You’ve probably heard the horror stories—property management platforms leaking tenant data, payment information getting compromised, or landlords facing legal trouble due to weak app security. When your business handles rent payments, bank details, leases, maintenance requests, and personal tenant information, security is not optional—it’s existential.
In 2025, launching a white-label Buildium app can accelerate your property management business, but only if the app is built with enterprise-grade security from day one. Regulations are stricter, cyberattacks are more targeted, and user trust is harder to earn—and easier to lose—than ever before.
This guide provides an honest, risk-focused assessment of white-label Buildium app safety. We’ll break down real threats, required compliance standards, and the exact security measures your app must meet—while showing how Miracuves approaches white-label app security differently, with a security-first architecture designed for long-term protection.
Understanding White-Label Buildium App Security Landscape
What “White-Label Buildium App Security” Actually Means
A white-label Buildium app is a pre-built property management platform customized with your branding and business workflows. From a security perspective, this means you inherit both the strengths and weaknesses of the underlying architecture. The safety of your app depends on how securely the core system is designed, deployed, and maintained—not just how it looks on the surface.
True white-label app security covers:
- How tenant and landlord data is stored
- How financial transactions are processed
- How access is controlled for property managers, owners, and residents
- How the app responds to security incidents and regulatory audits
Security is not a feature—it is an ongoing operational responsibility.
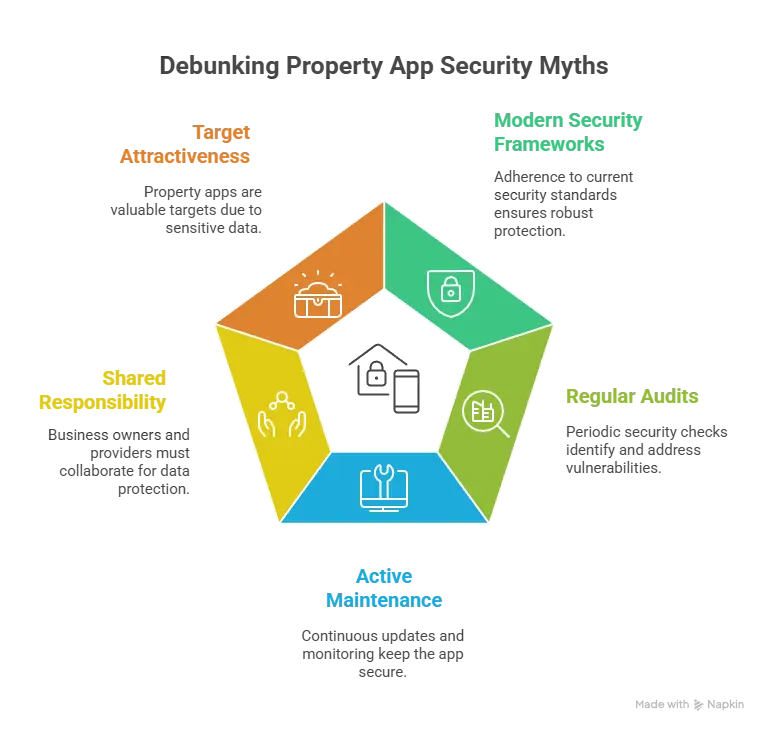
Why Businesses Worry About White-Label Buildium Apps
Security concerns around property management apps are justified due to:
- High concentration of sensitive tenant data
- Continuous payment processing and escrow handling
- Role-based access complexity (admins, landlords, tenants, vendors)
- Regulatory exposure across multiple jurisdictions
One breach can impact thousands of tenants simultaneously.
Current Threat Landscape for Property Management Apps (2025)
Property management platforms face a growing range of threats:
- Credential stuffing attacks on tenant portals
- API exploitation targeting rent payment systems
- Ransomware attacks on centralized databases
- Insider threats via misconfigured admin access
- Third-party service vulnerabilities (payment gateways, document storage)
Cloud-based apps without strong isolation and monitoring are particularly vulnerable.
Security Standards Defining Safety in 2025
Modern white-label Buildium app security must align with:
- Zero-trust access models
- Cloud-native security controls
- Encryption-by-default architectures
- Continuous compliance monitoring
- Automated vulnerability scanning
Security is now expected to be proactive, not reactive.
Real-World Security Statistics
- Over 60% of data breaches in SaaS platforms involve misconfigured access controls
- Property and real estate platforms saw a 38% increase in cyberattacks year-over-year
- Payment-related breaches result in an average $4.4 million loss per incident
- Regulatory fines now exceed breach recovery costs in many regions
These numbers highlight why app security decisions directly affect business survival.
Read more : – Buildium Revenue Model: How Buildium Makes Money in 2025
Key Security Risks & How to Identify Them
High-Risk Area 1: Data Protection & Privacy
A white-label Buildium app processes highly sensitive information daily. Any weakness in data protection can expose both tenants and property owners to serious harm.
User Personal Information
This includes names, addresses, identity documents, lease agreements, and communication history. Weak encryption or improper access controls can lead to identity theft and legal liability.
Payment Data Security
Rent payments, bank account details, card information, and escrow transactions must comply with strict financial security standards. Insecure payment handling is one of the most common breach points in property management apps.
Location & Property Data
Unit addresses, occupancy details, maintenance schedules, and access records can be exploited for fraud or physical security risks if exposed.
GDPR / CCPA Compliance Risks
Failure to properly manage consent, data retention, or user data deletion can result in heavy regulatory penalties and loss of trust.
High-Risk Area 2: Technical Vulnerabilities
Code Quality Issues
Poorly written or reused code increases exposure to injection attacks, authentication bypasses, and data leaks.
Server & Cloud Security Gaps
Improper cloud configuration, weak firewall rules, or unsecured storage buckets are a leading cause of large-scale breaches.
API Vulnerabilities
APIs power tenant portals, payment systems, and third-party integrations. Weak authentication or rate limiting can allow attackers to extract or manipulate data.
Third-Party Integrations
Payment gateways, document signing tools, and messaging services introduce external risk if not properly vetted and monitored.
High-Risk Area 3: Business & Operational Risks
Legal Liability
As the platform owner, you are responsible for data protection—even if the security failure originates from your provider.
Reputation Damage
Trust is critical in property management. A single breach can permanently damage brand credibility and user confidence.
Financial Losses
Costs include breach recovery, compensation, downtime, legal fees, and regulatory fines.
Regulatory Penalties
Non-compliance with data protection laws can trigger audits, forced shutdowns, or multi-million-dollar fines.
White-Label Buildium App Risk Assessment Checklist
- Is all user and payment data encrypted at rest and in transit?
- Are role-based access controls strictly enforced?
- Is payment processing fully PCI DSS compliant?
- Are APIs protected with authentication, rate limiting, and monitoring?
- Are third-party integrations security-audited?
- Is there a documented incident response plan?
- Are regular security audits and penetration tests conducted?
- Is compliance with GDPR and regional data laws clearly documented?
If any of these questions cannot be answered clearly, the app carries elevated risk.
Read more : – Business Model of Buildium : Complete Strategy Breakdown 2025
Security Standards Your White-Label Buildium App Must Meet
Essential Security Certifications
A secure white-label Buildium app must align with globally recognized security and compliance standards. These certifications are not marketing badges—they are proof of disciplined security governance.
ISO 27001 Compliance
Ensures a structured Information Security Management System (ISMS) covering risk assessment, access control, incident handling, and continuous improvement.
SOC 2 Type II
Validates that the app consistently protects customer data over time across security, availability, and confidentiality controls.
GDPR Compliance
Mandatory for handling EU resident data. Covers consent management, data minimization, right-to-erasure, and breach notification procedures.
HIPAA (If Applicable)
Required only if the app handles health-related tenant data, such as assisted living or senior housing records.
PCI DSS for Payments
Essential for rent payments, deposits, and escrow transactions involving card or bank data.
Technical Security Requirements
End-to-End Encryption
All data must be encrypted during transmission and while stored, preventing unauthorized access even if systems are compromised.
Secure Authentication
Multi-factor authentication, OAuth-based login, and role-based access ensure only authorized users access sensitive areas.
Regular Security Audits
Ongoing vulnerability assessments and third-party audits help detect issues before attackers do.
Penetration Testing
Simulated attacks identify real-world weaknesses across APIs, mobile apps, and admin panels.
SSL Certificates
Mandatory for securing all user interactions and preventing data interception.
Secure API Design
Includes token-based authentication, request validation, rate limiting, and logging.
Security Standards Comparison Table
| Security Area | Minimum Requirement | Enterprise-Grade Standard |
|---|---|---|
| Data Encryption | In transit only | In transit + at rest |
| Authentication | Password-based | MFA + OAuth |
| Payment Security | Basic gateway | Full PCI DSS |
| Compliance | Self-declared | ISO, SOC 2 verified |
| Monitoring | Manual checks | 24/7 automated |
| Audits | One-time | Continuous |
Meeting the enterprise-grade column is no longer optional in 2025—it is the baseline expectation.
Red Flags – How to Spot Unsafe White-Label Providers
Warning Signs You Should Never Ignore
Choosing the wrong white-label Buildium app provider can expose your entire business to unnecessary risk. The following red flags consistently appear in platforms that later suffer security incidents.
No Security Documentation
If a provider cannot clearly explain how data is stored, encrypted, and protected, security is not a priority.
Unrealistically Cheap Pricing
Enterprise-grade security has real costs. Extremely low pricing without a clear explanation often indicates shortcuts in infrastructure and compliance.
No Compliance Certifications
Lack of ISO 27001, SOC 2, or GDPR documentation signals weak governance and high regulatory risk.
Outdated Technology Stack
Legacy frameworks and unsupported libraries increase vulnerability exposure and reduce patching capability.
Poor Code Quality
Hardcoded credentials, reused code, and lack of documentation are common in insecure platforms.
No Security Update Policy
Security threats evolve constantly. Providers without a defined patch and update process leave apps exposed.
Weak Backup & Recovery Systems
Without encrypted backups and disaster recovery planning, data loss can be permanent.
No Cyber Insurance Coverage
A provider without insurance shifts all financial and legal risk onto you.
Evaluation Checklist Before Choosing a Provider
Questions to Ask
- How is tenant and payment data encrypted?
- What security audits are performed and how often?
- How do you handle security incidents and breach reporting?
- Who is responsible for compliance updates?
Documents to Request
- Security architecture overview
- Compliance certificates
- Penetration test summaries
- Data processing agreements
Testing Procedures
- Vulnerability scans on staging environments
- API security testing
- Role-based access testing
- Payment workflow validation
Due Diligence Steps
- Review past security track record
- Verify compliance claims independently
- Assess long-term update and support commitments
If a provider hesitates at any step, consider it a serious risk indicator.
Best Practices for Secure White-Label Buildium App Implementation
Pre-Launch Security Practices
Launching a white-label Buildium app without rigorous security preparation exposes the platform to immediate risk. Security must be validated before the first user signs up.
Security Audit Process
Conduct a full security audit covering application logic, APIs, infrastructure, and third-party services. Independent audits provide unbiased risk visibility.
Code Review Requirements
Every module should undergo manual and automated code review to identify vulnerabilities, insecure dependencies, and logic flaws.
Infrastructure Hardening
Servers must be configured with firewalls, intrusion detection systems, isolated environments, and secure cloud permissions.
Compliance Verification
Confirm GDPR, PCI DSS, and regional data protection requirements are fully implemented and documented.
Staff Access & Training
Limit administrative access strictly to need-based roles and train internal teams on secure data handling practices.
Post-Launch Security Monitoring
Continuous Security Monitoring
Real-time monitoring detects suspicious activity, unauthorized access attempts, and abnormal data usage patterns.
Regular Updates & Patches
Security updates must be applied consistently to address new vulnerabilities and dependency risks.
Incident Response Planning
A documented response plan ensures fast containment, user notification, and regulatory reporting if a breach occurs.
User Data Management
Data retention, deletion, and anonymization policies must be enforced automatically.
Backup & Recovery Systems
Encrypted backups and tested disaster recovery processes protect against data loss and ransomware attacks.
Security Implementation Timeline
| Phase | Key Activities |
|---|---|
| Week 1–2 | Security audit & risk assessment |
| Week 3 | Code review & penetration testing |
| Week 4 | Compliance verification |
| Launch | Monitoring & access control enforcement |
| Ongoing | Updates, audits, incident drills |
Security is not a one-time setup—it is a continuous operational commitment.
Read more : – Buildium Features List for Smarter Property Management
Legal & Compliance Considerations
Regulatory Requirements for a White-Label Buildium App
A white-label Buildium app operates at the intersection of real estate, finance, and personal data. This makes legal compliance non-negotiable in 2025.
Data Protection Laws by Region
Different regions impose different obligations on how tenant and landlord data is collected, stored, and processed.
- GDPR (EU): Lawful consent, right to access, right to deletion, breach notification within 72 hours
- CCPA/CPRA (USA): Data disclosure rights, opt-out mechanisms, data usage transparency
- DPDP Act (India): Consent-based processing, data minimization, breach accountability
Failure to comply can lead to operational bans, not just fines.
Industry-Specific Regulations
Property management apps handling escrow, rent collection, or trust accounts must align with financial and real estate regulations applicable in their operating region.
User Consent Management
Explicit consent must be collected for:
- Data storage and processing
- Communication and notifications
- Location and device access
Consent logs should be auditable and tamper-proof.
Privacy Policy Requirements
Your app must clearly disclose:
- What data is collected
- Why it is collected
- How long it is retained
- Who it is shared with
- How users can request deletion
Generic or copied policies are a compliance risk.
Terms of Service Essentials
Clearly define platform responsibility, user obligations, payment handling, dispute resolution, and service limitations.
Liability Protection Measures
Cyber Insurance Requirements
Cyber liability insurance helps cover breach response costs, legal claims, regulatory fines, and business interruption losses.
Legal Disclaimers
Disclaimers must be tailored to property management operations, not generic app usage.
User Agreements
Contracts should define data ownership, liability limits, and acceptable use policies.
Incident Reporting Protocols
Clear internal procedures ensure timely reporting to regulators and users when required by law.
Ongoing Compliance Monitoring
Regulations evolve. Continuous monitoring ensures the app remains compliant as laws change.
Compliance Checklist by Region
| Region | Key Laws | Mandatory Actions |
|---|---|---|
| EU | GDPR | Consent, encryption, breach reporting |
| USA | CCPA / CPRA | Data access rights, opt-out |
| India | DPDP Act | Consent tracking, data minimization |
| Global | PCI DSS | Secure payment processing |
Legal compliance is not just a safety net—it is a trust signal for landlords and tenants alike.

Why Miracuves White-Label Buildium App Is Your Safest Choice
Miracuves Security-First Approach
Miracuves does not treat security as an add-on. Every white-label Buildium app is engineered with enterprise-grade protection built into the core architecture—because property management platforms cannot afford shortcuts.
Enterprise-Grade Security Architecture
Our apps are designed using layered security models that isolate data, restrict access, and reduce attack surfaces across all modules.
Verified Compliance Readiness
Miracuves-built apps are structured to meet ISO 27001, SOC 2 Type II, GDPR, and PCI DSS requirements, making compliance achievable—not theoretical.
Privacy by Default
Data protection controls, consent management, and user rights handling are embedded from day one, ensuring GDPR and CCPA alignment.
24/7 Security Monitoring
Continuous monitoring helps detect anomalies, unauthorized access attempts, and suspicious activity before they escalate.
Encrypted Data Transmission & Storage
All sensitive data is encrypted in transit and at rest, protecting tenant, landlord, and payment information.
Secure Payment Processing
Rent collection and escrow flows follow PCI DSS standards with secure gateway integration.
Regular Security Updates
Security patches and dependency updates are applied continuously to address emerging threats.
Risk & Insurance Coverage
Miracuves follows structured risk management practices and supports insurance-ready deployments for added protection.
Final Thought
Don’t compromise on security. Miracuves white-label Buildium app solutions come with enterprise-grade security built in. With 600+ successful projects and zero major security breaches, we help businesses launch compliant, trustworthy property management platforms.
Get a free security assessment and see why businesses rely on Miracuves for safe, scalable white-label apps.
A white-label Buildium app can be safe, scalable, and compliant—but only when security is treated as a foundation, not an afterthought. In 2025, data protection, regulatory compliance, and user trust define success in property management platforms. Choosing a security-first provider like Miracuves ensures your app is built to protect users, withstand threats, and grow with confidence.
FAQs
1. How secure is a white-label Buildium app compared to custom development?
A white-label Buildium app can match or exceed custom development security when it follows ISO standards, regular audits, and continuous monitoring. Security depends on architecture and governance, not build method.
2. What happens if there is a security breach?
A secure app follows an incident response plan that includes containment, investigation, user notification, and regulatory reporting within required timelines.
3. Who is responsible for security updates?
The provider manages core security updates, while the business owner ensures operational practices and compliance obligations are followed.
4. How is user data protected in a white-label Buildium app?
Data is protected using encryption, role-based access controls, secure authentication, and continuous monitoring.
5. What compliance certifications should I look for?
ISO 27001, SOC 2 Type II, GDPR compliance, and PCI DSS are essential for property management apps.
6. Can a white-label Buildium app meet enterprise security standards?
Yes, when built with enterprise-grade infrastructure, audited security controls, and documented compliance processes.
7. How often should security audits be conducted?
Security audits should be conducted at least annually, with continuous vulnerability monitoring throughout the year.
8. What is included in Miracuves’ security package?
Encrypted data handling, compliance-ready architecture, regular audits, secure payment processing, and continuous monitoring.
9. How is security handled across different countries?
Data protection controls are adapted to regional laws such as GDPR, CCPA, and DPDP Act, with localized compliance management.
10. What insurance is needed for app security?
Cyber liability insurance is recommended to cover breach response costs, legal claims, and regulatory penalties.
Related Articles:








