You’ve heard the horror stories about data breaches, leaked chats, fake profiles, and apps getting banned overnight. And if you’re planning to launch a white-label Bumble app, one question will keep coming back:
“Is it actually safe?”
In 2026, safety is not just a “nice to have.” Dating apps handle some of the most sensitive user data in the world: private messages, identity details, location, preferences, photos, and sometimes even payment information. That makes them a prime target for hackers, scammers, and compliance violations.
The good news is this:
A white-label Bumble app can be safe in 2026, but only if you treat security like a core product feature, not an afterthought.
In this guide, I’ll give you an honest assessment of the risks, the security standards you must meet, and the exact checklist you should follow before launching. I’ll also explain how Miracuves approaches white-label app security with a “security-first” mindset so your platform is built for trust, compliance, and long-term growth.
Understanding White-Label Bumble App Security Landscape (2026)
A white-label Bumble app can look like a premium dating platform on the surface, but the real difference between a “good-looking app” and a “safe app” is what’s happening behind the scenes.
In 2026, users are more aware than ever about privacy, scams, and data leaks. They may download your app for matches, but they stay only when they trust you.
What “White-Label Security” Actually Means
White-label security means your app is built using a ready-made foundation (codebase + core modules), but the responsibility for protecting user data still remains yours.
Security in a white-label Bumble app includes:
- Secure backend architecture (servers, databases, APIs)
- Secure app code (no loopholes or weak logic)
- Secure user flows (login, chat, reporting, blocking)
- Secure data handling (photos, location, messages, preferences)
- Secure compliance setup (privacy laws, consent rules, data deletion)
So even if you buy a white-label solution, you must ensure the provider delivers security-ready infrastructure, and you must operate it responsibly after launch.

Why People Worry About White-Label Bumble Apps
Dating apps trigger stronger fear compared to ecommerce or content apps because the damage is personal.
Users worry about:
- Chat leaks and screenshot scandals
- Fake profiles, catfishing, and romance scams
- Location tracking misuse
- Private photo misuse
- Identity exposure
- Harassment, stalking, and abuse
- Weak moderation and reporting tools
- Data being sold or shared without consent
In 2026, these concerns are not “overthinking.” These are real risks that have destroyed brands and created legal issues.
Current Threat Landscape for Bumble-Type Platforms (2026)
A Bumble-type dating platform faces both cyber threats and human abuse threats.
Cyber threats
- Credential stuffing (using leaked passwords from other sites)
- Account takeovers (OTP bypass, weak login protection)
- API abuse (scraping profiles, extracting user data)
- Malware and phishing through chat links
- Cloud misconfigurations exposing databases
Platform abuse threats
- Fake accounts and bots
- Fraudsters targeting users emotionally and financially
- Harassment and inappropriate content
- Underage users bypassing age checks
- Revenge reporting and false flags
A secure Bumble-type app in 2026 must defend against both categories.
Security Standards in 2026 (What Users Expect)
In 2026, “secure dating app” means:
- Strong authentication (OTP + optional 2FA)
- Encrypted chat and secure media storage
- Privacy-first profile controls
- Anti-bot protection
- Verified profiles and identity checks
- Fast abuse reporting + action tracking
- Clear data deletion policies
- Regular security patching
- Compliance-ready privacy framework
The biggest shift in 2026 is that security is now a trust feature, not just a backend task.
Real-World Statistics on App Security Incidents (2026)
In 2026, mobile apps remain a major target for cyberattacks, and platforms handling personal and location-based data are high-risk categories.
Common patterns seen across the industry include:
- A large share of breaches happening due to weak credentials and reused passwords
- Many app leaks caused by misconfigured cloud storage or exposed databases
- Dating and social apps being frequent targets for data scraping and fake profile networks
- Increased regulatory actions when user consent and data deletion are mishandled
Even when companies don’t face “headline breaches,” smaller leaks like exposed APIs, unsecured media URLs, or weak admin panels still create serious damage.
Read more : – Bumble App Features Every Startup Should Know
Key Security Risks & How to Identify Them (White-label Bumble App) – 2026
When people ask “Is a white-label Bumble app safe in 2026?”, the honest answer is:
It depends on what risks you are exposed to, and whether your app is built to handle them from day one.
Dating platforms are high-risk because they combine private communication, personal identity, location data, and user-generated content. That combination attracts hackers, scammers, and even legal scrutiny.
Below are the key risk areas you must evaluate before launching.
High-Risk Area 1: Data Protection & Privacy
User Personal Information (PII)
A Bumble-type dating app collects sensitive data like:
- Name, email, phone number
- Gender, preferences, age
- Photos and profile details
- Messages and interactions
- Device data and IP address
Risk in 2026: If your database or APIs are weak, attackers can extract this information and sell it.
How to identify the risk
- Check if data is encrypted at rest in the database
- Ensure role-based access control for admin panels
- Verify that APIs don’t expose extra user fields
Payment Data Security
Many dating apps monetize via subscriptions, boosts, premium plans, and in-app purchases.
Risk in 2026: If you store card data directly or handle payments insecurely, you create a major liability.
What safe apps do
- Use PCI DSS-compliant payment gateways
- Tokenize payment information
- Avoid storing raw card details in your servers
Location Tracking Concerns
Dating apps often use location for matching and discovery.
Risk in 2026: Poor location security can lead to stalking risks, user harassment, or legal complaints.
How to identify the risk
- Make sure location is not exposed in API responses
- Use approximate location display (not exact coordinates)
- Add privacy controls like “hide distance” or “incognito mode”
GDPR / CCPA Compliance
Even if you operate locally, users may come from regions with strict privacy laws.
Risk in 2026: Compliance failures can lead to legal action, platform bans, or penalties.
Key compliance requirements
- Consent collection for data usage
- Right to delete account and data
- Right to export user data
- Transparent privacy policy and terms
High-Risk Area 2: Technical Vulnerabilities
Code Quality Issues
White-label apps can be risky if they are rushed or copied without secure coding practices.
Common problems
- Hardcoded API keys
- Weak password validation
- Insecure file uploads
- No input validation
- Poor session management
How to identify the risk
- Run a secure code review
- Scan for secrets in code repositories
- Ensure proper error handling (no sensitive logs exposed)
Server Security Gaps
Many breaches happen not because the app is bad, but because the server is misconfigured.
Common server risks
- Open database ports
- Weak admin credentials
- No firewall rules
- No DDoS protection
- Unpatched server software
How to identify the risk
- Perform cloud security audit (AWS/GCP/Azure)
- Check firewall and security group configuration
- Ensure automated patching policy exists
API Vulnerabilities
Dating apps depend heavily on APIs (matching, chat, profile browsing, payments, reporting).
Major API risks in 2026
- Broken authentication
- Broken access control (users seeing other users’ data)
- Rate-limit missing (scraping attacks)
- Weak token handling
How to identify the risk
- Penetration testing focused on API endpoints
- Test for IDOR vulnerabilities (Insecure Direct Object References)
- Implement rate limiting and bot protection
Third-Party Integrations
A Bumble-type app often integrates:
- OTP providers
- Push notifications
- Payment gateways
- Analytics tools
- Maps/location services
- Content moderation tools
Risk in 2026: One insecure integration can expose your entire platform.
How to identify the risk
- Review third-party compliance and security documentation
- Use least-privilege access for API keys
- Rotate keys regularly
High-Risk Area 3: Business Risks
Legal Liability
If users get harmed due to weak security or poor safety controls, you may face legal complaints.
High-liability areas in 2026
- Fake profiles scamming users
- Underage access
- Harassment and stalking incidents
- Data leak or exposure
Reputation Damage
Dating apps rely on trust more than almost any other category.
Even one incident can cause:
- Bad reviews
- Social media backlash
- Influencer criticism
- App store removals
Financial Losses
Security failures create direct costs:
- Refunds and chargebacks
- Legal fees
- Incident recovery cost
- Infrastructure downtime
- Marketing spend wasted due to lost trust
Regulatory Penalties
Privacy laws in 2026 are stricter and more enforced.
Violations may lead to:
- Heavy fines
- Mandatory audits
- Forced changes in user data handling
- Region-based restrictions
Risk Assessment Checklist (White-label Bumble App) – 2026
Use this checklist before you launch:
Data & Privacy
- User data encrypted at rest and in transit
- Secure media storage for photos and uploads
- Privacy controls available (hide profile, hide distance, block/report)
- Clear consent flow for data usage
- Data deletion and export feature available
Authentication & Accounts
- OTP login supported
- Optional 2FA for high-risk accounts
- Strong session/token security
- Protection against brute-force login attempts
API & Backend
- APIs protected with access control
- Rate limiting enabled
- No sensitive fields exposed in responses
- Penetration testing completed
- Logs do not store private user data
Infrastructure
- Firewall + WAF configured
- Database access restricted
- Backups enabled and tested
- DDoS protection active
- Monitoring and alerts enabled
Platform Abuse Protection
- Fake profile detection and controls
- Verified profiles (optional but recommended)
- Anti-bot measures
- Reporting + moderation workflow
- Age verification support
Read more : – Bumble Marketing Strategy | Swiping Right on Growth
Security Standards Your White-Label Bumble App Must Meet (2026)
If you want your white-label Bumble app to be trusted in 2026, security cannot be “basic protection.” It must meet real-world compliance expectations and modern technical standards.
This section will help you understand what standards actually matter, which ones are mandatory, and which ones are strong trust signals for investors, enterprise partners, and even app store approvals
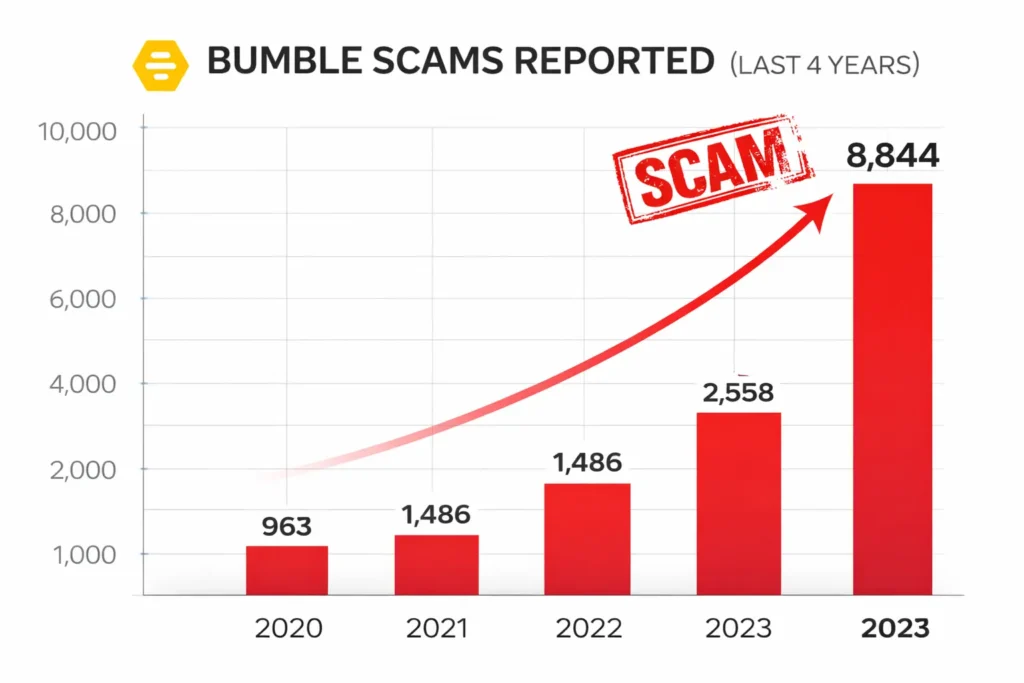
Essential Certifications & Compliance Frameworks (2026)
ISO 27001 Compliance
ISO 27001 is one of the most respected global standards for Information Security Management Systems (ISMS).
Why it matters for a Bumble-type app in 2026
- Shows structured security governance
- Improves internal security controls
- Builds credibility for partnerships and enterprise clients
Best for
- Businesses planning long-term scale
- Companies working with international users
- Brands that want strong investor trust
SOC 2 Type II
SOC 2 Type II focuses on how consistently a company protects data over time (not just one-time checks).
Why it matters in 2026
- Demonstrates operational security maturity
- Covers security, availability, confidentiality, privacy
- Builds strong trust with B2B partners
Best for
- Apps with premium memberships and recurring revenue
- Platforms expanding globally
- Brands aiming for corporate-grade compliance
GDPR Compliance
GDPR applies to any app that handles data of users in the European Union.
Why it matters for dating apps in 2026
Dating apps handle sensitive personal data and behavior patterns, which increases compliance expectations.
Key GDPR requirements
- Lawful basis for data processing
- Clear consent collection
- Right to access and delete user data
- Data minimization and purpose limitation
- Breach notification processes
HIPAA (If Applicable)
HIPAA is not usually required for dating apps. But in 2026, some relationship or wellness-focused dating platforms integrate therapy, counseling, or health-related features.
HIPAA may apply if your app includes
- Medical data storage
- Mental health records
- Healthcare provider partnerships
If your white-label Bumble app is purely dating + chat, HIPAA is usually not required.
PCI DSS for Payments
If your app accepts payments for subscriptions, boosts, or premium features, PCI DSS matters.
Important note for 2026
You should avoid storing card details yourself. The best practice is using PCI-compliant payment gateways that tokenize payments.
Why PCI DSS matters
- Prevents payment fraud exposure
- Reduces legal risk
- Helps with app store trust and user confidence
Technical Security Requirements (Must-Have in 2026)
End-to-End Encryption (Where Possible)
For dating apps, encryption is essential for:
- Login data
- Chat messages
- Photo uploads
- Sensitive profile information
In 2026, users expect private communication to be protected. Even if full end-to-end encryption is not implemented for every feature, strong encryption in transit and secure storage are mandatory.
Secure Authentication (2FA / OAuth / OTP)
A white-label Bumble app should support secure login options like:
- OTP login (phone-based)
- OAuth (Google / Apple sign-in)
- Optional 2FA for extra protection
- Strong session and token management
This reduces account takeovers and makes credential-stuffing attacks harder.
Regular Security Audits
Security audits should not be “one-time before launch.”
In 2026, safe apps follow:
- Quarterly security review
- Dependency vulnerability checks
- Infrastructure audit
- Admin panel access review
Penetration Testing
Penetration testing (pentesting) is one of the strongest security validations.
What it checks
- API vulnerabilities
- Broken access control
- Authentication weaknesses
- File upload exploits
- Database exposure risks
For Bumble-type apps, pentesting should focus heavily on APIs, chat systems, and admin panels.
SSL Certificates and Secure HTTPS
This is non-negotiable in 2026.
Minimum requirement
- HTTPS across the entire platform
- HSTS enabled
- Secure TLS configuration
Secure API Design
APIs are the heart of a dating app. Secure design must include:
- Proper authentication and authorization
- Role-based access control
- Rate limiting to stop scraping
- Input validation to stop injections
- Encrypted tokens and secure session expiry
Security Standards Comparison Table (2026)
| Standard / Requirement | What It Protects | Mandatory for White-label Bumble App in 2026? | Best For |
|---|---|---|---|
| ISO 27001 | Security governance and controls | Recommended | Global scale + investor trust |
| SOC 2 Type II | Ongoing security operations | Recommended | Enterprise-level credibility |
| GDPR | Privacy + user data rights | Mandatory if EU users exist | Global privacy compliance |
| CCPA | Consumer data rights (California) | Mandatory if US users exist | US expansion |
| PCI DSS | Payment data security | Mandatory if payments exist | Premium subscriptions |
| Penetration Testing | Finds real exploitable weaknesses | Strongly recommended | Preventing breaches |
| End-to-end encryption | Protects chat and sensitive data | Recommended | Trust and privacy |
| 2FA / OTP / OAuth | Prevents account takeover | Strongly recommended | Safer logins |
| Secure API design | Prevents scraping and leaks | Mandatory | Dating app stability |
| Security audits | Prevents long-term exposure | Strongly recommended | Continuous safety |
Red Flags: How to Spot Unsafe White-Label Providers (2026)
In 2026, the biggest security risk for a white-label Bumble app is not “hackers first.”
It is choosing the wrong provider in the first place.
Many unsafe providers sell attractive demos, but behind the design, the product is built on weak security foundations. And when you launch, you inherit all those risks.
This section will help you identify the warning signs early, so you don’t invest money into a platform that becomes a legal, financial, and reputational problem later.
Warning Signs of Unsafe White-Label Providers (2026)
No Security Documentation
If a provider cannot share basic security documentation, it usually means security was never properly planned.
Red flag examples
- No security architecture overview
- No explanation of data storage and encryption
- No authentication security details
- No mention of compliance readiness
In 2026, a serious provider will have at least a basic security checklist ready.
Cheap Pricing Without Explanation
Low pricing is not always bad, but extremely cheap pricing often means:
- Old code reused repeatedly
- No secure coding process
- No audits or testing
- No long-term updates included
- Weak infrastructure setup
A Bumble-type dating app needs ongoing security work. If the provider’s pricing cannot support that, the risk is automatically higher.
No Compliance Certifications or Compliance Support
Even if your business doesn’t need ISO 27001 or SOC 2 Type II on day one, your provider must understand compliance.
Red flag
- “We don’t handle GDPR/CCPA, you manage it”
- “We don’t provide data deletion features”
- “We don’t support consent tracking”
In 2026, compliance is part of the product, not a side task.
Outdated Technology Stack
Old tech is not automatically insecure, but outdated frameworks often have:
- Known vulnerabilities
- Poor performance
- Weak dependency support
- Compatibility issues with modern security standards
Red flag signs
- No clear tech stack explanation
- No update roadmap
- No security patch policy
Poor Code Quality
A white-label Bumble app needs stable, secure code because the platform will be handling user interactions every second.
Red flags
- Frequent crashes or bugs in demo
- Slow API response
- Weak admin controls
- Hardcoded values and weak validations
- No code review process
No Security Updates Policy
In 2026, security is a continuous process. New vulnerabilities are discovered every month.
If a provider cannot answer:
- “How often do you release patches?”
that’s a serious risk.
Red flag
- One-time delivery with no maintenance plan
- No versioning
- No post-launch support process
Lack of Data Backup Systems
For a dating app, data loss is not only a technical problem, it is a business-ending problem.
Red flags
- No daily backups
- No disaster recovery plan
- No rollback options
- No monitoring alerts
No Insurance Coverage
This is an overlooked factor in 2026.
Many serious providers and enterprises use cyber liability insurance or professional liability coverage to reduce business exposure.
Red flag
- Provider has no risk coverage
- No security responsibility defined in contract
Evaluation Checklist: How to Verify a Provider is Safe (2026)
Questions to Ask Providers
Ask these directly before you sign:
- What security standards does your white-label Bumble app follow in 2026?
- Is user data encrypted in transit and at rest?
- Do you support GDPR and CCPA requirements by default?
- How do you protect APIs from scraping and abuse?
- What authentication methods are included (OTP, OAuth, 2FA)?
- Do you provide penetration testing reports or security audits?
- How often do you release security patches and updates?
- What is your incident response process if a breach happens?
- How do you handle backups and disaster recovery?
- Do you provide admin panel access control and audit logs?
A secure provider in 2026 will answer confidently and clearly.
Documents to Request
You don’t need a 200-page report. But you should request proof.
Ask for:
- Security architecture overview
- Data flow diagram (what data is collected and where it is stored)
- Encryption policy summary
- Privacy compliance checklist (GDPR/CCPA readiness)
- Penetration testing summary (if available)
- Maintenance and update policy document
- Backup and disaster recovery plan
If they refuse to share anything, it’s a strong warning sign.
Testing Procedures You Should Run
Even before launch, you can validate the app’s safety.
Minimum testing in 2026
- Vulnerability scan (app + backend)
- API rate-limit testing
- Login brute-force protection testing
- File upload security testing
- Admin panel security testing
- Basic penetration testing by a security team
Due Diligence Steps (Simple but Powerful)
Before selecting a provider, do this:
- Review their past projects (not just screenshots)
- Ask for real deployment examples
- Verify hosting security approach
- Confirm post-launch support and patching
- Ensure compliance features exist inside the product
- Check contract terms for security responsibilities
In 2026, due diligence is what separates safe launches from risky launches.
Best Practices for Secure White-Label Bumble App Implementation (2026)
Buying a white-label Bumble app is only step one.
In 2026, real safety comes from how you implement, configure, and operate the platform after you receive it.
Many businesses fail not because their provider is completely unsafe, but because they launch without doing the security work that should happen before and after release.
This section gives you a practical security playbook you can follow.
Pre-Launch Security (What to Do Before Going Live in 2026)
Security Audit Process
Before launch, you should treat your app like a system that is already under attack.
A proper security audit should include:
- Authentication and login security review
- API security validation (access control + rate limiting)
- Database and storage security checks
- Admin panel access control audit
- User privacy controls review (block, report, hide profile)
In 2026, skipping a security audit is one of the biggest reasons dating apps face early incidents.
Code Review Requirements
Even if you are not a technical founder, you should insist on code review standards.
A secure white-label Bumble app should be checked for:
- Hardcoded keys or secrets
- Weak password handling
- Unsafe file uploads
- Missing input validation
- Logging of sensitive data (messages, phone numbers, OTPs)
- Broken authorization checks
Code review is not about perfection. It’s about removing the obvious weaknesses before real users join.
Infrastructure Hardening
Your server and hosting setup is just as important as the app itself.
Infrastructure hardening should include:
- Firewall and security rules configured
- Database ports closed to public access
- Secure environment variables management
- Web Application Firewall (WAF) enabled
- DDoS protection setup
- Admin panel restricted by IP or VPN access
- Monitoring and alerts enabled
In 2026, many breaches happen because the cloud setup was “default,” not hardened.
Compliance Verification
A Bumble-type app in 2026 must prove it handles user data responsibly.
Before launch, confirm:
- Privacy policy and terms are ready
- Consent collection is implemented properly
- Data deletion flow is working (account delete + erase data)
- Data export option exists (if required by region)
- Cookies and tracking disclosures are accurate (if web admin panel exists)
Compliance is not only legal protection. It’s user trust protection.
Staff Training Programs
Even the best security system fails if people use it incorrectly.
Train your team on:
- Admin access best practices
- Strong password management
- Social engineering awareness
- Handling user reports and abuse cases
- Safe data access policies
- Incident escalation process
In 2026, internal mistakes are still a top cause of security incidents.
Post-Launch Monitoring (How to Stay Secure After Launch in 2026)
Continuous Security Monitoring
Security is not a one-time checklist. It is ongoing.
You should monitor:
- Login attempts and suspicious activity
- Fake profile creation spikes
- Bot-like swiping behavior
- API traffic anomalies
- Database access logs
- Admin panel activity logs
In 2026, early detection is the difference between “small issue” and “public crisis.”
Regular Updates and Patches
Your app will need updates for:
- New vulnerabilities in libraries
- OS-level patches on servers
- Security improvements in authentication
- Fraud and bot prevention upgrades
A safe white-label Bumble app must have a clear patching cycle.
Recommended minimum in 2026:
- Monthly security patch review
- Emergency patches within 24–72 hours for critical issues
Incident Response Planning
If a breach or abuse incident happens, your response speed matters more than the event itself.
Your incident response plan should define:
- Who detects and confirms the issue
- Who has authority to lock systems
- How you notify affected users
- How you preserve logs and evidence
- How you report to regulators if required
- How you communicate publicly without panic
In 2026, platforms that respond fast protect trust. Platforms that hide issues lose users permanently.
User Data Management
A dating app is extremely sensitive because users share private conversations and identity details.
Your operational rules should include:
- Minimal data collection (only what’s needed)
- Limited internal access to user data
- Clear data retention rules
- Secure deletion and cleanup policy
- Safe media storage and access control
In 2026, “data minimization” is one of the strongest security strategies.
Backup and Recovery Systems
Backups protect you from:
- Data loss
- Ransomware attacks
- Human mistakes
- Infrastructure failures
A safe setup includes:
- Daily automated backups
- Encrypted backups
- Separate backup storage location
- Regular restore testing (not just backup creation)
In 2026, a backup that cannot be restored is not a backup.
Security Implementation Timeline (White-label Bumble App) – 2026
Week 1: Security Foundation Setup
- Infrastructure hardening
- SSL/HTTPS verification
- Admin panel restrictions
- Basic monitoring enabled
Week 2: App-Level Security Validation
- Code review
- Authentication testing
- API security testing
- Data encryption verification
Week 3: Compliance + Abuse Safety Controls
- GDPR/CCPA readiness checks
- Privacy policy + consent flow
- Reporting and moderation workflow testing
- Fake profile prevention setup
Week 4: Final Testing + Launch Readiness
- Penetration testing
- Load testing + DDoS readiness
- Backup restore drill
- Incident response plan finalization
After launch:
- Monthly security patch cycles
- Quarterly audits
- Continuous monitoring and fraud detection improvements
Legal & Compliance Considerations (White-label Bumble App) – 2026
Security is not only a technical topic in 2026.
For a Bumble-type dating platform, legal and compliance issues are directly connected to user trust, app store approval, and long-term business survival.
If you ignore compliance, even a “technically secure” white-label Bumble app can still become unsafe from a business perspective.
Regulatory Requirements (2026)
Data Protection Laws by Region
Different regions have different privacy rules. In 2026, you must plan based on where your users live, not just where your company is registered.
Common compliance expectations include:
- Clear consent for data collection and processing
- User rights to access, edit, and delete data
- Transparency about how data is used
- Strong protection for sensitive personal information
- Breach reporting obligations
European Union (GDPR)
If your app has EU users, GDPR is a major requirement.
Key obligations in 2026:
- Clear consent before processing user data
- Right to access and download user data
- Right to delete user data (full erasure)
- Privacy policy that explains purpose and retention
- Data processing agreements with third parties
- Breach notification procedures
GDPR also expects “privacy by design,” meaning your app must be built with privacy controls inside the product.
United States (CCPA and State-Level Laws)
In 2026, the US privacy landscape is more complex because multiple states have their own rules.
Common requirements:
- Inform users what data is collected
- Allow users to request deletion
- Allow users to opt out of data sharing (where applicable)
- Provide clear privacy disclosures
For dating apps, regulators also focus on how sensitive user behavior data is handled.
India (DPDP Act and Privacy Expectations)
In 2026, India’s privacy expectations are stronger, especially for platforms collecting personal data like photos, phone numbers, and location.
Key focus areas:
- User consent for data collection
- Safe handling of personal identifiers
- Secure storage and access control
- Clear policies for deletion and retention
For a Bumble-type app, these requirements matter because of identity and safety concerns.
Other Regions (General Compliance Patterns)
Even if laws differ, in 2026 most regulators expect:
- Consent-based data processing
- Secure storage and encryption
- User control over privacy settings
- Ability to delete data permanently
- Strong breach response process
If you want global expansion, compliance must be built into your app from the start.
Industry-Specific Regulations (Dating App Reality in 2026)
Dating platforms face extra scrutiny because of:
- User-generated content
- Harassment risks
- Fraud and scams
- Underage access risks
- Emotional harm and reputation risks
So compliance is not only about privacy laws. It is also about safety systems like moderation, reporting, and blocking.
User Consent Management (2026)
Consent is one of the most important legal foundations.
Your white-label Bumble app must support:
- Consent for profile visibility and matching
- Consent for location usage
- Consent for notifications and marketing communication
- Consent for analytics tracking (where applicable)
In 2026, consent must be clear, logged, and easy to withdraw.
Privacy Policy Requirements (2026)
A privacy policy is not just a website formality. It is a legal shield.
Your privacy policy should clearly explain:
- What data you collect (phone, photos, location, chat content)
- Why you collect it (matching, safety, fraud prevention)
- Where it is stored and how it is protected
- How long it is retained
- How users can delete or export data
- Which third parties receive data (payment gateways, cloud services)
- How you handle law enforcement requests
Terms of Service Essentials (2026)
Your terms protect you from misuse and define user responsibility.
A Bumble-type app should include:
- User eligibility rules (age restrictions)
- Prohibited content and behavior
- Anti-harassment policies
- Account termination conditions
- Payment and subscription rules
- Dispute resolution process
- Liability limitations (within legal boundaries)
In 2026, terms are also used to handle abuse cases quickly.
Liability Protection (2026)
Insurance Requirements
For dating platforms, insurance is becoming more common in 2026, especially for:
- Cyber liability coverage
- Data breach response coverage
- Business interruption coverage
- Professional liability coverage
This does not replace security, but it reduces financial risk if an incident happens.
Legal Disclaimers
Your app should clearly communicate:
- You cannot guarantee user behavior
- Users must follow safety practices
- The platform provides reporting and blocking tools
- The platform may remove accounts violating rules
These disclaimers help reduce legal exposure, especially in harassment or scam-related cases.
User Agreements and Responsibilities
In 2026, platforms are expected to actively enforce rules.
Your user agreement should cover:
- Identity misrepresentation consequences
- Scam and fraud prevention rules
- Prohibited messaging and content
- Reporting and investigation procedures
Incident Reporting Protocols
If something goes wrong, your legal process matters.
Your protocol should define:
- How users report issues
- How quickly you respond
- What actions you take (warn, suspend, ban)
- When you involve authorities (if required)
- How you notify users about major incidents
Regulatory Compliance Monitoring
Compliance is not “set and forget.”
In 2026, you should regularly review:
- Data retention practices
- Consent records
- Security logs
- Third-party integrations compliance
- Policy updates based on new regulations
Compliance Checklist by Region (2026)
| Region | Key Law / Focus | Must-Have Compliance Actions |
|---|---|---|
| EU | GDPR | Consent, data deletion, export, breach process, privacy by design |
| USA | CCPA + state privacy laws | Disclosure, deletion request, opt-out options, data access rights |
| India | DPDP + privacy expectations | Consent, secure storage, limited access, retention controls |
| Global | General privacy + safety | Strong encryption, user controls, reporting system, audit readiness |
Why Miracuves White-Label Bumble App is Your Safest Choice (2026)
If you’re investing in a white-label Bumble app in 2026, you’re not just buying an app.
You’re taking responsibility for user trust, privacy, safety, and compliance.
That’s why the smartest founders don’t choose providers based only on UI or speed. They choose providers who treat security as a product feature, not a last-minute add-on.
Miracuves positions itself as a security-first solution provider, meaning the app is built to protect users, protect your business, and support long-term growth.
Miracuves Security Advantages (2026)
Enterprise-Grade Security Architecture
Miracuves designs white-label Bumble app infrastructure with security at the core, including secure backend systems, controlled access, and safe data handling practices.
This reduces common risks like exposed databases, weak admin panels, and API leaks.
Regular Security Audits and Security-Ready Processes
In 2026, safe platforms require ongoing checks, not one-time fixes.
Miracuves focuses on structured security processes such as:
- Security reviews before launch
- Secure deployment practices
- Continuous improvement based on risk patterns
This helps ensure your app remains safe even as threats evolve.
GDPR/CCPA Compliant by Default
Privacy compliance is not optional in 2026.
Miracuves white-label Bumble app solutions are designed to support:
- User consent flows
- Data access and deletion requests
- Transparent privacy handling
- Compliance-ready data management
So you’re not forced to rebuild compliance later after users join.
24/7 Security Monitoring Mindset
A dating platform cannot be left unmonitored.
Miracuves follows a security-first approach that supports:
- Suspicious activity detection
- Login and abuse monitoring readiness
- System stability protection
In 2026, monitoring is one of the biggest differences between safe apps and vulnerable apps.
Encrypted Data Transmission
Your users’ messages, identity details, and media must be protected during transmission.
Miracuves ensures encrypted data transmission practices are part of the core security foundation so user data is not exposed in transit.
Secure Payment Processing
If your Bumble-type app includes subscriptions or premium upgrades, payment security becomes critical.
Miracuves supports secure payment processing practices aligned with PCI DSS expectations in 2026 by using secure gateways and safe handling of payment workflows.
Regular Security Updates
Security threats change constantly in 2026.
Miracuves focuses on regular updates so your platform does not stay stuck with outdated security controls, weak dependencies, or old vulnerabilities.
Insurance Coverage Included (Business Risk Protection)
For many businesses, insurance coverage is an important part of risk reduction.
Miracuves supports a security-first approach where business continuity and risk exposure are taken seriously, helping founders operate with more confidence.
Final thought
Don’t compromise on security. Miracuves white-label Bumble app solutions come with enterprise-grade security built-in. Our 600+ successful projects have maintained zero major security breaches. Get a free security assessment and see why businesses trust Miracuves for safe, compliant platforms.
A white-label Bumble app can be safe in 2026, but only when security is treated as a core foundation, not a feature added later. If you choose the right provider, follow compliance rules, and commit to continuous monitoring and updates, you can build a dating platform users genuinely trust.
FAQs
1. How secure is white-label vs custom development in 2026?
White-label apps can be just as secure as custom apps in 2026 if they follow strong security standards, secure coding, and regular audits. The real difference is the provider’s security maturity, not the development method.
2. What happens if there’s a security breach in 2026?
If a breach happens, you must act fast: isolate the issue, secure accounts, investigate logs, notify affected users, and report to regulators if required. A clear incident response plan reduces damage and protects trust.
3. Who is responsible for security updates in a white-label Bumble app in 2026?
Usually, the provider handles core app updates and patches, while you manage operational security like admin access, hosting configuration, and policy enforcement. The safest approach in 2026 is a shared responsibility model with clear support terms.
4. How is user data protected in white-label Bumble apps in 2026?
User data is protected through encryption, secure APIs, access control, and privacy-first data storage. Strong apps also include features like blocking, reporting, and profile visibility controls to protect users.
5. What compliance certifications should I look for in 2026?
In 2026, ISO 27001 and SOC 2 Type II are strong trust signals. GDPR and CCPA readiness are critical for privacy compliance, and PCI DSS is required if your app processes payments.
6. Can white-label Bumble apps meet enterprise security standards in 2026?
Yes. In 2026, white-label Bumble apps can meet enterprise standards if they include secure authentication, encryption, audits, penetration testing, and compliance-ready architecture.
7. How often should security audits be conducted in 2026?
At minimum, run security reviews monthly and perform full audits quarterly. Penetration testing should be done before launch and repeated after major updates or feature releases.
8. What’s included in Miracuves security package for 2026?
Miracuves focuses on enterprise-grade architecture, encryption, compliance-ready design, secure payment handling, monitoring readiness, and regular security updates to keep the platform safe long-term.
9. How to handle security in different countries in 2026?
You must follow region-specific privacy laws, implement consent management, support user data deletion/export, and maintain clear policies. A compliance-first approach ensures your app remains legal across markets.
10. What insurance is needed for app security in 2026?
Most platforms use cyber liability insurance and data breach coverage to reduce financial exposure. It helps cover incident response costs, legal support, and business interruption losses.
Related Articles :








