You’ve heard the horror stories about data breaches, leaked customer addresses, stolen card details, and grocery apps getting pulled down due to compliance failures. For founders planning to launch a white-label BigBasket app, one question dominates every discussion:
Is it actually safe?
In 2025, grocery delivery apps handle far more than product listings. They store personal identities, phone numbers, real-time locations, saved payment methods, order histories, and vendor data. One weak security decision can expose thousands of users and permanently damage brand trust.
White-label apps often get unfairly labeled as “unsafe” or “cheap shortcuts.” The truth is more nuanced. Safety depends entirely on how the app is engineered, hosted, audited, and maintained. A poorly built white-label BigBasket app can be dangerous. A security-first one can match or exceed custom-built platforms.
This guide delivers an honest, technical, and practical security assessment of white-label BigBasket app safety in 2025. We will break down real risks, current threat patterns, compliance standards, and exactly how to evaluate whether a provider is trustworthy.
You’ll also see how Miracuves approaches white-label app security differently, treating grocery platforms as enterprise-grade infrastructure rather than just reusable code.
Understanding White-Label BigBasket App Security Landscape
What “White-Label App Security” Actually Means
When people talk about white-label app security, they often misunderstand what is being reused. A white-label BigBasket app does not mean shared databases or shared user data across clients. It means a reusable core architecture that is deployed as a separate, isolated instance for each business.
Security in a white-label app depends on:
- How the core codebase is written and reviewed
- Whether each client gets isolated servers and databases
- How data encryption, access control, and updates are handled
- How quickly vulnerabilities are patched across deployments
A well-designed white-label app actually benefits from security compounding. Vulnerabilities discovered in one deployment are fixed globally, strengthening all instances.
Why Founders Worry About White-Label BigBasket Apps
Security concerns usually come from real risks founders have seen in the market:
- Reports of leaked customer phone numbers and addresses
- Fake order manipulation and wallet abuse
- Admin panel takeovers due to weak authentication
- Payment fraud through insecure APIs
- Regulatory notices due to GDPR or data protection failures
These risks are not caused by white-label models themselves, but by vendors cutting corners on security engineering.
Current Threat Landscape for Grocery Delivery Apps (2025)
In 2025, grocery delivery platforms face advanced, organized threats:
- Credential stuffing attacks on user accounts
- API abuse targeting pricing and coupon logic
- Bot-driven inventory scraping
- Payment token interception attempts
- Insider threats through poorly protected admin panels
According to recent industry security reports, retail and grocery apps account for over 18% of consumer app data breach incidents, with location data and phone numbers being the most commonly exposed assets.
Security Standards That Matter in 2025
A modern white-label BigBasket app must align with:
- Zero-trust access principles
- Encrypted data storage and transmission
- Strong API authentication and rate limiting
- Continuous vulnerability monitoring
- Privacy-by-design architecture
In 2025, regulators and users expect enterprise-grade security, even from early-stage platforms. Apps that fail to meet these expectations struggle with user trust, partnerships, and payment gateway approvals.
Key Security Risks & How to Identify Them
High-Risk Area 1: Data Protection & Privacy
Grocery delivery apps like a white-label BigBasket app process highly sensitive consumer data every day. This makes data protection the single biggest risk category.
User Personal Information
This includes names, phone numbers, home addresses, order history, and behavioral patterns. If databases are not properly encrypted or access-controlled, attackers can extract bulk user data with minimal effort.
Payment Data Security
Even if a third-party payment gateway is used, insecure app-side handling can expose:
- Payment tokens
- Order-value manipulation
- Wallet balance abuse
A secure app must never store raw card data and must strictly follow PCI DSS guidelines.
Location Tracking Concerns
Live delivery tracking exposes real-time user and driver locations. Without secure APIs and tokenized access, this data can be intercepted or misused, creating serious privacy risks.
GDPR and CCPA Compliance
Failure to manage user consent, data retention, and deletion requests can lead to regulatory penalties. In 2025, data protection authorities actively fine apps that cannot demonstrate compliance processes.
High-Risk Area 2: Technical Vulnerabilities
Code Quality Issues
Poorly written or outdated code introduces:
- SQL injection risks
- Insecure authentication logic
- Broken access control
Low-cost providers often reuse legacy scripts without security refactoring.
Server Security Gaps
Common problems include:
- Shared hosting environments
- Weak firewall rules
- No intrusion detection systems
- Unpatched operating systems
Each white-label BigBasket app deployment must run in an isolated, hardened infrastructure.
API Vulnerabilities
APIs power mobile apps, admin panels, vendor dashboards, and delivery tracking. Weak API security leads to:
- Order manipulation
- Price tampering
- Unauthorized data access
Secure APIs require authentication tokens, rate limiting, and role-based permissions.
Third-Party Integrations
SMS gateways, maps, analytics tools, and CRM integrations can become entry points if not vetted properly. Each external dependency increases the attack surface.
High-Risk Area 3: Business-Level Risks
Legal Liability
If user data is compromised, the business owner is legally responsible, not the software vendor. This includes fines, lawsuits, and regulatory actions.
Reputation Damage
For grocery apps, trust is everything. A single breach can permanently damage customer confidence and partner relationships.
Financial Losses
Security incidents result in:
- Refunds and chargebacks
- Platform downtime
- Emergency security remediation costs
Regulatory Penalties
Non-compliance with data protection laws can trigger heavy penalties, especially in regions like the EU, UK, and parts of Asia.
Risk Assessment Checklist
Before selecting a white-label BigBasket app provider, verify:
- Are databases encrypted at rest and in transit?
- Is payment handling PCI DSS compliant?
- Are admin panels protected with multi-factor authentication?
- Are APIs documented with security controls?
- Is there a formal incident response plan?
- Are compliance processes clearly defined?
If any of these answers are unclear or undocumented, the risk level is high.
Security Standards Your White-Label BigBasket App Must Meet
In 2025, grocery delivery apps are expected to meet the same security benchmarks as fintech and health platforms. If a white-label BigBasket app does not align with recognized global standards, it is not production-ready.
Essential Compliance Certifications
ISO 27001 (Information Security Management)
ISO 27001 ensures that the app provider follows a structured, documented, and continuously improved information security framework. This covers risk assessment, access control, incident handling, and internal audits.
For a white-label BigBasket app, ISO 27001 indicates that:
- Data handling processes are formally defined
- Security responsibilities are clearly assigned
- Risks are reviewed regularly, not reactively
SOC 2 Type II
SOC 2 Type II evaluates how systems operate over time, not just at a single point. It focuses on:
- Security
- Availability
- Confidentiality
This is critical for grocery apps that operate 24/7 and handle live orders, payments, and delivery tracking.
GDPR Compliance
If the app serves users in Europe or handles EU resident data, GDPR compliance is mandatory. This includes:
- Explicit user consent
- Right to access and delete data
- Data minimization and retention policies
Non-compliance can result in severe penalties and forced service shutdowns.
HIPAA (Conditional)
HIPAA applies only if the grocery app handles medical or prescription-related data. While not common for all BigBasket-style apps, it becomes relevant for medicine delivery extensions.
PCI DSS for Payments
Any app that processes payments must comply with PCI DSS standards. This ensures:
- Secure payment data handling
- Tokenization instead of card storage
- Controlled access to payment systems
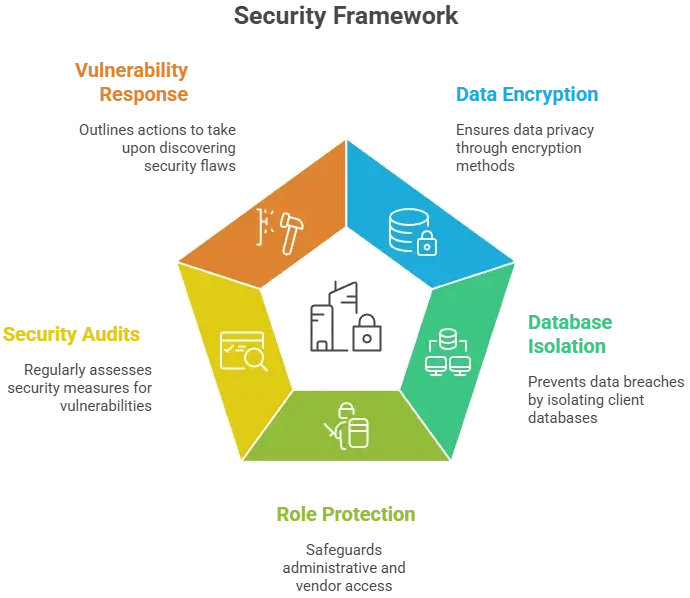
Technical Security Requirements
End-to-End Encryption
All data must be encrypted:
- In transit using TLS 1.2 or higher
- At rest using strong encryption algorithms
This protects user data even if infrastructure is compromised.
Secure Authentication and Access Control
A secure white-label BigBasket app must support:
- Two-factor authentication for admins
- OAuth or token-based user authentication
- Role-based access control for vendors and staff
Regular Security Audits
Security cannot be a one-time task. Apps must undergo:
- Periodic vulnerability assessments
- Code reviews
- Infrastructure audits
These audits should be documented and shareable with clients.
Penetration Testing
Penetration testing simulates real-world attacks to uncover hidden vulnerabilities. In 2025, serious platforms conduct this at least annually or after major updates.
SSL Certificates and Secure Hosting
SSL certificates are the minimum requirement. Hosting environments must also include:
- Firewalls and intrusion detection
- Secure cloud configurations
- Automated patch management
Secure API Design
APIs should implement:
- Authentication tokens
- Rate limiting
- Input validation
- Logging and monitoring
APIs are the most targeted attack surface in grocery delivery apps.
Security Standards Comparison Table
| Security Area | Basic Providers | Enterprise-Grade Standard |
|---|---|---|
| Data Encryption | Partial or optional | Mandatory at rest and in transit |
| Payment Security | Gateway only | PCI DSS compliant flow |
| Admin Access | Password-based | 2FA + role-based access |
| API Protection | Minimal | Tokenized, rate-limited APIs |
| Compliance | None or unclear | ISO 27001, SOC 2, GDPR |
| Audits | One-time | Continuous and documented |
If a white-label BigBasket app provider cannot clearly explain how they meet these standards, the platform is not suitable for long-term operation.
Read more : – Top BigBasket App Features Explained
Red Flags: How to Spot Unsafe White-Label App Providers
Not all white-label app providers build with security as a priority. In the grocery delivery space, unsafe providers often look attractive on the surface but hide serious long-term risks. Knowing the warning signs can save you from costly mistakes.
Critical Warning Signs to Watch For
No Security Documentation
If a provider cannot clearly explain how data is stored, encrypted, and accessed, that is a major red flag. Professional vendors maintain written security architecture and compliance documentation.
Unrealistically Cheap Pricing
Extremely low prices usually mean corners are being cut. Security audits, compliance certifications, and hardened infrastructure are expensive. If pricing seems too good to be true, security is likely missing.
No Compliance Certifications
Providers who dismiss ISO, SOC 2, or GDPR as “optional” are not enterprise-ready. In 2025, compliance is a baseline requirement, not an upgrade.
Outdated Technology Stack
Old frameworks, unsupported libraries, and legacy scripts increase vulnerability exposure. Modern grocery apps require actively maintained and patched technology.
Poor Code Quality
Signs include:
- No version control transparency
- No documented code review process
- Lack of modular architecture
Poor code quality makes security fixes slow and risky.
No Security Update Policy
Security threats evolve constantly. If the provider does not offer regular updates and patching, vulnerabilities will remain open indefinitely.
Weak or Missing Backup Systems
Without encrypted backups and disaster recovery plans, data loss from attacks or outages can be permanent.
No Insurance Coverage
Serious providers carry cyber liability or professional indemnity insurance. Absence of insurance shifts all risk to the client.
Evaluation Checklist Before Choosing a Provider
Documents to Request
- Security architecture overview
- Compliance certificates or audit summaries
- Data protection and privacy policies
- Incident response plan
Testing Procedures
- Can you conduct independent penetration testing?
- Is a staging environment available for security validation?
- Are API endpoints documented with security controls?
Due Diligence Steps
- Review past client history
- Check for publicly reported incidents
- Validate hosting and infrastructure setup
If a provider avoids or deflects these questions, it is a clear signal that security is not their priority.
Best Practices for Secure White-Label BigBasket App Implementation
Launching a secure white-label BigBasket app is not just about choosing the right provider. Security must be embedded throughout the implementation lifecycle, from pre-launch preparation to ongoing operations.
Pre-Launch Security Best Practices
Comprehensive Security Audit
Before going live, the entire app ecosystem should be audited. This includes mobile apps, web panels, APIs, databases, and server infrastructure. Audits help identify hidden vulnerabilities that are not visible during normal testing.
Strict Code Review Process
Every release should pass structured code reviews focusing on authentication logic, data handling, and access control. This reduces the risk of introducing exploitable flaws into production.
Infrastructure Hardening
Servers must be configured with:
- Isolated environments per client
- Firewalls and intrusion detection systems
- Secure cloud permissions
- Automated security patching
Infrastructure misconfigurations are one of the leading causes of breaches in delivery apps.
Compliance Verification
Before launch, verify:
- GDPR consent flows
- Data retention and deletion mechanisms
- Privacy policy alignment with actual app behavior
Compliance should be tested in practice, not just documented.
Staff and Admin Training
Human error is a major risk factor. Admins and support teams should be trained on:
- Secure password practices
- Phishing awareness
- Proper data access protocols
Post-Launch Security Monitoring
Continuous Security Monitoring
A production app must be monitored for:
- Unusual login patterns
- API abuse
- Suspicious order activity
- Infrastructure anomalies
Early detection prevents minor issues from becoming major incidents.
Regular Updates and Patch Management
Security updates should be deployed on a defined schedule, with emergency patches available for critical vulnerabilities. Delayed updates are a common cause of exploits.
Incident Response Planning
Every app should have a documented incident response plan outlining:
- Detection and escalation steps
- User and authority notification timelines
- Containment and recovery actions
This ensures fast, controlled handling of security events.
User Data Management
Clear processes must exist for:
- Data access requests
- Data deletion requests
- Account deactivation
These are legal requirements in many regions, not optional features.
Backup and Recovery Systems
Encrypted backups should be:
- Automated
- Stored securely
- Tested regularly for restoration
Backups are essential for ransomware protection and disaster recovery.
Security Implementation Timeline
| Phase | Security Focus |
|---|---|
| Planning | Risk assessment and compliance mapping |
| Development | Secure coding and access control |
| Pre-Launch | Audits, penetration testing, compliance checks |
| Launch | Monitoring and incident readiness |
| Post-Launch | Continuous updates and security reviews |
When security is treated as a continuous process rather than a one-time task, white-label BigBasket apps can operate safely at scale.
Legal & Compliance Considerations
Security is not only a technical responsibility but also a legal obligation. For a white-label BigBasket app, compliance failures can result in fines, forced shutdowns, or long-term legal exposure.
Regulatory Requirements by Region
India
- Compliance with the Digital Personal Data Protection Act (DPDP Act)
- Clear user consent for data collection and processing
- Defined data retention and deletion policies
India has significantly tightened enforcement around consumer data protection, especially for delivery and retail apps.
European Union
- Mandatory GDPR compliance
- Lawful basis for data processing
- Right to data access, correction, and erasure
Any grocery app serving EU users or handling EU data must demonstrate GDPR compliance, regardless of where the business is based.
United States
- CCPA and CPRA for California residents
- State-level privacy regulations expanding rapidly
- Transparent data usage disclosures
Apps operating in the US must handle regional variations carefully to avoid non-compliance.
Other Regions
- UK GDPR
- Singapore PDPA
- UAE and Middle East data protection frameworks
A scalable white-label BigBasket app must support region-specific compliance configurations.
User Consent and Privacy Management
A compliant app must include:
- Clear consent prompts during onboarding
- Granular permission controls
- Transparent privacy policies aligned with actual data usage
Hidden or vague consent mechanisms are no longer acceptable in 2025.
Terms of Service and Policy Essentials
Legal documents should clearly define:
- User responsibilities
- Platform limitations
- Data usage and retention
- Dispute resolution mechanisms
These documents protect both users and business owners.
Liability Protection Strategies
Insurance Requirements
Businesses should carry:
- Cyber liability insurance
- Professional indemnity insurance
These policies help cover breach response costs, legal fees, and regulatory penalties.
Legal Disclaimers and Agreements
Proper disclaimers reduce exposure during:
- Service outages
- Data incidents
- Third-party integration failures
Incident Reporting Protocols
Regulations often require breach notifications within strict timelines. Apps must have internal processes to:
- Identify incidents
- Notify authorities
- Inform affected users
Compliance Monitoring
Compliance is ongoing. Regular reviews should verify:
- Policy alignment with laws
- Security controls effectiveness
- Vendor and integration compliance
Without continuous monitoring, even compliant apps can drift into violation over time.
Read more : – How to Hire the Best BigBasket Clone Developer
Why Miracuves White-Label BigBasket App Is Your Safest Choice
Security is not treated as an add-on at Miracuves. It is built into the architecture, processes, and delivery model of every white-label BigBasket app we deploy.
Enterprise-Grade Security Architecture
Miracuves apps are designed using security-first principles:
- Isolated infrastructure per client
- Encrypted databases and storage
- Secure cloud configurations aligned with industry best practices
This ensures that one client’s data is never exposed to another.
Verified Compliance Readiness
Miracuves aligns its platforms with:
- ISO 27001 security frameworks
- SOC 2 control principles
- GDPR and CCPA data protection requirements
Compliance is designed into the app workflow, not retrofitted later.
Continuous Security Monitoring
Every deployed app benefits from:
- 24/7 infrastructure monitoring
- Automated threat detection
- Real-time alerts for suspicious activity
This proactive approach significantly reduces response time during incidents.
Strong Data and Payment Protection
User data protection includes:
- End-to-end encrypted data transmission
- Secure role-based access control
- Strict separation of admin, vendor, and user privileges
Payment flows follow PCI DSS-compliant patterns using secure gateways and tokenization.
Regular Security Updates and Audits
Miracuves conducts:
- Ongoing vulnerability assessments
- Scheduled security updates
- Periodic penetration testing
Security improvements are rolled out across all app deployments without disrupting operations.
Risk Coverage and Accountability
Miracuves supports clients with:
- Clear incident response processes
- Transparent security documentation
- Professional accountability through structured security practices
This reduces operational and legal uncertainty for founders.
Conclusion
Do not compromise on security when launching a grocery delivery platform. Miracuves white-label BigBasket app solutions are built with enterprise-grade security from day one. With over 600 successfully delivered projects and no major reported security breaches, Miracuves helps businesses launch compliant, resilient, and trusted platforms. Request a free security assessment and see how your platform can meet 2025’s highest safety standards.
White-label BigBasket apps are not inherently unsafe. The real risk lies in who builds the app, how security is engineered, and how seriously compliance is treated. In 2025, grocery delivery platforms operate in a high-risk environment where user trust, regulatory scrutiny, and cyber threats intersect every day.
FAQs
1. How secure is a white-label BigBasket app compared to custom development?
A security-first white-label BigBasket app can be as secure or more secure than custom development because it benefits from repeated audits, standardized controls, and continuous patching.
2. What happens if there is a security breach?
A proper incident response process includes immediate containment, investigation, user notification, regulatory reporting, and system hardening to prevent recurrence.
3. Who is responsible for security updates?
The app provider is responsible for core security updates, while the business owner manages operational security such as admin access and user policies.
4. How is user data protected in a white-label BigBasket app?
User data is protected through encryption at rest and in transit, role-based access control, secure APIs, and strict data retention policies.
5. What compliance certifications should I look for?
At minimum, ISO 27001, GDPR compliance, and PCI DSS-aligned payment handling. SOC 2 Type II is strongly recommended for scale.
6. Can white-label BigBasket apps meet enterprise security standards?
Yes, when built with isolated infrastructure, audited codebases, and continuous monitoring, they meet enterprise-level requirements.
7. How often should security audits be conducted?
At least annually, with additional audits after major feature releases or infrastructure changes.
8. What is included in Miracuves’ security package?
Enterprise-grade architecture, encrypted data handling, compliance-ready workflows, continuous monitoring, and regular security updates.
9. How is security handled across different countries?
The app supports region-specific compliance configurations to align with local data protection laws and regulations.
10. What insurance is needed for app security?
Cyber liability and professional indemnity insurance are recommended to cover breach response, legal costs, and regulatory penalties.
Related Articles:
- How Much Does It Cost to Develop a BigBasket App
- Best Gorillas Clone Scripts 2025 – Build a 10-Minute Delivery Empire Fast
- Instacart Revenue Model: How Instacart Makes Money in 2025
- White-Label Goldbelly App Security: Risks, Compliance & Safety in 2025
- White-Label JustEat App Security: Risks, Compliance & Protection in 2025








