You’ve probably heard the horror stories — grocery apps leaking customer addresses, payment data exposed through weak APIs, or startups facing legal trouble after a single security breach. In the world of 10-minute grocery delivery, where users share real-time location, phone numbers, payment details, and daily purchase behavior, security is no longer optional.
A white-label Zepto app handles some of the most sensitive data any consumer platform can store. From live rider tracking and saved card details to order history and address patterns, even a small vulnerability can turn into a large-scale business disaster.
In 2025, user trust is fragile, regulators are aggressive, and attackers are smarter than ever. This is why founders, grocery chains, and logistics startups asking “Is a white-label Zepto app safe?” are asking the right question.
This guide delivers an honest, security-first assessment of white-label Zepto app safety. We’ll break down real risks, modern compliance requirements, and the practical steps required to launch a secure, scalable instant grocery platform — while clearly showing how Miracuves approaches security differently from low-cost, high-risk providers.
Understanding White-Label Zepto App Security Landscape
What White-Label Zepto App Security Actually Means
When people talk about white-label app security, they often assume it simply means “the code is reused.” In reality, white-label Zepto app security is about how safely that reusable architecture is built, deployed, and maintained.
A secure white-label Zepto app must protect:
- Customer personal data (names, phone numbers, addresses)
- Real-time location tracking of users and delivery partners
- Payment credentials and transaction history
- Vendor inventory and pricing data
- Internal operational dashboards and APIs
Security is not determined by whether an app is white-label or custom-built. It is determined by engineering discipline, infrastructure design, and compliance maturity.
Why Founders Worry About White-Label Zepto Apps
The concern is justified. Zepto-style apps operate under extreme conditions:
- High order volume in short time windows
- Continuous GPS tracking
- Real-time inventory updates
- Multiple third-party integrations (payments, maps, SMS, push)
Founders fear:
- Data leaks exposing customer addresses
- Payment fraud and chargebacks
- API abuse by competitors or attackers
- Regulatory fines under data protection laws
- Brand damage that kills user trust overnight
Current Threat Landscape for Zepto-Type Platforms
In 2025, instant grocery and hyperlocal delivery apps are prime targets for attackers because they combine financial data, physical locations, and operational APIs.
Key threats include:
- API scraping for pricing and inventory data
- Account takeover through weak authentication
- Location spoofing and order manipulation
- Payment token interception
- Admin panel compromise
- Vendor-side credential leaks
Security Standards in 2025
Modern white-label Zepto apps are expected to align with:
- Zero-trust infrastructure models
- Encryption-first data handling
- Privacy-by-design architecture
- Continuous monitoring and alerting
- Mandatory compliance documentation
Security is no longer a “feature.” It is a baseline requirement.
Real-World App Security Statistics
Recent industry data shows:
- Over 60% of grocery and delivery app breaches originate from insecure APIs
- Nearly 1 in 3 breaches involve misconfigured cloud storage
- Payment-related vulnerabilities account for the highest financial losses
- Most breaches go undetected for weeks without monitoring systems
These numbers explain why regulators and enterprises are demanding provable security, not promises.
Key Security Risks & How to Identify Them
High-Risk Area 1: Data Protection and Privacy
A white-label Zepto app processes highly sensitive personal data multiple times a day. If data protection is weak, the risk is immediate and severe.
User Personal Information
Customer names, phone numbers, addresses, and order history must be securely stored and access-controlled. Poor role-based access or unencrypted databases expose this data to internal misuse and external attacks.
Payment Data Security
Although payments usually pass through gateways, unsafe token handling, insecure callbacks, or weak server validation can still lead to financial breaches.
Location Tracking Concerns
Live delivery tracking exposes real-time movement patterns. Without strict access rules and encryption, attackers can misuse this data to profile users or riders.
GDPR and CCPA Compliance
Failure to manage consent, data retention, and deletion requests can lead to heavy fines and forced shutdowns in regulated markets.
High-Risk Area 2: Technical Vulnerabilities
Technical weaknesses are the most common cause of white-label app breaches.
Code Quality Issues
Poorly written code introduces logic flaws, insecure data handling, and exploitable endpoints that attackers can easily discover.
Server Security Gaps
Misconfigured cloud servers, open ports, and weak firewall rules expose backend systems directly to the internet.
API Vulnerabilities
APIs handle orders, payments, inventory, and tracking. Weak authentication or missing rate limits allow abuse, scraping, and manipulation.
Third-Party Integrations
Payment gateways, maps, SMS, and analytics tools introduce external risk if not properly sandboxed and monitored.
High-Risk Area 3: Business-Level Risks
Security failures do not stop at technical damage. They directly impact business survival.
Legal Liability
Data protection violations can trigger lawsuits, penalties, and regulatory investigations.
Reputation Damage
A single breach can permanently destroy trust in a grocery delivery brand.
Financial Losses
Chargebacks, fraud, downtime, and recovery costs can drain operating capital.
Regulatory Penalties
Non-compliance with data laws can result in fines running into millions, especially in Europe and North America.
White-Label Zepto App Risk Assessment Checklist
- Are all user and order databases encrypted at rest and in transit
- Is role-based access enforced for admin and operations teams
- Are APIs protected with authentication, authorization, and rate limiting
- Are third-party services isolated and monitored
- Is compliance documentation available and updated
- Is there an incident response and breach notification plan
Security Standards Your White-Label Zepto App Must Meet
Essential Security Certifications
A serious white-label Zepto app must meet recognized international security and compliance standards. These certifications are not marketing labels; they are proof that security controls exist, are documented, and are audited.
ISO 27001 Compliance
This standard ensures that the provider follows a structured Information Security Management System. It covers data access, risk assessment, incident handling, and continuous improvement.
SOC 2 Type II
SOC 2 Type II validates how security controls operate over time. It focuses on security, availability, confidentiality, and data integrity — critical for real-time grocery delivery platforms.
GDPR Compliance
Required for any app handling EU user data. It governs consent management, data storage, breach reporting, and user rights.
HIPAA (If Applicable)
If the app processes health-related data such as prescription groceries or wellness products, HIPAA compliance becomes relevant in certain regions.
PCI DSS for Payments
Any app handling card payments must follow PCI DSS standards to ensure secure processing and storage of payment data.
Technical Security Requirements
Certifications alone are not enough. The technical foundation must support them.
End-to-End Encryption
All data must be encrypted during transmission and while stored on servers. This prevents interception and unauthorized access.
Secure Authentication
Two-factor authentication and OAuth-based login systems reduce the risk of account takeovers and credential abuse.
Regular Security Audits
Internal and third-party audits help identify vulnerabilities before attackers exploit them.
Penetration Testing
Simulated attacks are essential to test real-world resilience against hacking attempts.
SSL Certificates
Secure communication between users, servers, and third-party services is mandatory.
Secure API Design
APIs must implement authentication, authorization, rate limiting, and logging to prevent abuse.
Security Standards Comparison Table
| Security Area | Basic Provider | Enterprise-Grade Provider (Miracuves) |
|---|---|---|
| Data Encryption | Partial or missing | Full encryption at rest and transit |
| Compliance | Self-declared | Audited and certified |
| API Security | Basic tokens | OAuth, rate limiting, monitoring |
| Audit Frequency | Rare or none | Regular scheduled audits |
| Incident Response | Reactive | Predefined response plans |
| Monitoring | Minimal | Continuous 24/7 monitoring |
Meeting these standards is what separates a risky white-label Zepto app from a platform that enterprises and regulators trust.
Red Flags – How to Spot Unsafe White-Label Providers
Warning Signs You Should Never Ignore
Many security failures start with choosing the wrong provider. Unsafe white-label Zepto apps often look attractive on the surface but hide serious risks underneath.
No Security Documentation
If a provider cannot clearly explain how data is stored, encrypted, and accessed, it usually means security was never properly implemented.
Unrealistically Cheap Pricing
Security infrastructure, audits, and compliance cost money. Extremely low pricing without justification often indicates shortcuts in critical areas.
No Compliance Certifications
Lack of ISO, SOC, GDPR, or PCI compliance is a strong signal that the app cannot meet enterprise or regulatory requirements.
Outdated Technology Stack
Old frameworks and unmaintained libraries increase vulnerability exposure and make patching difficult.
Poor Code Quality
Messy, undocumented code leads to bugs, security gaps, and expensive future fixes.
No Security Update Policy
If updates are not planned, tested, and deployed regularly, vulnerabilities remain open for exploitation.
Lack of Data Backup Systems
Without encrypted backups and recovery plans, data loss can permanently damage operations.
No Insurance Coverage
Professional liability and cyber insurance protect businesses during incidents. Providers without coverage shift all risk to you.
Evaluation Checklist Before Choosing a Provider
Questions to Ask
- How is user and order data encrypted
- What authentication and authorization mechanisms are used
- How often are security audits performed
- What happens in case of a data breach
- Who is responsible for applying security updates
Documents to Request
- Security architecture overview
- Compliance certificates and audit reports
- Data protection and privacy policies
- Incident response plan
Testing Procedures
- API security testing reports
- Penetration testing summaries
- Load and stress testing results
Due Diligence Steps
- Verify certifications independently
- Review past project security history
- Assess update and maintenance processes
- Confirm legal and insurance coverage
Identifying these red flags early can save months of legal, financial, and reputational damage.
Best Practices for Secure White-Label Zepto App Implementation
Pre-Launch Security Measures
Security must be validated before the app ever reaches real users. Most breaches happen because this phase is rushed or skipped.
Security Audit Process
A full audit should review application logic, APIs, server configuration, data storage, and access controls. This identifies weaknesses early.
Code Review Requirements
Independent code reviews reduce hidden vulnerabilities and ensure secure coding standards are followed consistently.
Infrastructure Hardening
Servers should be isolated, firewalls configured, unnecessary ports closed, and access restricted using least-privilege principles.
Compliance Verification
All required certifications and legal compliance checks must be completed before launch, not promised for later.
Staff Training Programs
Operations and support teams must understand security protocols, data handling rules, and incident escalation procedures.
Post-Launch Security Monitoring
Launching the app is not the end of security responsibility. Continuous protection is critical.
Continuous Security Monitoring
Real-time monitoring detects suspicious behavior, unauthorized access, and unusual traffic patterns.
Regular Updates and Patches
Security patches must be applied promptly to prevent known vulnerabilities from being exploited.
Incident Response Planning
A clear response plan defines how breaches are contained, investigated, and reported.
User Data Management
Data retention, deletion, and access requests must be handled according to privacy regulations.
Backup and Recovery Systems
Encrypted backups and tested recovery procedures ensure business continuity during failures or attacks.
White-Label Zepto App Security Implementation Timeline
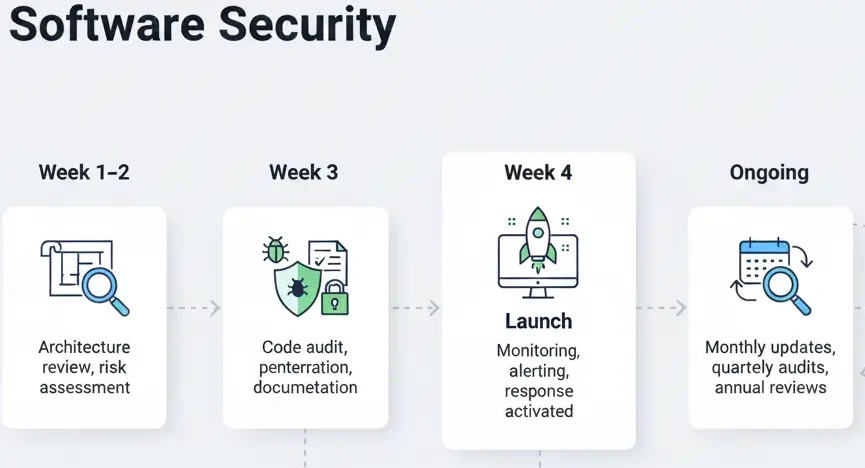
Following this structured approach dramatically reduces long-term security risk.
Read more : – Zepto Revenue Model: How Zepto Makes Money in 2025
Legal & Compliance Considerations
Regulatory Requirements for White-Label Zepto Apps
A white-label Zepto app operates in a heavily regulated environment because it handles personal data, payment information, and real-world logistics. Ignoring legal compliance is one of the fastest ways to shut down a growing platform.
Data Protection Laws by Region
Different regions impose different obligations on app owners:
- Europe (GDPR)
Requires explicit user consent, data minimization, breach notification within strict timelines, and the right to data deletion. - United States (CCPA / CPRA)
Focuses on transparency, user rights over personal data, and restrictions on data sharing. - India (DPDP Act)
Mandates purpose limitation, consent management, secure storage, and accountability for data processors. - Other Regions
Many countries now follow GDPR-inspired frameworks, making global compliance a necessity.
Industry-Specific Regulations
Instant grocery delivery apps may also face:
- Consumer protection laws
- Digital payment regulations
- Food and supply chain compliance rules
- Cross-border data transfer restrictions
Failing to align with these laws can result in fines, operational bans, and forced data deletion.
User Consent and Privacy Management
A compliant white-label Zepto app must:
- Clearly explain how user data is collected and used
- Allow users to control permissions
- Provide easy opt-out and data deletion options
- Maintain detailed consent logs for audits
Privacy Policy and Terms of Service Essentials
Legal documents must not be generic templates. They should:
- Reflect actual data practices
- Define roles and responsibilities clearly
- Explain security safeguards
- Outline breach notification processes
Liability Protection for App Owners
Security incidents are not just technical events; they are legal events.
Insurance Requirements
Cyber liability and professional indemnity insurance protect against financial loss during breaches.
Legal Disclaimers
Clear disclaimers limit exposure when systems are misused or external services fail.
User Agreements
Strong agreements define acceptable use, dispute resolution, and data responsibilities.
Incident Reporting Protocols
Predefined reporting timelines ensure compliance with regulators and users.
Compliance Monitoring
Regular reviews help maintain alignment with evolving laws.
Compliance Checklist by Region
- Data protection compliance verified
- Consent mechanisms implemented
- Legal documents reviewed and updated
- Breach reporting workflows defined
- Insurance coverage confirmed
Legal compliance is not a one-time task. It is an ongoing responsibility that must evolve with regulations.
Read more : – Zepto Revenue Model: How Zepto Makes Money in 2025
Why Miracuves White-Label Zepto App Is Your Safest Choice
Miracuves Security-First Philosophy
Most security failures in white-label grocery apps happen because security is treated as an add-on. At Miracuves, security is designed into the architecture from day one. Every white-label Zepto app is built with enterprise-grade safeguards that scale with your business.
Miracuves Security Advantages
Enterprise-Grade Security Architecture
Our apps are built on hardened infrastructure with strict access controls, isolated environments, and zero-trust principles.
Regular Security Audits and Certifications
Miracuves follows internationally recognized security standards and conducts regular internal and third-party audits to maintain compliance.
GDPR and CCPA Compliance by Default
Privacy and consent management are built into the core system, not bolted on later.
24/7 Security Monitoring
Continuous monitoring helps detect threats early and respond before damage occurs.
Encrypted Data Transmission
All sensitive data is encrypted in transit and at rest using modern cryptographic standards.
Secure Payment Processing
Payment flows follow PCI DSS requirements, ensuring safe handling of financial transactions.
Regular Security Updates
Vulnerabilities are patched promptly through controlled update cycles.
Insurance Coverage Included
Professional and cyber liability coverage reduces risk exposure for app owners.
Why Businesses Trust Miracuves
- 600+ successfully delivered platforms
- Zero major reported security breaches
- Proven experience in high-traffic, real-time apps
- Dedicated security and compliance teams
Final Thought
Don’t compromise on security. Miracuves white-label Zepto app solutions come with enterprise-grade security built in from day one. Our platforms are designed to meet modern compliance standards while protecting your users, data, and brand reputation.
Get a free security assessment and see why businesses trust Miracuves to build safe, compliant instant grocery delivery platforms.
Security is the foundation of trust for any instant grocery app. A white-label Zepto app can be just as safe — or safer — than a custom build, but only when security, compliance, and monitoring are treated as non-negotiable essentials. Choosing a provider that prioritizes audits, encryption, and legal compliance is not a cost decision; it is a business survival decision.
FAQs
1. Is a white-label Zepto app secure compared to custom development?
Yes, a white-label Zepto app can be equally secure or more secure than custom development when built with audited code, certified infrastructure, and continuous monitoring. Security depends on implementation quality, not development model.
2. What happens if there is a security breach?
A defined incident response process is activated, affected systems are isolated, investigations begin, and regulatory and user notifications are handled according to legal timelines.
3. Who is responsible for security updates?
The app provider is responsible for maintaining core security updates, while the app owner must ensure updates are deployed and operational policies are followed.
4. How is user data protected in a white-label Zepto app?
User data is protected through encryption, access controls, secure APIs, and compliance-driven data handling policies.
5. What compliance certifications should I look for?
ISO 27001, SOC 2 Type II, GDPR compliance, and PCI DSS for payment processing are essential for grocery delivery apps.
6. Can white-label Zepto apps meet enterprise security standards?
Yes, enterprise-grade white-label Zepto apps are designed to meet regulatory, operational, and security requirements at scale.
7. How often should security audits be conducted?
Internal audits should occur regularly, with external audits at least annually or after major system changes.
8. What is included in Miracuves’ security package?
Secure architecture, compliance readiness, encrypted data handling, continuous monitoring, regular updates, and incident response planning.
9. How is security managed across different countries?
Security controls are adapted to regional data protection laws while maintaining a consistent global security baseline.
10. What insurance is needed for app security?
Cyber liability and professional indemnity insurance protect against financial and legal risks related to sec
Related Articles:








