You’ve heard the horror stories about data breaches, leaked customer details, hacked payment systems, and businesses losing user trust overnight. When you plan to launch a white-label Talabat app, one question naturally dominates every serious founder’s mind: Is my app truly safe?
In 2025, food delivery platforms handle far more than just orders. They process real-time locations, store sensitive customer profiles, manage digital wallets, and move millions in online transactions. A single security failure can trigger legal action, regulatory penalties, massive revenue loss, and irreversible brand damage.
White-label apps bring speed and cost efficiency, but they also introduce a critical responsibility: ensuring that enterprise-level security is not compromised for faster deployment. The safety of your users, merchants, and business reputation depends entirely on how well your platform is protected from modern cyber threats.
This guide delivers an honest, in-depth security assessment of white-label Talabat app safety in 2025. You will understand real risks, global compliance requirements, practical protection strategies, and how Miracuves builds security-first food delivery platforms that businesses can trust with confidence.
Understanding White-Label Talabat App Security Landscape
What “White-Label Security” Actually Means
White-label security refers to the protection framework built into a ready-made food delivery app that is rebranded and deployed for your business. The core security architecture is shared, while your responsibility lies in configuration, compliance, and operations.
Common Security Myths vs Reality
Many founders believe white-label apps are inherently unsafe. In reality, security depends on the provider’s infrastructure, coding standards, and compliance maturity—not on the white-label model itself.
Why People Worry About White-Label Apps
Concerns arise from past data breaches, low-cost unsafe providers, and lack of transparency in code ownership, server control, and compliance documentation.
Current Threat Landscape for Talabat-Type Platforms
Food delivery apps face high-frequency attacks including payment fraud, API abuse, account takeovers, location tracking exploits, and database intrusions targeting customer and merchant data.
Security Standards in 2025
Modern platforms must follow zero-trust architecture, continuous monitoring, encrypted cloud infrastructure, and real-time threat detection systems.
Real-World Statistics on App Security Incidents
In 2024–2025, over 62% of food and e-commerce app breaches originated from insecure APIs and misconfigured cloud servers, with average breach recovery costs exceeding $3.9 million per incident.
Key Security Risks & How to Identify Them
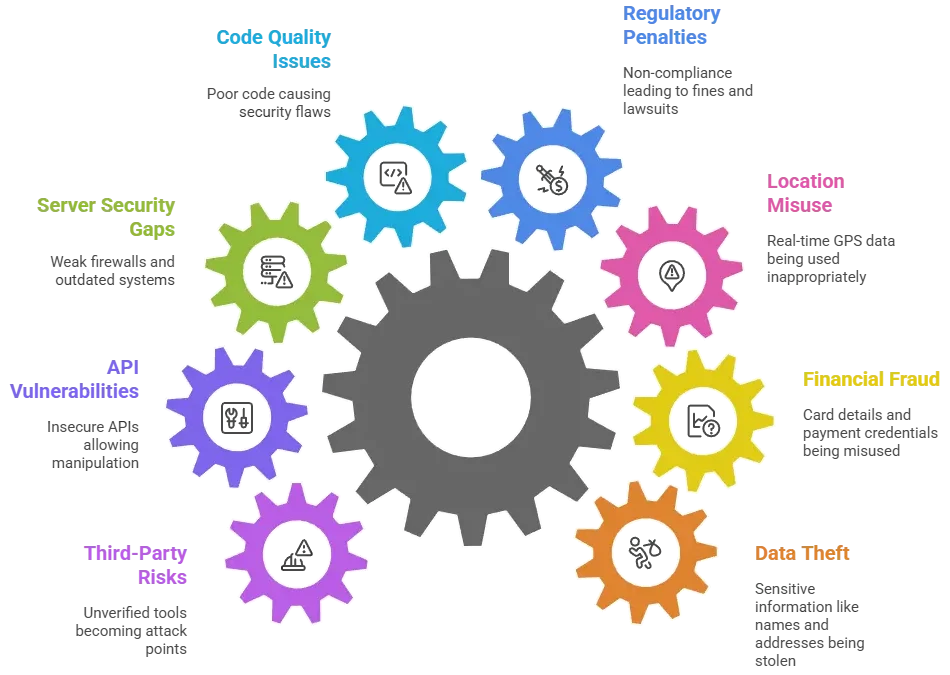
Business Risks
Legal Liability
Data leaks can trigger class-action lawsuits and government investigations.
Reputation Damage
Loss of user trust directly impacts long-term growth and brand credibility.
Financial Losses
Chargebacks, fraud, and downtime lead to direct revenue loss.
Regulatory Penalties
Non-compliance can invite fines running into millions depending on the region.
Risk Assessment Checklist
- Is all user and payment data encrypted?
- Are APIs protected with authentication and rate limits?
- Are cloud servers configured using security best practices?
- Are third-party tools vetted for security compliance?
- Is regular vulnerability testing conducted?
Read more : – How to Create an App Like Talabat: Essential Steps, Costs, and Features
Security Standards Your White-Label Talabat App Must Meet
Essential Certifications
ISO 27001 Compliance
Ensures a structured information security management system across infrastructure, data handling, and access controls.
SOC 2 Type II
Validates long-term operational security for availability, integrity, and confidentiality.
GDPR Compliance
Mandatory for handling personal data of users in EU regions with strict consent and data usage rules.
HIPAA (If Applicable)
Required only when health-related food services, nutrition tracking, or medical meal delivery is involved.
PCI DSS for Payments
Compulsory standard for processing debit cards, credit cards, wallets, and online transactions.
Technical Requirements
End-to-End Encryption
Protects user data from device to server using industry-grade cryptographic protocols.
Secure Authentication (2FA / OAuth)
Prevents unauthorized access through multi-layer identity verification.
Regular Security Audits
Identifies vulnerabilities before attackers exploit them.
Penetration Testing
Simulated cyberattacks to test system resilience under real-world conditions.
SSL Certificates
Encrypts communication channels between users and the platform.
Secure API Design
Prevents unauthorized data exposure and system manipulation.
Security Standards Comparison Table
| Security Standard | Purpose | Mandatory for Talabat App |
|---|---|---|
| ISO 27001 | Overall information security framework | Yes |
| SOC 2 Type II | Operational and cloud security assurance | Yes |
| GDPR | User data protection (EU) | Yes |
| PCI DSS | Payment security | Yes |
| HIPAA | Health data protection | Conditional |
Red Flags – How to Spot Unsafe White-Label Providers
Warning Signs
No Security Documentation
If a provider cannot share security architecture, audit reports, or compliance proof, it indicates weak internal controls.
Cheap Pricing Without Explanation
Unrealistically low pricing often means compromised infrastructure, reused insecure code, or no long-term security investment.
No Compliance Certifications
Absence of ISO, SOC, GDPR, or PCI certifications exposes your business to regulatory and legal risk.
Outdated Technology Stack
Old frameworks and unsupported server versions are highly vulnerable to modern cyberattacks.
Poor Code Quality
Lack of coding standards increases the chances of injection attacks, data leaks, and system failures.
No Security Updates Policy
Providers who do not commit to regular updates leave your system exposed to newly discovered threats.
Lack of Data Backup Systems
Without structured backups, recovery after ransomware or system failure becomes nearly impossible.
No Insurance Coverage
Cyber insurance is a key indicator of a mature and responsible technology provider.
Evaluation Checklist
Questions to Ask Providers
- Do you follow ISO 27001 or SOC 2?
- How often are security audits conducted?
- How is payment data handled and stored?
- What is your incident response time?
Documents to Request
- Security audit reports
- Compliance certificates
- Data processing agreements
- Penetration testing summaries
Testing Procedures
- Vulnerability assessment
- Load and stress testing
- API security validation
Due Diligence Steps
- Background verification
- Past breach history review
- Client security references
- Infrastructure inspection
Read more : – White-Label Delivery Hero App Security: What You Must Know in 2025
Best Practices for Secure White-Label Talabat App Implementation
Pre-Launch Security
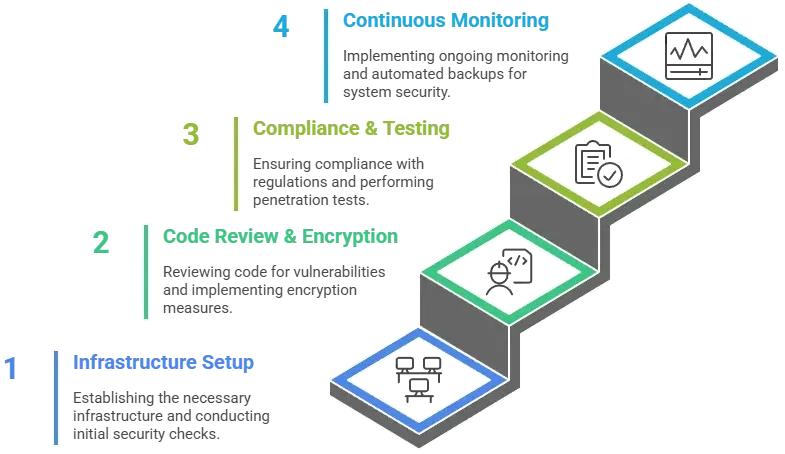
Security Audit Process
A full vulnerability assessment must be conducted before the app goes live to detect weak points in code, servers, and integrations.
Code Review Requirements
Source code should be reviewed for logical flaws, insecure functions, and dependency risks.
Infrastructure Hardening
Firewalls, intrusion detection systems, and secure cloud configurations must be deployed before production access.
Compliance Verification
All required certifications, legal policies, and regulatory checks must be verified prior to launch.
Staff Training Programs
Operational and support teams must be trained to handle data securely and respond to security alerts.
Post-Launch Monitoring
Continuous Security Monitoring
Live monitoring tools must track threats, abnormal behavior, and breach attempts in real time.
Regular Updates and Patches
Security patches must be rolled out immediately after vulnerabilities are discovered.
Incident Response Planning
A predefined breach response plan ensures quick containment, investigation, and communication.
User Data Management
Access to sensitive data must be role-based with activity logging and audit trails.
Backup and Recovery Systems
Automated encrypted backups must be stored on secure off-site environments for disaster recovery.
Security Implementation Timeline
Legal & Compliance Considerations
Regulatory Requirements
Data Protection Laws by Region
Different regions follow different data laws such as GDPR in Europe, CCPA in California, DPDP Act in India, and PDPL in Middle East countries. Your Talabat-type app must align with the law of every market you operate in.
Industry-Specific Regulations
Food safety laws, digital payment regulations, and courier delivery compliance also apply to food delivery platforms.
User Consent Management
Users must expressly approve data collection, location access, and marketing permissions.
Privacy Policy Requirements
Your app must clearly disclose what data is collected, how it is used, where it is stored, and how users can request deletion.
Terms of Service Essentials
Legal terms must define liabilities, user responsibilities, refund policies, and platform usage rules.
Liability Protection
Insurance Requirements
Cyber liability insurance protects your business against breach recovery costs, lawsuits, and regulatory fines.
Legal Disclaimers
Disclaimers limit risk related to delivery delays, service interruptions, and third-party integrations.
User Agreements
Strong agreements protect the platform from misuse and fraudulent activities.
Incident Reporting Protocols
Clear breach reporting timelines must comply with regional regulatory mandates.
Regulatory Compliance Monitoring
Continuous compliance tracking ensures you stay updated with changing digital laws.
Compliance Checklist by Region
| Region | Key Regulations | Mandatory |
|---|---|---|
| Europe | GDPR, PCI DSS | Yes |
| USA | CCPA, PCI DSS | Yes |
| India | DPDP Act, RBI Guidelines | Yes |
| Middle East | PDPL, PCI DSS | Yes |
| Global | ISO 27001, SOC 2 | Strongly Recommended |
Why Miracuves White-Label Talabat App Is Your Safest Choice
Miracuves Security Advantages
Enterprise-Grade Security Architecture
Miracuves applications are built on hardened cloud infrastructure with layered security controls, firewalls, and intrusion detection systems.
Regular Security Audits and Certifications
All platforms undergo scheduled vulnerability assessments and penetration testing to maintain compliance with global security standards.
GDPR / CCPA Compliant by Default
Built-in consent management, encrypted storage, and data access controls ensure automatic compliance with major privacy laws.
24/7 Security Monitoring
Real-time monitoring tracks suspicious activity, unauthorized access attempts, and abnormal system behavior without downtime.
Encrypted Data Transmission
All data exchanges between users, servers, and payment gateways are protected using industry-grade encryption protocols.
Secure Payment Processing
Miracuves integrates only PCI DSS–compliant payment gateways with tokenized transaction handling.
Regular Security Updates
Security patches and framework upgrades are deployed continuously to safeguard against newly discovered vulnerabilities.
Insurance Coverage Included
Cyber risk protection and liability safeguards are built into the service framework for complete business protection.
Final thought
Don’t compromise on security. Miracuves white-label Talabat app solutions come with enterprise-grade security built-in. Our 600+ successful projects have maintained zero major security breaches. Get a free security assessment and see why businesses trust Miracuves for safe, compliant platforms.
Security is not an optional feature in a white-label Talabat app—it is the foundation of long-term business survival. Choosing a provider that prioritizes compliance, infrastructure protection, and continuous monitoring is the only way to build lasting user trust in 2025.
FAQs
1. How secure is a white-label Talabat app compared to custom development?
Security depends on the provider’s infrastructure and standards. A certified white-label app can be as secure as custom development.
2. What happens if a security breach occurs?
Immediate containment, forensic investigation, user notification, and regulatory reporting are required.
3. Who is responsible for security updates?
The technology provider handles core updates, while the business manages operational security.
4. How is user data protected in a white-label Talabat app?
Through encryption, access control, secure servers, and compliance-based data handling.
5. What compliance certifications should I look for?
ISO 27001, SOC 2 Type II, GDPR, and PCI DSS.
6. Can white-label apps meet enterprise security standards?
Yes, when built on enterprise-grade cloud infrastructure with continuous audits.
7. How often should security audits be conducted?
At least once every 6–12 months, with ongoing internal monitoring.
8. What is included in the Miracuves security package?
Encrypted infrastructure, compliance readiness, monitoring, secure payments, and regular updates.
9. How is security handled across different countries?
By aligning the app with region-specific data protection and payment regulations.
10. What insurance is needed for app security?
Cyber liability, data breach response, and technology errors insurance.
Related articles:








