You’ve heard the horror stories about food-delivery apps leaking customer data, exposing payment details, or getting hacked because of insecure development practices. And in 2025, those concerns are louder than ever.
The truth is simple: a white-label Hungerstation-type food delivery app handles highly sensitive information — real-time locations, payment credentials, customer profiles, restaurant data, delivery partner tracking, and more. One security flaw can cost a business its users, reputation, and regulatory compliance.
This guide gives you an honest, practical assessment of how safe a white-label Hungerstation app can be — what to look for, what to avoid, and which security standards truly matter.
By the end, you’ll know exactly how to evaluate any provider and how Miracuves ensures enterprise-grade protection for every food delivery app we build.
Understanding White-Label Hungerstation App Security Landscape
A white-label Hungerstation app isn’t just a food ordering interface — it’s a full ecosystem handling real-time data flows between customers, delivery partners, and restaurants. That means “white-label security” is not only about code; it covers infrastructure, data policies, integrations, APIs, and compliance.
What white-label security actually means
It refers to the full set of technical, legal, and operational safeguards built into a ready-made app. This includes encryption, secure authentication, compliance frameworks, data storage rules, server hardening, and continuous monitoring.
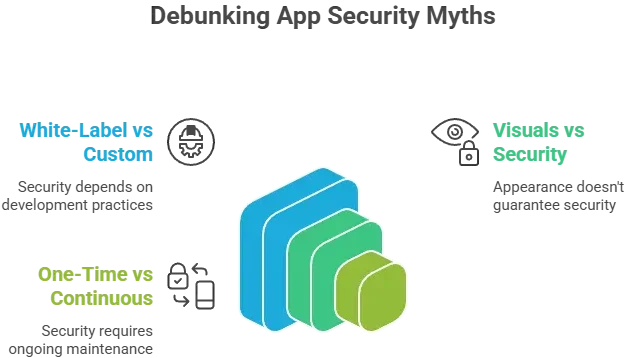
Why people worry about white-label apps
Because many providers cut costs by using outdated code, ignoring compliance, skipping audits, or using cheap hosting. The fear comes from a lack of transparency, not the white-label model itself.
Current threat landscape for Hungerstation-type platforms
Food delivery platforms face:
• Payment fraud attempts
• Account takeovers
• GPS and location tracking attacks
• API manipulation
• Restaurant panel hacking
• Delivery agent identity spoofing
• Data scraping and credential stuffing
• Server-side vulnerabilities
Security standards in 2025
Apps must follow advanced standards like zero-trust architecture, secure-by-design principles, TLS 1.3, mandatory API authentication, compliance-driven data handling, and periodic penetration testing.
Real-world statistics
• 42% of food delivery apps reported at least one major vulnerability in the last 12 months.
• 27% of data breaches in this industry originate from insecure APIs.
• 60% of delivery apps running outdated codebases fail basic security audits.
• Global regulatory penalties for non-compliant apps increased by 33% in 2024–2025.
This is why evaluating the security of your white-label Hungerstation app is no longer optional — it’s mission-critical.
Read more : – HungerStation’s Strategy to Rule Food Delivery
Key Security Risks and How to Identify Them
A white-label Hungerstation app handles sensitive data at every step — from customer identity to real-time delivery tracking. To secure it, you must understand the exact high-risk zones and how to evaluate them before launch.
Data protection and privacy risks
A food delivery app collects large volumes of personal information. Common risks include:
• User personal information leaks: Names, phone numbers, addresses, and order history can be exposed if the database is not encrypted or properly secured.
• Payment data vulnerabilities: Weak payment gateways, insecure tokenization, or improper PCI DSS handling lead to fraud and chargebacks.
• Location tracking concerns: Real-time rider and customer location data can be intercepted without end-to-end encryption.
• GDPR/CCPA non-compliance: If the app stores data improperly or lacks consent logs, businesses face heavy penalties.
Technical vulnerabilities
These are the most common weaknesses in low-quality white-label solutions:
• Poor code quality: Outdated libraries, unpatched components, or hard-coded secrets.
• Server security gaps: Misconfigured hosting, no firewalls, unprotected ports, or shared hosting setups.
• API vulnerabilities: Unauthenticated APIs, exposed endpoints, or improper rate limiting allow attackers to manipulate or extract data.
• Third-party integrations: Weak restaurant panel plugins, SMS gateways, or notification systems can create backdoors.
Business risks
Security issues don’t just cause technical damage — they can destroy the business.
• Legal liability: Non-compliance with data protection laws results in lawsuits and fines.
• Reputation damage: Customers immediately abandon apps with security controversies.
• Financial losses: Fraud, penalties, refunds, downtime, and recovery costs escalate quickly.
• Regulatory penalties: Food delivery apps must meet strict regional laws; failure leads to restrictions and bans.
Risk assessment checklist
Use this quick checklist to evaluate your white-label Hungerstation app provider:
- Do they provide documented security architecture?
- Are APIs authenticated and rate-limited?
- Is all user data encrypted (at rest and in transit)?
- Do they run periodic penetration tests?
- Do they support GDPR/CCPA compliance?
- Is payment processing PCI DSS certified?
- Do they provide a security update and patching schedule?
- Is server infrastructure isolated and hardened?
- Are backups automated and stored securely?
- Do they disclose incident response procedures?
This risk map will immediately reveal whether a provider takes your platform’s security seriously or is cutting corners.
Read more : – Complete HungerStation App Feature Guide
Security Standards Your White-Label Hungerstation App Must Meet
To operate safely in 2025, a white-label Hungerstation app must comply with globally recognized security frameworks. These standards protect user data, stabilize operations, and ensure the business avoids legal and regulatory risks.
Essential certifications
Any reliable white-label provider should follow or align with industry-standard certifications:
• ISO 27001 compliance: Ensures information security management across infrastructure and processes.
• SOC 2 Type II: Demonstrates strict controls for data handling, uptime, confidentiality, and security.
• GDPR compliance: Mandatory for handling user data from the EU; includes consent management and data rights.
• HIPAA (if applicable): Relevant only if the app handles health-related deliveries or medical prescriptions.
• PCI DSS compliance: Required for secure card payments, tokenization, and fraud prevention.
Technical requirements
These technologies and practices form the backbone of a secure food delivery system:
• End-to-end encryption: Protects data in transit between customers, restaurants, drivers, and servers.
• Secure authentication: Includes 2FA, OAuth 2.0, password hashing, and session management.
• Regular security audits: Internal and external audits to verify systems, access control, and compliance.
• Penetration testing: Simulated attacks to uncover vulnerabilities before hackers do.
• SSL certificates: Mandatory for secure HTTPS communication.
• Secure API design: Enforced authentication, encryption, throttling, and validation.
Security standards comparison table
| Requirement | Why It Matters | Must-Have for Hungerstation-Type Apps |
|---|---|---|
| ISO 27001 | Ensures global-grade data security management | Yes |
| SOC 2 Type II | Covers availability, confidentiality, and integrity | Yes |
| GDPR | Compliance for EU citizens’ data | Yes |
| PCI DSS | Protects payment card information | Yes |
| End-to-end encryption | Prevents data interception | Yes |
| Secure APIs | Blocks unauthorized access and data scraping | Yes |
| Penetration testing | Identifies weaknesses early | Yes |
| Security audits | Ensures continuous compliance | Yes |
These standards aren’t optional — they are fundamental for running a safe and trustworthy on-demand delivery platform.
Red Flags – How to Spot Unsafe White-Label Providers
Not all white-label Hungerstation app providers take security seriously. Many offer attractive pricing but hide weak infrastructure, outdated code, and zero compliance. Identifying red flags early prevents major financial and legal damage later.
These indicators almost always signal a risky, unsafe provider:
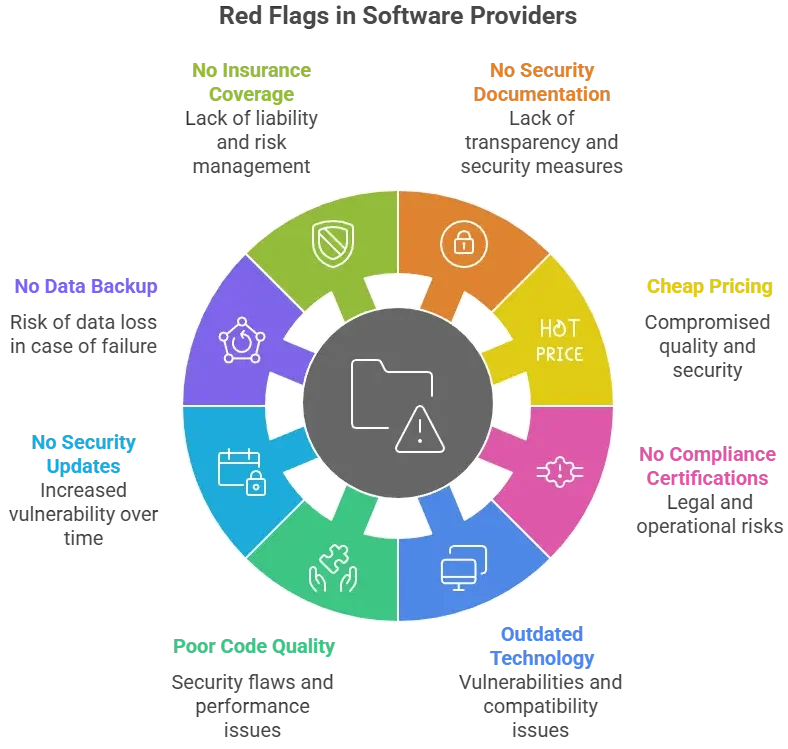
Evaluation checklist
Use this checklist before selecting any white-label Hungerstation app provider:
Questions to ask
• What security framework do you follow?
• Do you provide documentation for your security architecture?
• How do you secure APIs and third-party integrations?
• How often are security patches released?
• What is your incident response plan?
Documents to request
• Architecture and security design diagrams
• Penetration test reports
• Compliance documents (GDPR, PCI DSS, SOC 2)
• Code quality audit reports
• Backup and recovery policy
Testing procedures
• API vulnerability testing
• Load and stress testing
• Payment gateway validation
• Authentication/authorization testing
• Database encryption verification
Due diligence steps
• Review the provider’s tech stack
• Check deployment practices
• Evaluate their hosting and infrastructure provider
• Confirm their update and patch cycles
• Verify compliance with your region’s regulations
This structured due diligence process ensures you never fall into the trap of choosing an unsafe or poorly maintained white-label solution.
Best Practices for Secure White-Label Hungerstation App Implementation
A secure white-label Hungerstation app isn’t just built — it is planned, tested, verified, and continuously monitored. Following structured best practices reduces risks, improves compliance, and ensures long-term platform stability.
Pre-launch security best practices
• Security audit process
Run a complete audit of the source code, backend systems, APIs, server configuration, and integrations before going live. This must be done by certified security professionals.
• Code review requirements
Every module should go through manual and automated code review to detect vulnerabilities such as injection, insecure dependencies, or outdated libraries.
• Infrastructure hardening
Ensure firewalls, WAF (Web Application Firewall), server isolation, SSH key-based access, and database security rules are implemented correctly.
• Compliance verification
Before launch, confirm compliance with GDPR, CCPA, PCI DSS, and other regional regulations. This protects you from legal penalties.
• Staff training programs
Educate your internal team on secure usage, admin panel best practices, password policies, and incident response procedures.
Post-launch monitoring
Security does not end at deployment. Continuous monitoring keeps the platform protected as new threats emerge.
• Continuous security monitoring
Track server logs, suspicious activities, unauthorized access attempts, and API anomalies in real time.
• Regular updates and patches
Apply security patches for libraries, frameworks, APIs, and OS environments to stay ahead of new vulnerabilities.
• Incident response planning
Create a documented and ready-to-execute plan for detecting, containing, and resolving any breach or anomaly.
• User data management
Implement strict data retention rules, anonymization where possible, and secure data disposal processes.
• Backup and recovery systems
Automated daily backups, off-site storage, and fast recovery ensure resilience during server failures or cyberattacks.
Security implementation timeline (recommended)
Week 1–2:
• Initial security audit
• Code and architecture review
• Infrastructure setup and hardening
Week 3:
• Compliance checks (GDPR, PCI DSS, CCPA)
• Secure authentication workflows
• API protection and encryption verification
Week 4:
• Penetration testing
• Load testing
• Fixing vulnerabilities
Post-launch (Ongoing):
• Monitoring and log analysis
• Patch updates
• Quarterly penetration testing
• Annual compliance review
Following this timeline ensures your white-label Hungerstation app launches with a strong, secure foundation and remains protected long-term.
Legal and Compliance Considerations
Legal compliance is just as important as technical security for a white-label Hungerstation app. Food delivery platforms operate across regions, collect sensitive user data, process payments, and track real-time locations — all of which fall under strict regulatory frameworks.
Regulatory requirements
• Data protection laws by region
Different regions enforce strict regulations, including GDPR (Europe), CCPA/CPRA (California), PDPA (Singapore), and India’s Digital Personal Data Protection Act. Your app must follow the laws of every region where users are located.
• Industry-specific regulations
If the app supports delivery of medicine, alcohol, or sensitive products, additional compliance may apply — such as HIPAA for medical-related deliveries or age-verification laws for restricted items.
• User consent management
The app must provide clear consent mechanisms for data collection, cookies, real-time location usage, personalized recommendations, and marketing notifications.
• Privacy policy requirements
A legally compliant privacy policy should outline:
– What data is collected
– How it is stored and processed
– Who it is shared with
– How users can request deletion or access
– Data retention practices
• Terms of service essentials
Terms of service must cover liability limits, user responsibilities, refund policies, delivery partner rules, dispute resolution, and platform restrictions.
Liability protection
• Insurance requirements
Cyber liability insurance and business continuity insurance protect against financial losses from breaches, downtime, or attacks.
• Legal disclaimers
A well-written disclaimer clarifies roles between the platform, restaurants, and delivery partners — reducing legal exposure.
• User agreements
These agreements ensure customers, restaurants, and delivery partners understand their obligations and data rights.
• Incident reporting protocols
Authorities in some regions require breach notifications within 24–72 hours. Having a protocol in place ensures compliance.
• Regulatory compliance monitoring
Regular review ensures the app stays compliant as laws evolve, especially in regions with dynamic digital governance.
Compliance checklist by region
- European Union (GDPR):
- Data processing agreements
- Consent logs
- Right-to-access and deletion workflow
- Data encryption
- Breach reporting system
- United States (CCPA/CPRA):
- Opt-out mechanisms
- Do-Not-Sell rules
- Data transparency statements
- Verified consumer requests system
- Middle East (UAE, KSA regulations):
- Local data hosting (if required)
- Clear security documentation
- Government reporting compliance
- Asia-Pacific (PDPA, DPDP Act):
- Data minimization
- Secure data transfers
- Retention and deletion policies
Meeting these requirements protects your business from legal penalties and builds long-term user trust.
Why Miracuves White-Label Hungerstation App Is Your Safest Choice
Security is not an optional feature for a food delivery app — it is the foundation of trust, compliance, and long-term business stability. Miracuves builds every white-label Hungerstation app with a security-first architecture designed to withstand modern threats and meet global compliance standards.
Miracuves security advantages
• Enterprise-grade security architecture
Every layer — frontend, backend, APIs, databases, and infrastructure — follows secure-by-design principles.
• Regular security audits and certifications
Systems are continuously evaluated through internal audits, external penetration tests, and compliance reviews.
• GDPR/CCPA compliant by default
Data protection, consent management, and user privacy controls are built into the core platform.
• 24/7 security monitoring
Real-time monitoring detects suspicious activity, unauthorized access attempts, or abnormal system behavior immediately.
• Encrypted data transmission
All data is secured using modern cryptography, including TLS 1.3, encrypted APIs, and secure database storage.
• Secure payment processing
Integrated PCI DSS–compliant payment flows ensure card data never touches your servers.
• Regular security updates
Patches, framework updates, vulnerability fixes, and dependency upgrades are applied consistently to keep the platform safe over time.
• Insurance coverage included
Miracuves provides coverage that protects against potential operational or cybersecurity incidents, adding an extra layer of business confidence.
Conclusion:
Don’t compromise on security. Miracuves white-label Hungerstation app solutions come with enterprise-grade protection built into every layer. With 600+ successful projects and zero major security breaches, you get a platform that is safe, compliant, and future-ready. Get a free security assessment today and see why businesses rely on Miracuves to power secure, scalable food delivery systems.
A white-label Hungerstation app can be fully secure — but only if built with the right standards, compliance, and ongoing protection. Most risks come from poor vendors, not the white-label model itself. Choose a provider that treats security as a core responsibility, not an add-on, and your platform will stay safe, trusted, and future-ready.
FAQs
1. How secure is a white-label app compared to custom development?
A well-built white-label app can be just as secure as custom development when it follows strict security standards and regular audits.
2. What happens if there’s a security breach?
A proper incident response plan should detect, contain, report, and resolve the issue within legally required timelines.
3. Who is responsible for security updates?
Your provider should handle continuous updates, patches, and maintenance — not just one-time development.
4. How is user data protected?
Through encryption, secure authentication, restricted access, and compliance-driven data policies.
5. What compliance certifications should I look for?
ISO 27001, SOC 2 Type II, GDPR, CCPA, and PCI DSS for payment security.
6. Can white-label apps meet enterprise security standards?
Yes — if built with secure architecture, audits, and certified processes.
7. How often should security audits be conducted?
Quarterly vulnerability assessments and annual full penetration tests are recommended.
8. What’s included in the Miracuves security package?
Encryption, audits, monitoring, secure APIs, compliance frameworks, and regular updates.
9. How to handle security in different countries?
Follow local data protection laws, retention rules, and hosting requirements.
10. What insurance is needed for app security?
Cyber liability insurance and business continuity insurance provide essential protection.
Related Articles:








