You’ve heard the horror stories about super app data breaches, leaked customer information, hijacked driver accounts, and payment fraud. In an ecosystem as complex as a Gojek-style super app—with rides, food delivery, logistics, payments, and on-demand services—security issues multiply fast.
In 2025, the stakes are even higher. With new data protection laws, aggressive cyberattacks, AI-driven fraud, and millions of daily transactions, a single vulnerability in a white-label Gojek app can cause financial, legal, and reputational damage overnight.
This guide gives you an honest, research-backed breakdown of white-label Gojek app security: what’s actually risky, what’s misunderstood, and what you must demand from your technology provider. You’ll learn exactly how these apps can be secured, what standards they must meet, and why choosing the right partner makes all the difference.
Miracuves brings deep expertise in secure super app development, and this guide will show you what truly matters when launching a safe, compliant, multi-service ecosystem.
Understanding White-label Gojek App Security Landscape
What white-label security actually means
A white-label Gojek app is a pre-built multi-service platform that you customize and launch under your own brand. But the term “white-label” often confuses business owners into thinking security is weaker or generic. In reality, security depends entirely on how the provider designs, manages, and maintains the underlying architecture.
A secure white-label Gojek app should follow the same engineering standards as any enterprise super app: encrypted communication, secure APIs, strong authentication, audit logs, and continuous monitoring.
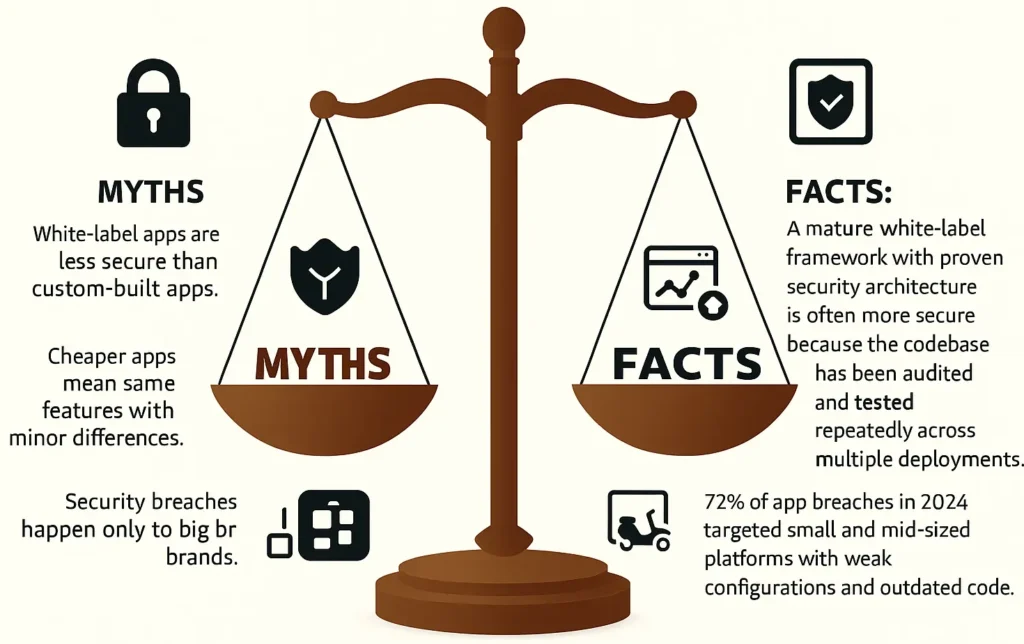
Why people worry about white-label apps
- Lack of visibility into the provider’s code quality
- Unknown server practices
- Fear of reused code creating vulnerabilities
- Questions about data ownership and privacy
- Complexity of super app ecosystems
- Multiple user roles increasing attack vectors
- Payment and wallet systems introducing financial risk
These concerns are valid—but solvable when backed by proper standards.
Current threat landscape for Gojek-type platforms
A super app like Gojek handles dozens of high-risk operations simultaneously: ride tracking, delivery routes, payment processing, chat systems, wallet management, identity verification, and much more. Each module becomes a potential entry point for attackers.
The most common threats in 2025 include:
- API-based attacks on ride-booking and delivery endpoints
- Token hijacking and session spoofing
- Wallet exploitation and payment fraud
- Fake driver or vendor account creation
- Reverse engineering of the app APK
- Phishing campaigns targeting customers and drivers
- Server misconfigurations exposing sensitive data
- AI-powered credential stuffing attacks
Security standards in 2025
A modern white-label Gojek app must follow globally recognized standards:
- ISO 27001 controls for information security
- SOC 2 Type II for data protection
- PCI DSS for payment modules
- GDPR/CCPA for data privacy
- OWASP Mobile Top 10 for vulnerability prevention
- Regular VAPT (Vulnerability Assessment and Penetration Testing)
Real-world security statistics for 2024–2025
- 48% of super app incidents started from insecure APIs
- 62% of mobile apps examined had at least one critical vulnerability
- 39% of breaches involved third-party integrations
- 76% of users now expect businesses to follow GDPR-grade privacy
- Multi-service apps experienced a 110% rise in targeted cyberattacks due to their financial operations and high user volumes
A white-label Gojek app can be safe—if built and maintained with enterprise-grade security, continuous monitoring, and compliance-first engineering.
Read more : – Best Gojek Clone Scripts in 2025: Features & Pricing Compared
Key Security Risks & How to Identify Them
A white-label Gojek app handles rides, deliveries, payments, location tracking, chat, and vendor operations — which means security gaps can appear in multiple layers. Below are the highest-risk areas and how to identify them before they become real threats.
Data Protection & Privacy Risks
User personal information
Super apps collect sensitive data: names, emails, phone numbers, addresses, ID verification files, and behavioral data.
Payment data security
Wallet systems, card payments, and transaction history are attractive targets.
Location tracking concerns
Ride-booking requires real-time GPS tracking, which is extremely sensitive.
GDPR/CCPA compliance
Privacy laws require transparent data usage, deletion rights, consent management, and breach reporting.
Technical Vulnerabilities
Code quality issues
Poor coding practices lead to injection attacks, insecure storage, and API misconfigurations.
Server security gaps
If servers are not hardened, attackers can enter through misconfigurations.
API vulnerabilities
Since a Gojek-style app runs dozens of APIs, a single weak endpoint can expose the entire platform.
Third-party integrations
Payment gateways, SMS providers, map APIs, and analytics tools can create vulnerabilities.
Business Risks
Legal liability
If the app mishandles data or experiences a breach, business owners—not developers—are liable.
Reputation damage
One breach or financial fraud incident can destroy user trust instantly.
Financial losses
Fraud, chargebacks, and service manipulation can drain revenue.
Regulatory penalties
Non-compliance can lead to heavy fines under GDPR, RBI guidelines, or regional privacy laws.
Risk Assessment Checklist
| Security Area | Checklist Questions |
|---|---|
| Documentation & Transparency | Do they provide security documentation? |
| Code Quality & Maintenance | Is their codebase audited and updated regularly? |
| Security Testing | Do they offer VAPT reports? |
| API Protection | Are API gateways and rate limits implemented? |
| Data Security | Is user data encrypted at rest and in transit? |
| Compliance Standards | Do they follow ISO 27001 and SOC 2 standards? |
| Payment Security | Are payment modules PCI DSS compliant? |
| Disaster Preparedness | Is there a disaster recovery and backup plan? |
| Data Ownership | Do they provide clear data ownership rights? |
| Ongoing Security Support | Is there ongoing support for security updates? |
Security Standards Your White-label Gojek App Must Meet
To launch a safe, compliant, and scalable white-label Gojek app in 2025, your platform must adhere to strict global security standards. These aren’t optional — they are mandatory requirements for protecting user data, payment information, and operational integrity.
Essential Certifications
ISO 27001
A global gold standard for information security management. Ensures structured controls for data processing, storage, monitoring, and risk management.
SOC 2 Type II
Validates that the provider maintains secure systems for data confidentiality, processing integrity, and operational resilience.
GDPR
Regulates how user data must be collected, stored, processed, and deleted. Applies even if your business is outside the EU but handles EU user data.
HIPAA (if applicable)
Necessary only if your app includes health-related services such as telemedicine or wellness integrations.
PCI DSS
Required for any payment or wallet feature. Governs secure handling of card data and transaction security protocols.
Technical Requirements for a Secure White-label Gojek App
End-to-end encryption
All sensitive data — personal details, location, transactions — must be encrypted at rest and in transit.
Secure authentication
Supports 2FA, OTP-based login, OAuth, and session timeouts to prevent account hijacking.
Regular security audits
Monthly or quarterly audits to detect vulnerabilities early and maintain compliance.
Penetration testing
Simulated cyberattacks to evaluate weaknesses in APIs, mobile apps, and backend environments.
SSL certificates
Mandatory for all communication between users, drivers, vendors, and servers.
Secure API design
Follows OWASP API Security Top 10 guidelines. Includes rate limiting, token validation, encryption, and abuse detection.
Security Standards Comparison Table
| Security Requirement | Mandatory for Gojek-type Apps | What It Protects | Risk if Missing |
|---|---|---|---|
| ISO 27001 | Yes | Information security management | Weak data controls |
| SOC 2 Type II | Yes | Secure operations & data handling | Operational breaches |
| GDPR/CCPA | Yes | User privacy & data rights | Legal penalties |
| PCI DSS | Yes | Payment & wallet systems | Financial fraud |
| End-to-end encryption | Yes | Data confidentiality | Data theft |
| API security standards | Yes | API endpoints & integrations | API exploitation |
| VAPT | Yes | Full system vulnerability detection | Undiscovered threats |
| SSL certificates | Yes | Secure communication | MITM attacks |
| 2FA/OAuth | Recommended | Account protection | Account hijacking |
| Disaster recovery plan | Yes | Business continuity | Downtime & data loss |
These standards form the backbone of a secure super app ecosystem. Skipping even one opens the door to severe breaches.
Read more : – Top Uber Features Every Taxi App Needs
Red Flags – How to Spot Unsafe White-label Providers
Choosing the wrong provider can expose your white-label Gojek app to data breaches, financial fraud, legal penalties, and long-term operational risks. Before investing, you must understand the warning signs that signal poor security practices.
No security documentation
A legitimate provider should offer architecture documents, encryption details, compliance reports, and security policies.
If they cannot explain how user data is protected, it’s a red flag.
Cheap pricing without reason
Low-cost offers usually cut security corners: outdated code, no audits, insecure servers, or reused libraries with vulnerabilities.
No compliance certifications
If they cannot provide ISO 27001, SOC 2, PCI DSS, or GDPR alignment, they are not ready for enterprise-level deployment.
Outdated technology stack
Legacy frameworks, unsupported libraries, and old API versions create critical vulnerabilities.
Poor code quality
Messy, untested, or copied code increases the risk of injection attacks, API failures, and malware entry points.
No security updates policy
A secure Gojek-style super app requires continuous updates. One-time delivery with no update roadmap is a major risk.
Lack of data backup systems
Without automated backups and disaster recovery, your business is vulnerable to data loss and catastrophic downtime.
No insurance coverage
A mature provider should offer liability protection and security insurance to cover unforeseen breaches.
Evaluation Checklist
Use the following checklist when evaluating any provider:
Questions to ask providers
- How do you encrypt user data?
- What is your authentication mechanism?
- Do you conduct regular VAPT audits?
- Can you provide compliance documentation?
- How do you secure APIs and third-party integrations?
- What is your incident response process?
Documents to request
- Architecture blueprint
- Data flow diagrams
- Compliance certificates
- API documentation
- VAPT reports
- Security audit logs
- Server configurations and policies
Testing procedures
- Perform black-box and white-box testing
- Conduct API penetration tests
- Test for OWASP Mobile Top 10 vulnerabilities
- Run load/penetration tests on the backend
- Validate server hardening
Due diligence steps
- Review past deployments
- Interview existing clients
- Validate hosting infrastructure
- Check update frequency
- Confirm encryption standards
- Verify how long data is retained and why
These steps help you filter unsafe providers and ensure your white-label Gojek app is built on a trustworthy, compliant, and secure foundation.
Best Practices for Secure White-label Gojek App Implementation
A white-label Gojek app involves multiple moving parts — riders, drivers, vendors, wallets, payments, chat, deliveries, and real-time tracking. To keep this ecosystem secure, you must follow a structured security implementation plan both before launch and after going live.
Pre-launch Security
Security audit process
Before deployment, the entire app — mobile, backend, admin panel, APIs, and third-party modules — must undergo a full security audit.
This includes vulnerability scanning, threat modeling, API testing, and code-level assessments.
Code review requirements
Manual and automated code reviews ensure the app follows secure coding standards, removes unsafe libraries, and eliminates injection risks.
Look for linting, static analysis, and security review documentation.
Infrastructure hardening
Server hardening prevents unauthorized access and reduces attack surfaces.
This includes firewall setup, SSL enforcement, secure key management, DDOS protection, IAM controls, and restricted SSH access.
Compliance verification
All compliance requirements (ISO 27001, SOC 2, GDPR, PCI DSS) must be validated before launch.
Check if data retention, deletion, permission management, and audit trails are implemented correctly.
Staff training programs
Your internal team must be trained to handle the app securely:
- Data handling practices
- Access control
- Incident reporting
- Admin panel usage
- User verification processes
Human error is still the biggest cause of breaches, so training is essential.
Post-launch Monitoring
Continuous security monitoring
Real-time monitoring detects unusual activity, API abuse, fraudulent patterns, and unauthorized access attempts.
Regular updates and patches
A secure super app requires continuous patching for server libraries, mobile OS changes, API updates, and third-party services.
Incident response planning
A documented plan ensures your team knows exactly how to respond in case of:
- Data breach
- Unauthorized access
- Suspicious transactions
- Server attack
- Payment fraud
User data management
Includes proper encryption, regular data cleanup, permission checks, and secure storage with restricted access controls.
Backup and recovery systems
Automated backup schedules, replicated servers, and disaster recovery plans ensure the app can be restored without major downtime or data loss.
Security Implementation Timeline
| Phase | Key Tasks | Expected Duration |
|---|---|---|
| Pre-audit | Requirement analysis, app review, dependency mapping | 2–4 days |
| Code security checks | Code review, static analysis, fixing vulnerabilities | 5–10 days |
| Infrastructure setup | Hardening, SSL, firewall configuration | 3–5 days |
| Compliance alignment | GDPR, PCI DSS, ISO documentation | 4–7 days |
| Pre-launch testing | VAPT, penetration tests, API tests | 5–7 days |
| Post-launch security | Monitoring, patching, alerts | Ongoing |
A secure white-label Gojek app is not a one-time setup — it is a continuous security-first lifecycle.
Legal & Compliance Considerations
Launching a white-label Gojek app means handling sensitive data, real-time location tracking, financial transactions, and identity verification. This makes legal and regulatory compliance a core part of your security strategy—not an afterthought.
Regulatory Requirements
Data protection laws by region
Every country enforces different data protection standards. A Gojek-type app with users across multiple regions must comply with all applicable laws:
- GDPR: Europe
- CCPA/CPRA: California
- PDPA: Singapore
- PDP Bill: India
- LGPD: Brazil
- PIPEDA: Canada
Compliance requires clear consent, secure storage, user rights, breach notification, and strict data processing controls.
Industry-specific regulations
A multi-service app may include:
- Payments (requires PCI DSS compliance)
- Healthcare/wellness modules (requires HIPAA if applicable)
- Delivery and logistics (requires audit trails for tracking data)
Each module brings its own compliance responsibilities.
User consent management
You must implement:
- Clear consent forms
- Cookie and tracking transparency
- Data usage explanations
- Easy withdrawal of consent
- Opt-in and opt-out controls
Non-compliance leads to heavy fines.
Privacy policy requirements
A legally valid privacy policy must define:
- What data is collected
- Why it’s collected
- How it’s processed
- Where it’s stored
- Who can access it
- Retention periods
- User rights
- Breach response procedures
Terms of service essentials
Your terms must cover:
- Platform responsibilities
- User obligations
- Prohibited behaviours
- Liability limitations
- Dispute resolution
- Refund policies
- Suspension/termination conditions
Liability Protection
Insurance requirements
A white-label Gojek app should have cyber liability insurance to cover:
- Data breaches
- Financial fraud
- Server shutdown
- Technical failures
- Legal costs
Ask your provider if they include coverage.
Legal disclaimers
Your policies should include disclaimers about:
- Third-party service risks
- Driver/vendor misconduct
- Technical interruptions
- Data usage limitations
This protects you from unexpected lawsuits.
User agreements
Digital contracts must be enforceable and protect your business from:
- Misuse
- Fraud
- Abuse
- Policy violations
Incident reporting protocols
A strict reporting framework must outline:
- Response timelines
- Notification flow
- Communication templates
- Stakeholder responsibilities
- Documentation requirements
Regulatory compliance monitoring
Compliance is not a one-time event. You must conduct:
- Quarterly reviews
- Annual audits
- Policy updates
- Vendor risk assessments
Compliance Checklist by Region
| Region | Key Regulations | Required Controls |
|---|---|---|
| Europe | GDPR | Data rights, consent, encryption, breach reporting |
| USA | CCPA/CPRA | Opt-out rights, data sale disclosures, privacy controls |
| India | PDP Bill | Storage limitation, sensitive data protection |
| Singapore | PDPA | Purpose limitation, consent framework |
| Brazil | LGPD | Data processing rights, privacy notices |
| Canada | PIPEDA | Fair information practices, secure data handling |
A legally compliant foundation protects your users and shields your business from penalties, lawsuits, and operational disruption.
Why Miracuves White-label Gojek App Is Your Safest Choice
A white-label Gojek app operates at the highest-risk intersection of technology: real-time location tracking, multi-service bookings, payments, vendor management, and identity verification. Security cannot be optional. Miracuves is engineered from the ground up with an enterprise-grade security architecture that eliminates the risks most providers ignore.
Below is a clear breakdown of why Miracuves stands out as a security-first technology partner.
Miracuves Security Advantages
- Regular security audits and certifications
Our systems undergo scheduled internal and third-party audits following ISO 27001 and SOC 2 Type II principles, ensuring every deployment meets global security benchmarks. - GDPR/CCPA compliant by default
We implement user consent controls, data rights management, transparent processing logs, and privacy policies aligned with global regulations—so your app stays compliant wherever it operates. - 24/7 security monitoring
With real-time threat detection, API monitoring, anomaly alerts, and automated incident reporting, security is continuously enforced, not periodically checked. - Encrypted data transmission
All sensitive information—location data, payment details, chat messages, and transactional logs—is encrypted using industry-leading protocols at rest and in transit. - Secure payment processing
Our wallet and payment modules follow PCI DSS principles, with tokenization, fraud detection layers, and secure transaction flows to eliminate financial risk. - Regular security updates
Miracuves provides continuous updates for frameworks, SDK patches, OS versions, APIs, and emerging threat protection.
Miracuves provides continuous updates for:
- Framework changes
- Third-party SDK patches
- OS version updates
- API enhancements
- New threat protection mechanisms
This ensures your app never becomes outdated or vulnerable.
Insurance coverage included
Miracuves offers business liability and security assurance so you’re protected from unforeseen breach-related losses or operational failures.
conclusion
Don’t compromise on security.
Miracuves white-label Gojek app solutions come with enterprise-grade security built-in—from encrypted data flows to full compliance and continuous monitoring. With over 600 successful deployments and zero major security breaches, Miracuves is trusted worldwide for secure, scalable super app development.
A white-label Gojek app can be incredibly powerful—but only when built on a secure, compliant, and continuously protected foundation. Security is not a feature; it’s the backbone of your entire business. Choosing the right partner determines whether your platform becomes a trusted super app or a vulnerable target. With the right standards, audits, and a security-focused provider like Miracuves, your super app can scale confidently, handle millions of users, and stay protected in an increasingly risky digital landscape.
Get a free security assessment today and see why businesses rely on Miracuves for safe, compliant, and future-ready platforms.
FAQs
1. How secure is a white-label Gojek app compared to custom development?
Equally secure or even safer when built by a provider with audited, time-tested architecture and compliance standards.
2. What happens if there’s a security breach?
A proper response plan includes immediate isolation, breach assessment, notification, patching, and recovery. Miracuves provides full incident handling support.
3. Who is responsible for security updates?
Your provider must deliver regular patches, SDK updates, API fixes, and server optimizations. Miracuves handles continuous updates.
4. How is user data protected?
Through encryption, secure servers, protected APIs, consent-based access, and global data privacy compliance.
5. What compliance certifications should I look for?
ISO 27001, SOC 2 Type II, PCI DSS, GDPR/CCPA, and OWASP Mobile Top 10 compliance.
6. Can a white-label Gojek app meet enterprise security standards?
Yes, if it includes encryption, secure authentication, VAPT, API hardening, and compliance controls.
7. How often should security audits be conducted?
Monthly or quarterly, depending on usage volume and new feature rollouts.
8. What’s included in Miracuves’ security package?
Encryption, secure APIs, compliance setup, monitoring, audits, insurance coverage, and 24/7 security oversight.
9. How do I manage security in different countries?
Follow regional data laws (GDPR, CCPA, PDPA, PDP Bill) and deploy localized compliance policies.
10. What insurance does my app need?
Cyber liability insurance to protect against breaches, fraud, data loss, and operational failures.