive Security Audit
Before launch, the white-label Blinkit app should undergo a full audit covering application code, APIs, server configuration, and data storage practices. This ensures vulnerabilities are identified before real users interact with the system.
Structured Code Review
Every module must be reviewed for secure coding practices, especially authentication, order processing, wallet logic, and delivery assignment flows.
Infrastructure Hardening
Security-focused infrastructure includes:
- Isolated cloud environments
- Firewalls and access rules
- Secure admin access with IP restrictions
Compliance Verification
Confirm that privacy policies, consent flows, and data handling practices meet regional regulations where the app will operate.
Internal Staff Training
Admins and support teams should be trained on:
- Secure access handling
- Data privacy responsibilities
- Incident reporting procedures
Post-Launch Security Monitoring
Continuous Security Monitoring
Real-time monitoring helps detect suspicious activity such as login anomalies, API abuse, or unusual order behavior.
Regular Updates and Patch Management
Security patches must be deployed on a fixed schedule to address new vulnerabilities as they emerge.
Incident Response Planning
A documented response plan ensures quick containment, user communication, and regulatory reporting if an incident occurs.
User Data Lifecycle Management
Data retention, anonymization, and deletion policies must be enforced automatically to remain compliant.
Backup and Disaster Recovery
Automated backups and tested recovery plans protect the business from ransomware and system failures.
Security Implementation Timeline Overview
Before Launch
- Security audit and penetration testing
- Compliance and policy validation
- Infrastructure hardening
After Launch
- Continuous monitoring
- Regular audits and updates
- Ongoing compliance reviews
Security is a continuous process, not a one-time setup.
Legal & Compliance Considerations
Regulatory Requirements for Blinkit-Type Apps
Data Protection Laws by Region
White-label Blinkit apps often operate across cities or countries, making compliance region-specific. Common requirements include:
- GDPR for European users
- CCPA and CPRA for users in California
- DPDP Act for users in India
Each law defines how personal data is collected, stored, processed, and deleted.
Industry-Specific Regulations
Quick-commerce apps may also face:
- Consumer protection laws
- E-commerce marketplace regulations
- Food safety and pharmacy delivery rules in certain regions
Ignoring these can halt operations overnight.
User Consent Management
Explicit consent must be recorded for:
- Location tracking
- Marketing communication
- Data sharing with third parties
Consent logs are often required during audits.
Privacy Policy Requirements
A compliant privacy policy must clearly explain:
- What data is collected
- Why it is collected
- How long it is stored
- How users can request deletion
Terms of Service Essentials
Terms must define responsibilities of users, merchants, and delivery partners, along with dispute resolution mechanisms.
Liability and Risk Protection
Cyber Insurance Coverage
Insurance protects founders against financial losses caused by breaches, downtime, or legal claims.
Legal Disclaimers
Clear disclaimers limit exposure when external services or delivery partners are involved.
User Agreements
Strong agreements help transfer certain operational risks while remaining compliant with local law.
Incident Reporting Protocols
Most regulations require notifying authorities and users within strict timelines after a breach.
Ongoing Compliance Monitoring
Regulations change frequently. Continuous legal review is essential for long-term operations.
Regional Compliance Checklist Overview
Global
- Data encryption and access control
- Breach notification processes
Europe
- GDPR compliance
- Data processing agreements
India
- DPDP Act compliance
- Local data handling disclosures
United States
- State-level privacy compliance
- Consumer rights enforcement
Why Miracuves White-Label Blinkit App Is Your Safest Choice
Miracuves Security-First Architecture
Miracuves designs every white-label Blinkit app with security as a core architectural layer, not an afterthought. The platform is built to handle high-frequency orders, real-time location tracking, and sensitive payment workflows without exposing data or system integrity.
Enterprise-Grade Security Advantages
Hardened Infrastructure by Design
Each app deployment runs in an isolated environment, reducing cross-client risk and improving incident containment.
Certified Security and Compliance Practices
Miracuves follows globally recognized security frameworks and aligns app deployments with GDPR, CCPA, and regional data protection requirements by default.
Encrypted Data Transmission
All communication between user apps, delivery partner apps, merchant dashboards, and admin panels is encrypted using modern security protocols.
Secure Payment Processing
Payment flows are integrated with compliant gateways, ensuring transaction data is never exposed or stored improperly.
Continuous Monitoring and Audits
Security monitoring runs continuously, supported by scheduled audits and vulnerability assessments.
Regular Security Updates
Updates and patches are rolled out proactively to protect against newly discovered vulnerabilities.
Incident Readiness and Risk Coverage
Defined incident response procedures and insurance coverage help minimize business impact if an issue arises.
Why This Matters for Founders
A white-label Blinkit app is not just a product launch. It is a trust contract with users, merchants, and regulators. Miracuves reduces founder risk by embedding enterprise-level security controls from day one, allowing you to scale confidently without hidden liabilities.
Conclusion
Don’t compromise on security. Miracuves white-label Blinkit app solutions are built with enterprise-grade protection, compliance readiness, and operational resilience. With hundreds of successful deployments and a strong security track record, Miracuves helps businesses launch fast without sacrificing safety. Get a free security assessment and understand how your Blinkit-style app can meet 2026 security and compliance expectations from the start.
Security is not a feature you add later to a white-label Blinkit app. It is the foundation that determines whether your business earns trust or loses it. In 2026, users, regulators, and partners expect on-demand grocery apps to handle data responsibly, transparently, and securely.
FAQs
1. How secure is a white-label Blinkit app compared to custom development?
A well-built white-label Blinkit app can be as secure as, or more secure than, a custom-built app when it follows certified security standards, audited codebases, and hardened infrastructure. Security depends on architecture and compliance, not development method.
2. What happens if there is a security breach?
A secure provider follows a documented incident response process that includes breach containment, investigation, regulatory notification, and user communication within required timelines.
3. Who is responsible for security updates?
The app provider is responsible for core security updates, while the business owner must ensure timely deployment and adherence to operational security practices.
4. How is user data protected in a white-label Blinkit app?
User data is protected through encryption, role-based access control, secure APIs, and compliance-driven data retention and deletion policies.
5. Which compliance certifications should I look for?
You should prioritize ISO 27001, SOC 2 Type II, GDPR compliance, and PCI DSS for payment processing.
6. Can white-label Blinkit apps meet enterprise security standards?
Yes, enterprise-grade white-label apps are designed to meet the same security and compliance standards used by large-scale platforms.
7. How often should security audits be conducted?
Security audits should be conducted at least annually, with vulnerability assessments performed more frequently.
8. What is included in the Miracuves security package?
Miracuves includes encrypted infrastructure, compliance-aligned architecture, continuous monitoring, regular audits, secure payment integration, and incident readiness.
9. How is security handled across different countries?
Security is managed through region-specific compliance configurations, localized data handling practices, and adaptable privacy policies.
10. What insurance is needed for app security?
Cyber liability insurance is recommended to cover data breaches, downtime losses, legal costs, and regulatory penalties.
Related Articles:








