You’ve heard the horror stories — data leaks exposing personal details, fake profiles hijacking professional identities, and unprotected APIs leaving user data vulnerable. In a digital ecosystem where professional trust is everything, one security breach can destroy not just an app — but an entire brand’s credibility.
That’s why white-label LinkedIn app security has become a front-line concern in 2025. With thousands of businesses deploying ready-made networking platforms, ensuring these apps meet enterprise-grade safety standards is more critical than ever.
In this article, we’ll go beyond generic promises and provide a realistic, fact-based assessment of how secure a white-label LinkedIn-style app truly is. You’ll learn what risks exist, which security frameworks matter, and how providers like Miracuves deliver airtight protection for your platform and your users.
Understanding white-label LinkedIn app security landscape
When businesses choose a white-label LinkedIn app, they often assume it’s as secure as the original platform. But that’s not always true — security depends on the developer’s architecture, coding standards, and ongoing compliance practices.
White-label security means adopting a shared responsibility model where the provider ensures backend protection while the client manages operational and user-level safety. It’s about implementing enterprise-grade defenses without the cost or time of building from scratch.
People worry about white-label apps because data exposure risks have grown exponentially. The current threat landscape for social networking and professional platforms includes phishing attacks, credential stuffing, and unauthorized data scraping.
Security standards in 2025 emphasize continuous auditing, GDPR compliance, and SOC 2 Type II validation. A 2025 Statista report revealed that nearly 43% of social networking app breaches were due to third-party API vulnerabilities — a key reason to choose verified providers who practice secure API design.
A white-label LinkedIn app must therefore be built on strong encryption, verified hosting infrastructure, and regular vulnerability assessments to ensure safe user engagement and data exchange.
Key security risks and how to identify them
Security in a white-label LinkedIn app is not just about coding—it’s about identifying and mitigating risks across every layer: data, technology, and business operations. Below is a breakdown of the major risk zones and how to evaluate them effectively.
Data protection and privacy risks
- User personal information: Professional profiles often contain sensitive personal and corporate data. Any weak encryption or storage flaw can lead to identity theft or data leaks.
- Payment data security: If your app includes premium memberships or job-posting payments, PCI DSS compliance is critical to prevent card fraud.
- Location tracking concerns: Many networking apps use location features. Without explicit consent or anonymization, this can breach GDPR and CCPA.
- GDPR/CCPA compliance: Your provider must demonstrate clear data handling, deletion, and consent protocols to avoid regulatory penalties.
Technical vulnerabilities
- Code quality issues: Poorly written or unreviewed code can expose injection and authentication flaws.
- Server security gaps: Misconfigured servers or outdated frameworks often become targets for DDoS or brute-force attacks.
- API vulnerabilities: Third-party or unprotected APIs are among the top entry points for data breaches.
- Third-party integrations: Plugins for analytics, ads, or chat systems can introduce indirect security weaknesses.
Business risks
- Legal liability: In case of a breach, both the app owner and white-label provider may face legal action.
- Reputation damage: Even a minor breach can erode user trust, making recovery expensive and slow.
- Financial losses: Breach management, fines, and lost subscriptions can cripple startups.
- Regulatory penalties: Non-compliance with data laws can attract multi-million-dollar fines, especially in the EU and US.
Risk assessment checklist
- Verify encryption and storage mechanisms
- Audit all API endpoints and third-party libraries
- Check compliance certificates and audit logs
- Review data retention and deletion policies
- Ensure backup and disaster recovery measures are in place
A strong security posture begins with transparent code practices, regular audits, and compliance-backed architecture—not assumptions.
Read more : – Key Features to Include in a LinkedIn Clone App
Security standards your white-label LinkedIn app must meet
Security is not a one-time setup; it’s an ongoing process backed by international standards and regular compliance checks. A secure white-label LinkedIn app should follow a mix of global certifications and strong technical practices to ensure both regulatory and operational protection.
Essential certifications
- ISO 27001 compliance: Demonstrates a systematic approach to managing sensitive information, ensuring confidentiality and integrity.
- SOC 2 Type II: Validates that the app’s data handling, security, and availability controls are audited regularly.
- GDPR compliance: Ensures data collection, storage, and processing meet European Union privacy requirements.
- HIPAA (if applicable): Relevant for apps handling health-related professional data or medical networks.
- PCI DSS for payments: Mandatory for any app processing transactions, ensuring cardholder data safety.
Technical requirements
- End-to-end encryption: Protects messages, user data, and communication channels from interception.
- Secure authentication (2FA/OAuth): Prevents unauthorized account access and impersonation.
- Regular security audits: Identifies vulnerabilities and ensures proactive patching.
- Penetration testing: Simulates attacks to uncover weaknesses before real hackers do.
- SSL certificates: Encrypts data in transit, preventing data interception.
- Secure API design: Protects third-party integrations and data exchange endpoints from misuse.
Security standards comparison table
| Standard / Requirement | Purpose | Applicability |
|---|---|---|
| ISO 27001 | Information security management | All business and social apps |
| SOC 2 Type II | Security, availability, and confidentiality | SaaS and hosted apps |
| GDPR | Data protection and user privacy | Global (mandatory in EU) |
| PCI DSS | Payment data protection | Apps with payment modules |
| SSL/TLS | Secure data transmission | All web and mobile platforms |
| Penetration Testing | Vulnerability detection | Recommended quarterly |
Meeting these standards ensures the app not only prevents data breaches but also meets user and enterprise trust expectations in 2025.
Read more : – Top 5 Mistakes Startups Make When Building a LinkedIn Clone
Red flags: how to spot unsafe white-label providers
Not every provider claiming “enterprise-level security” truly delivers it. Some cut costs by skipping audits, using outdated frameworks, or neglecting compliance altogether. Identifying these warning signs early can save you from costly breaches later.
- No transparent security documentation or audit reports
- Extremely low pricing without clear justification
- Absence of compliance certifications such as ISO 27001 or SOC 2
- Use of outdated or unmaintained technology stacks
- Unclear or inconsistent code quality
- No structured update or patch policy
- Missing data backup and recovery procedures
- No liability or insurance coverage
Evaluation checklist
Before selecting a white-label LinkedIn app provider, use this simple due diligence checklist:
- Ask for third-party audit certificates and vulnerability assessment reports
- Request a complete list of security measures implemented in both app and backend
- Verify their compliance with GDPR, CCPA, and PCI DSS if applicable
- Inspect their disaster recovery and data retention policy
- Conduct a test deployment or penetration test before signing the final contract
- Confirm they offer regular updates and long-term security support
A secure provider is transparent, proactive, and accountable. They don’t just talk about compliance—they demonstrate it through documented evidence and consistent testing.
Best practices for secure white-label LinkedIn app implementation
Building a white-label LinkedIn app that is both scalable and secure requires a combination of preventive strategies before launch and continuous vigilance afterward. The goal is not just compliance but true operational security that protects user data and brand reputation.
Pre-launch security
- Security audit process: Conduct independent vulnerability assessments and penetration tests before deployment.
- Code review requirements: Every line of code should be reviewed by qualified auditors to eliminate injection, API, and logic flaws.
- Infrastructure hardening: Implement firewalls, SSL, and strict access control across servers and databases.
- Compliance verification: Ensure all regional and international data privacy laws (GDPR, CCPA) are fully met before app rollout.
- Staff training programs: Educate developers and administrators on secure coding, phishing prevention, and data handling.
Post-launch monitoring
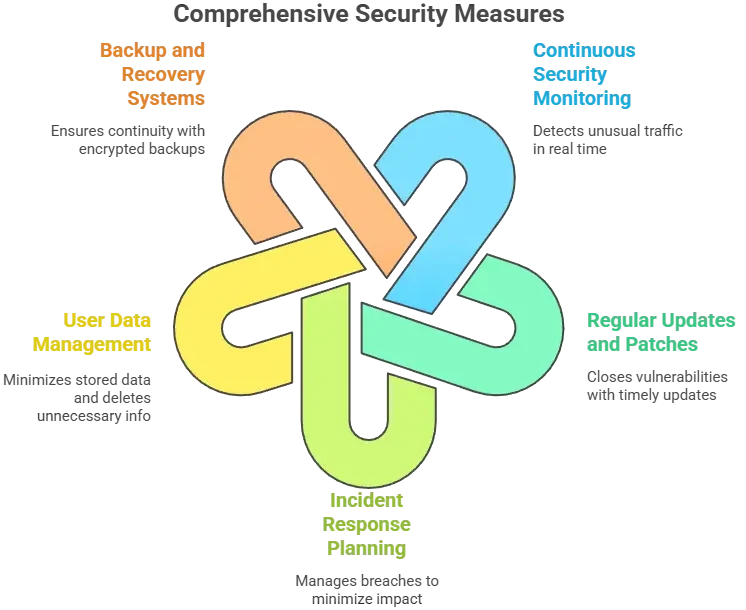
Security implementation timeline
| Phase | Key Activities | Duration |
|---|---|---|
| Planning | Define compliance scope and select security frameworks | 1–2 weeks |
| Development | Implement secure coding and testing practices | 3–4 weeks |
| Pre-launch | Conduct audits, reviews, and penetration tests | 1–2 weeks |
| Post-launch | Continuous monitoring and scheduled updates | Ongoing |
Following these best practices ensures that your white-label LinkedIn app not only passes compliance checks but also builds long-term trust with users and partners.
Legal and compliance considerations
Security is only half the story — the other half lies in staying legally compliant across all operating regions. A white-label LinkedIn app handles sensitive professional data, meaning it must follow strict privacy, data protection, and consent regulations to avoid lawsuits or fines.
Regulatory requirements
- Data protection laws by region: The app must comply with GDPR in Europe, CCPA in California, and similar laws in India, Singapore, and Australia.
- Industry-specific regulations: If the platform caters to healthcare or finance professionals, additional standards like HIPAA or FINRA may apply.
- User consent management: Every data collection activity should be tied to clear, revocable user consent. No data should be stored or shared without it.
- Privacy policy requirements: The privacy policy must detail data handling, retention periods, and third-party sharing.
- Terms of service essentials: Must define user rights, acceptable use, and limitations of liability to protect both provider and owner.
Liability protection
- Insurance requirements: Cyber liability insurance should cover data breaches, ransom attacks, and regulatory penalties.
- Legal disclaimers: Clearly communicate data usage responsibilities between the app provider and owner.
- User agreements: Draft strong EULAs and service terms that assign security duties transparently.
- Incident reporting protocols: Define how and when users and authorities are informed in case of data breaches.
- Regulatory compliance monitoring: Continuously track changes in data laws and update documentation to stay aligned with evolving legal standards.
Compliance checklist by region
| Region | Key Regulation | Required Measures |
|---|---|---|
| European Union | GDPR | Consent management, user data control, encryption |
| United States | CCPA, FTC Act | User disclosure, opt-out systems, data portability |
| India | DPDP Act 2023 | Explicit consent, data localization, user access rights |
| Middle East | DIFC, ADGM | Data classification, storage limitation |
| Asia-Pacific | PDPA (Singapore), APP (Australia) | Security safeguards, transparency policies |
Maintaining up-to-date legal compliance not only prevents penalties but also enhances credibility, helping users trust the integrity and reliability of your professional networking platform.
Why Miracuves white-label LinkedIn app is your safest choice
When it comes to professional networking platforms, Miracuves goes beyond development — it delivers security-engineered infrastructure designed to protect both users and enterprises from every possible risk. Our white-label LinkedIn app isn’t just compliant; it’s built with proactive defense mechanisms that evolve with new security challenges.
Miracuves security advantages
- Enterprise-grade security architecture: Our apps are built on ISO 27001 and SOC 2 Type II–certified frameworks ensuring data protection from the ground up.
- Regular security audits and certifications: Every deployment undergoes independent audits, vulnerability scans, and penetration testing.
- GDPR/CCPA compliant by default: User data handling, consent management, and storage meet global privacy standards.
- 24/7 security monitoring: Real-time tracking and automated alerts prevent potential breaches before they escalate.
- Encrypted data transmission: All communication between client, server, and third-party APIs is secured with 256-bit SSL encryption.
- Secure payment processing: PCI DSS compliance ensures safe transactions for premium memberships and ad payments.
- Regular security updates: All clients receive free updates to stay protected from evolving threats.
- Insurance coverage included: Miracuves solutions include cyber liability protection for maximum business continuity.
Conclusion
Don’t compromise on security. Miracuves white-label LinkedIn app solutions come with enterprise-grade safety built in. Our 600+ successful projects have maintained zero major security breaches. Get a free security assessment and discover why businesses trust Miracuves for compliant, scalable, and future-ready platforms.
The safest and most sustainable approach is to partner with a provider that prioritizes compliance, transparency, and continuous protection. Miracuves stands out by combining robust engineering with global security standards, ensuring that every app is not only fast to launch but fortified against modern threats.
When you choose a Miracuves white-label LinkedIn app, you’re not just deploying a product — you’re investing in long-term reliability, legal compliance, and enterprise-grade peace of mind.
FAQs
1. How secure is a white-label app compared to custom development?
A well-developed white-label app can be just as secure as a custom-built one — provided it’s maintained, audited, and updated regularly. Security depends on practices, not origin.
2. What happens if there’s a security breach?
A proper incident response plan activates immediately: detection, isolation, communication, and recovery. Miracuves includes predefined response protocols to minimize downtime and data loss.
3. Who is responsible for security updates?
Miracuves manages ongoing patching, vulnerability fixes, and compliance updates. Clients only need to maintain user-level policies like passwords and access controls.
4. How is user data protected in white-label apps?
All sensitive data is encrypted both in transit (via SSL/TLS) and at rest. Access is restricted using role-based authentication and activity logs.
5. What compliance certifications should I look for?
ISO 27001, SOC 2 Type II, and GDPR compliance are essential for all social networking or professional apps. For payment-enabled apps, PCI DSS is also mandatory.
6. Can white-label apps meet enterprise security standards?
Yes. With features like secure APIs, encryption, audit trails, and authentication frameworks, they can fully match enterprise-grade security expectations.
7. How often should security audits be conducted?
Quarterly audits are recommended. Miracuves performs internal and third-party audits every three months to ensure zero-gap compliance.
8. What’s included in Miracuves’ security package?
Regular security audits, compliance reports, encrypted hosting, insurance coverage, and lifetime update support.
9. How to handle security across different countries?
Miracuves ensures region-specific compliance (GDPR for EU, CCPA for California, DPDP Act for India) to meet international data protection standards.
Related Article:








