You have heard the horror stories about data breaches, leaked customer information, and payment fraud destroying perfectly good food delivery businesses overnight. When you invest in a white-label UberEats app, one question naturally dominates your thinking: Is it actually safe?
In 2025, food delivery platforms process enormous volumes of sensitive data—customer addresses, phone numbers, real-time location tracking, payment details, restaurant business data, and driver identity information. A single security lapse can expose thousands of users, invite regulatory penalties, and permanently damage brand trust. Security is no longer a technical feature. It is your business foundation.
Yet, many entrepreneurs still assume that a white-label app is inherently less secure than custom development. Others blindly trust low-cost vendors without understanding what protection is really in place. Both assumptions are risky.
In this guide, we will deliver an honest, technical, and business-focused assessment of white-label UberEats app security in 2025. You will learn the real risks, the compliance standards you must meet, how to evaluate providers, and how to implement enterprise-grade protection without slowing down your launch.
Most importantly, you will see how a security-first development approach—like the one followed by Miracuves—allows you to launch fast without compromising user safety, regulatory compliance, or long-term trust.
Understanding White-Label UberEats App Security Landscape
What “White-Label UberEats App Security” Actually Means
White-label UberEats app security refers to the protection framework built into a pre-developed food delivery platform that is rebranded and customized for different businesses. Unlike custom development where security is built from scratch, a white-label app relies on a shared core codebase that is hardened, tested, and deployed across multiple clients.
In a secure white-label model, security is managed at three critical layers:
- Application layer (app code, authentication, APIs)
- Infrastructure layer (servers, cloud, databases)
- Compliance layer (legal, data protection, audits)
The safety of your business does not depend on the “white-label” label itself. It depends entirely on how seriously the provider treats code security, data handling, and regulatory compliance

Why People Worry About White-Label UberEats Apps
Security concerns typically arise from legitimate business fears:
- Exposure of customer payment data
- Unauthorized access to delivery partner accounts
- Manipulation of order pricing or commissions
- Data leaks of restaurant performance metrics
- Identity misuse of drivers and customers
- Regulatory fines under GDPR and payment laws
Food delivery platforms also operate in high-fraud environments. Fake orders, card testing fraud, coupon abuse, and location spoofing are common attack vectors. This makes UberEats-type apps a prime target for cybercriminals.
Current Threat Landscape for UberEats-Type Platforms in 2025
In 2025, food delivery apps face a more complex threat profile than ever before:
- Account Takeover Attacks (ATO): Automated credential stuffing targeting customer and driver accounts
- Payment Card Fraud: Test transactions using stolen cards
- API Exploits: Attackers probing weak backend endpoints
- Location Spoofing: Fake GPS to manipulate delivery zones and incentives
- Ransomware: Attacks on cloud databases holding order and payment records
- Insider Threats: Misuse of admin access at vendor or franchise level
Industry security reports indicate that over 42 percent of food delivery platforms experienced at least one critical security incident between 2023 and 2024. The majority of breaches occurred due to poor API security and weak authentication systems.
Security Standards in 2025
In 2025, a secure white-label UberEats app is expected to meet the following baseline standards:
- Cloud-native security architecture
- Zero-trust access control
- End-to-end data encryption
- Secure API gateway architecture
- Continuous vulnerability scanning
- Automated incident detection and response
These standards are no longer “enterprise extras.” They are now minimum startup requirements.
Real-World Statistics on App Security Incidents
- Over 70 percent of food delivery app breaches originate from backend vulnerabilities, not mobile apps
- Nearly 1 in 3 breaches involve exposed APIs
- The average cost of a data breach in on-demand delivery platforms crossed USD 4.1 million in 2024
- GDPR penalties related to delivery apps increased by 29 percent year-over-year in Europe
- Payment fraud losses in food delivery crossed USD 1.2 billion globally
These numbers highlight one truth clearly: launching fast without security planning is no longer a viable business strategy.
Key Security Risks & How to Identify Them
A white-label UberEats app operates at the intersection of payments, real-time location tracking, customer data, and merchant systems. That makes it one of the most security-sensitive consumer platforms you can launch. Understanding where the real risks exist is the first step toward preventing costly breaches.
Below are the most critical risk categories every food delivery business must evaluate before launch.
Data Protection & Privacy Risks
Food delivery platforms collect and process extremely sensitive personal and financial data daily. Any weakness here can instantly trigger legal action and public trust collapse.
User Personal Information
- Names, phone numbers, email addresses
- Home and office delivery locations
- Order histories and behavior tracking
- Device identifiers and IP addresses
Risk occurs when:
- Databases are not properly encrypted
- Access controls are poorly implemented
- Admin privileges are excessive or unmanaged
Payment Data Security
- Credit and debit card numbers
- Transaction histories
- Refund and wallet balances
Major risks include:
- Storing card data without PCI DSS compliance
- Insecure payment gateways
- Poor tokenization practices
Location Tracking Concerns
- Real-time GPS tracking of customers and delivery partners
- Route history storage
If location data is leaked, it creates:
- Physical safety risks
- Legal exposure under privacy laws
- Severe reputational damage
GDPR and CCPA Compliance Gaps
- Improper consent management
- Lack of data deletion controls
- No breach notification process
Non-compliance can result in:
- Heavy regulatory fines
- Forced platform shutdowns
- Long-term trust erosion
Technical Vulnerabilities
These are the most common causes of successful cyberattacks on UberEats-type platforms.
Code Quality Issues
- Hardcoded credentials
- Poor session management
- Weak encryption logic
- Insecure file handling
Low-quality code exponentially increases breach probability.
Server Security Gaps
- Open ports
- Outdated operating systems
- Weak firewall rules
- Poor access policies
A single exposed server can compromise the entire platform.
API Vulnerabilities
- Insecure endpoints
- Missing authentication on backend APIs
- No rate limiting or abuse protection
APIs are the most frequently exploited attack surface in food delivery apps.
Third-Party Integrations
- Map services
- Payment gateways
- SMS and notification services
- Restaurant POS systems
Each third-party connection widens the attack surface if not securely sandboxed.ea3
Business Risks
Security failures do not stay technical for long. They rapidly become business disasters.
Legal Liability
- Lawsuits from affected users
- Regulatory investigations
- Contract violations with payment providers
Reputation Damage
- Loss of customer trust
- Restaurant partner attrition
- Media exposure of breaches
Trust once broken in a food delivery business is extremely difficult to rebuild.
Financial Losses
- Fraudulent transactions
- Chargebacks and payment disputes
- Ransomware demands
- Emergency security response costs
Regulatory Penalties
- GDPR fines up to 4 percent of global revenue
- PCI DSS non-compliance penalties
- Local digital data protection law violations
White-Label UberEats App Risk Assessment Checklist
Use this checklist to quickly assess your exposure level:
- Is all customer and driver data encrypted at rest and in transit?
- Are payment transactions fully PCI DSS compliant?
- Are APIs protected with authentication, throttling, and monitoring?
- Is real-time location data stored securely and access-restricted?
- Are admin roles and permissions tightly controlled?
- Is there a formal incident response plan in place?
- Are regular vulnerability scans and penetration tests conducted?
- Is there an automated data backup and recovery system?
- Is compliance with GDPR, CCPA, and regional laws documented?
- Is a cyber liability insurance policy in place?
If even three of these items cannot be confidently answered with documented proof, the platform is operating at elevated security risk.
Read more : – UberEats App Marketing Strategy: How to Deliver Growth with Every Order
Security Standards Your White-Label UberEats App Must Meet
To operate legally, safely, and at scale in 2025, your white-label UberEats app must comply with globally recognized security certifications and follow strict technical security protocols. These standards are no longer optional. They are the baseline expectation from regulators, payment companies, restaurant partners, and users.
ESSENTIAL CERTIFICATIONS
These certifications validate that your platform follows globally accepted security and data protection frameworks.
ISO 27001 – Information Security Management System
This is the international gold standard for managing information security. It ensures:
- Structured risk management
- Secure handling of sensitive data
- Continuous improvement of security controls
- Documented security governance across teams
For any large-scale UberEats-type app, ISO 27001 compliance signals serious security maturity.
SOC 2 Type II – Operational Security & Data Handling
SOC 2 Type II verifies that your systems consistently meet five trust principles:
- Security
- Availability
- Processing integrity
- Confidentiality
- Privacy
This certification is especially important for backend infrastructure, cloud hosting, and payment processing environments.
GDPR Compliance – Data Protection in Europe
If your app has users in the EU, GDPR compliance is mandatory. It governs:
- User consent management
- Data retention limits
- Right to access and delete personal information
- Mandatory breach notification timelines
Non-compliance can trigger fines of up to 4 percent of global annual revenue.
HIPAA – Only If Healthcare Data Is Involved
Generally not required for food delivery platforms. However, if your white-label UberEats app integrates prescription delivery, medical meals, or health data, HIPAA may apply.
PCI DSS – Mandatory for Payment Processing
All apps handling card payments must comply with PCI DSS standards. This ensures:
- Secure card data transmission
- Tokenization of payment information
- Regular vulnerability scans
- Restricted access to payment systems
Without PCI DSS compliance, payment gateways can legally block your transactions.
TECHNICAL SECURITY REQUIREMENTS
Beyond certifications, your UberEats-type app must meet strict engineering-level security standards.
End-to-End Encryption
- AES-256 encryption for data at rest
- TLS 1.3 encryption for data in transit
- Secure key management systems
This prevents attackers from reading sensitive data even if infrastructure is compromised.
Secure Authentication Systems
- Two-factor authentication for admin and merchant panels
- OAuth 2.0 for user login
- Secure password hashing with modern algorithms
- Brute-force and bot attack protection
Authentication is the first line of defense against account takeover attacks.
Regular Security Audits
- Annual third-party security audits
- Quarterly internal vulnerability scans
- Codebase security reviews
Audits ensure that hidden vulnerabilities do not quietly accumulate over time.
Penetration Testing
Ethical hackers simulate real-world cyberattacks to uncover:
- API flaws
- Authentication bypasses
- Server misconfigurations
- Business logic vulnerabilities
Penetration testing is essential before every major release.
SSL Certificates and Domain Security
- Extended validation SSL certificates
- HSTS configuration
- Secure DNS management
This protects users from man-in-the-middle attacks and phishing.
Secure API Design
- Token-based authentication
- IP whitelisting
- Rate limiting and throttling
- Input validation and filtering
- Continuous API traffic monitoring
APIs represent the most exploited attack surface in on-demand delivery apps.
SECURITY STANDARDS COMPARISON TABLE
| Security Area | Minimum Acceptable Standard | Enterprise-Grade Standard |
|---|---|---|
| Data Encryption | TLS + basic database encryption | End-to-end AES-256 + zero-trust keys |
| Authentication | Password-based login | 2FA + OAuth + device verification |
| Payment Security | Basic gateway integration | Full PCI DSS certified processing |
| API Protection | Token authentication | Token + throttling + real-time monitoring |
| Server Security | Firewall + antivirus | Zero-trust architecture + IDS/IPS |
| Audits | Annual internal review | Continuous automated + external audits |
| Compliance | Basic legal compliance | ISO 27001 + SOC 2 + GDPR certified |
| Incident Response | Manual escalation | Automated detection + rapid containment |
This table highlights the gap between platforms that merely “function” and those that operate with true enterprise-grade security.
Red Flags: How to Spot Unsafe White-Label Providers
Choosing the wrong white-label UberEats app provider can expose your business to massive legal, financial, and reputational risks. Many security failures do not happen because founders ignore security—but because they trust the wrong vendor. Knowing the warning signs in advance can save you from irreversible damage.
WARNING SIGNS OF AN UNSAFE WHITE-LABEL PROVIDER
These red flags indicate that security is being treated as an afterthought rather than a foundation.
No Security Documentation
If a provider cannot clearly share:
- Security architecture overview
- Data handling policies
- Breach response procedures
It usually means no formal security framework exists.
Unrealistically Cheap Pricing Without Explanation
Extremely low pricing often indicates:
- No third-party audits
- Shared insecure servers
- Minimal penetration testing
- Poor-quality open-source reuse without hardening
Security engineering requires real investment. Sustainable pricing should always reflect that.
No Compliance Certifications
If the provider cannot demonstrate:
- GDPR compliance
- PCI DSS adherence
- ISO 27001 or SOC 2 alignment
Your business becomes legally exposed from day one of launch.
Outdated Technology Stack
Old frameworks and unpatched libraries introduce:
- Known exploit vulnerabilities
- Poor performance under attack
- Compatibility issues with modern security tools
Security cannot be built on obsolete code.
Poor Code Quality
Indicators include:
- No modular architecture
- Hardcoded credentials
- Weak password handling
- No environment separation (development, testing, production)
Low code quality directly translates into high breach probability.
No Security Update Policy
If a provider does not release:
- Regular patches
- Emergency vulnerability fixes
- Dependency updates
Your platform will slowly become more vulnerable with every passing month.
Lack of Data Backup Systems
Absence of:
- Automated daily backups
- Offsite backup storage
- Disaster recovery planning
Means a single ransomware attack can permanently wipe your business data.
No Insurance Coverage
Reputable security-first providers carry:
- Cyber liability insurance
- Professional indemnity coverage
This protects both the provider and your business during major security incidents.
EVALUATION CHECKLIST FOR SAFE PROVIDER SELECTION
Before finalizing any white-label UberEats app provider, conduct structured due diligence using this checklist.
Questions to Ask Providers
- Do you follow ISO 27001 security management practices?
- Is your platform PCI DSS compliant for payments?
- How is user data encrypted at rest and in transit?
- How often do you perform penetration testing?
- What is your average security patch release cycle?
- Who is responsible for security updates after launch?
- What is your formal incident response time?
- Do you offer cyber liability insurance coverage?
Documents to Request
- Security audit reports
- Penetration testing summaries
- Data protection policy
- GDPR compliance statement
- PCI DSS attestation of compliance
- Backup and disaster recovery plan
A legitimate provider will never hesitate to share security credentials.
Testing Procedures
- Request demo access to admin panels
- Validate multi-factor authentication
- Review API access control methods
- Test payment flows under sandbox mode
- Verify encrypted communication using security tools
Due Diligence Steps
- Cross-check client references
- Review public breach history
- Ask for compliance certificates
- Involve a third-party security consultant if needed
- Conduct your own vulnerability assessment before production launch
Skipping due diligence is one of the most expensive mistakes founders make in the food delivery space.
Read more : – Top UberEats App Features You Should Know
Best Practices for Secure White-Label UberEats App Implementation
A secure white-label UberEats app is not achieved at the moment of deployment. It is built through disciplined preparation before launch and sustained through continuous monitoring after launch. Security must be embedded into both operational workflows and technical infrastructure from day one.
PRE-LAUNCH SECURITY BEST PRACTICES
These steps must be completed before your app goes live in any market.
Security Audit Process
- Conduct a full infrastructure and application-level security audit
- Review codebase for known vulnerabilities
- Validate encryption standards and key management
- Verify data flow between app, servers, and third-party services
Independent third-party audits provide the highest level of validation.
Code Review Requirements
- Manual review of authentication logic
- Secure handling of API tokens
- Validation of database query protection
- Session management and timeout controls
Code review prevents logic-level vulnerabilities that automated tools may miss.
Infrastructure Hardening
- Harden cloud servers using zero-trust access controls
- Restrict administrative access using role-based permissions
- Deploy intrusion detection and prevention systems
- Segment databases and microservices
Infrastructure is the backbone of platform security.
Compliance Verification
- Confirm GDPR and regional data protection alignment
- Verify PCI DSS certification for payment systems
- Ensure privacy policy and terms of service reflect actual data handling practices
Legal compliance must match technical implementation.
Staff Training Programs
- Security awareness training for support and operations teams
- Phishing attack simulations
- Access control and data handling guidelines
Human error remains one of the leading causes of breaches.
POST-LAUNCH SECURITY MONITORING
Once live, security becomes a continuous discipline rather than a one-time task.
Continuous Security Monitoring
- Real-time vulnerability detection
- Automated alerting for suspicious activity
- Traffic anomaly monitoring
- API abuse detection
Active monitoring dramatically reduces breach response time.
Regular Updates and Patches
- Scheduled monthly security updates
- Emergency patch deployment for critical vulnerabilities
- Continuous dependency updates
Unpatched systems are the most exploited systems in production.
Incident Response Planning
- Defined breach detection protocols
- Automated alert escalation paths
- Dedicated response teams
- Regulatory reporting workflows
- User notification procedures
A rehearsed response plan reduces both damage and legal liability.
User Data Management
- Enforced data retention limits
- Automated user data deletion requests
- Secure anonymization of historical analytics data
Data minimization directly reduces long-term breach exposure.
Backup and Recovery Systems
- Daily encrypted database backups
- Automated backup integrity verification
- Geographic redundancy across cloud regions
- Disaster recovery simulation testing
Backups are the only reliable defense against ransomware and data corruption.
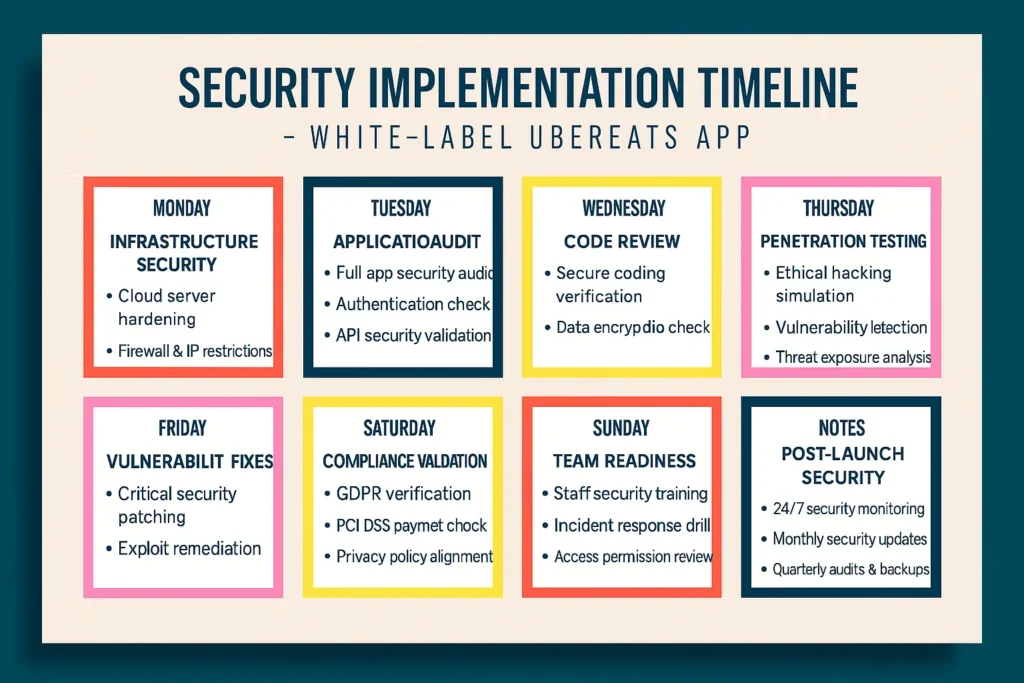
SECURITY IMPLEMENTATION TIMELINE
Legal & Compliance Considerations
Security in a white-label UberEats app is not only a technical responsibility but also a legal obligation. Regulatory authorities across the world now treat data protection and digital transaction security as enforceable business laws. Ignoring compliance can result in platform shutdowns, heavy financial penalties, and permanent brand damage.
REGULATORY REQUIREMENTS
Every food delivery platform operates under multiple overlapping legal frameworks depending on the regions it serves.
Data Protection Laws by Region
- European Union – GDPR
Requires lawful data processing, explicit user consent, right to erasure, breach notification within 72 hours, and strict data minimization. - United States – CCPA and CPRA
Grants users rights over personal data access, deletion, and opting out of data sharing. - India – Digital Personal Data Protection Act (DPDP)
Governs consent-based collection, secure storage, breach reporting, and cross-border data transfers. - Middle East and APAC
Increasing adoption of GDPR-style privacy regulations with strict data localization rules in certain countries.
Your white-label UberEats app must dynamically adapt its compliance framework based on the countries it operates in.
Industry-Specific Regulations
- Payment processing laws
- Electronic transaction compliance
- Consumer protection laws
- Digital advertising regulations
- Food delivery service licensing requirements
Non-compliance in any one area can block payment processing or app store approvals.
User Consent Management
- Explicit opt-in for data collection
- Cookie tracking disclosure
- Location and camera permission transparency
- Marketing communication consent controls
Consent must be:
- Freely given
- Documented
- Revocable at any time
Privacy Policy Requirements
Your app’s privacy policy must clearly define:
- What data is collected
- Why it is collected
- How long it is stored
- With whom it is shared
- How users can request deletion
Mismatch between legal policy and technical operation is a common source of lawsuits.
Terms of Service Essentials
- User responsibilities
- Platform liability limitations
- Dispute resolution mechanism
- Payment and refund policies
- Jurisdictional authority
Clear terms reduce legal ambiguity during conflicts.
LIABILITY PROTECTION
Even with the strongest security infrastructure, residual risk remains. Liability protection safeguards your business against catastrophic losses.
Insurance Requirements
- Cyber liability insurance
- Data breach coverage
- Technology errors and omissions insurance
These policies cover:
- Regulatory investigation costs
- Customer compensation
- Forensic audits
- Legal defense expenses
Legal Disclaimers
- Platform usage limitations
- Data processing ownership
- Third-party integration responsibility clauses
Disclaimers must be legally vetted and region-specific.
User Agreements
- Compliance acknowledgment
- Data consent confirmation
- Dispute arbitration clauses
- Digital transaction responsibility definitions
Incident Reporting Protocols
- Mandatory reporting timelines
- Regulatory authority notification workflows
- Affected user communication procedures
Delayed reporting often increases penalties more than the breach itself.
Regulatory Compliance Monitoring
- Continuous legal updates tracking
- Periodic policy reviews
- Regional compliance audits
- External legal advisory retainers
Laws evolve faster than most startups anticipate. Continuous monitoring prevents accidental violations.
COMPLIANCE CHECKLIST BY REGION
Use this high-level checklist to validate minimum legal readiness:
- GDPR consent management implemented
- Data deletion and portability tools available
- PCI DSS compliance documented
- Local digital data protection laws validated
- Cyber liability insurance active
- Privacy policy legally reviewed
- Terms of service regionally adapted
- Breach response and reporting workflow defined
If any of these items are missing, your white-label UberEats app operates under legal and financial exposure.
Why Miracuves White-Label UberEats App Is Your Safest Choice
Security is not an add-on at Miracuves. It is embedded into the architecture, development process, infrastructure management, and long-term platform support. While many providers focus purely on speed and cost, Miracuves follows a security-first engineering model designed specifically for high-risk platforms like food delivery and on-demand services.
Read more : – UberEats Revenue Model: How UberEats Makes Money in 2025
MIRACUVES SECURITY ADVANTAGES
Enterprise-Grade Security Architecture
The Miracuves white-label UberEats app is built on a hardened, enterprise-grade security framework that includes:
- Multi-layer application security
- Zero-trust server access control
- Segmented databases for customers, drivers, and merchants
- Isolated production environments for each client
This design ensures that even in the rare event of a breach attempt, damage is compartmentalized and contained.
Regular Security Audits and Certifications
Miracuves follows a structured audit and compliance cycle that includes:
- Periodic internal vulnerability assessments
- Third-party penetration testing
- Continuous compliance validation for regulatory standards
This ensures that evolving threat vectors are addressed proactively rather than reactively.
GDPR and CCPA Compliance by Default
Every Miracuves white-label UberEats app is deployed with:
- Built-in user consent management
- Automated data deletion workflows
- Structured data retention policies
- Secure privacy policy enforcement
This makes global expansion smoother and legally safer from day one.
24/7 Security Monitoring
Miracuves platforms operate under continuous monitoring for:
- Unauthorized access attempts
- API abuse and bot traffic
- Payment fraud activities
- Infrastructure anomalies
Real-time alerts ensure immediate response to suspicious activity.
Encrypted Data Transmission
All sensitive data is protected with:
- End-to-end encryption for data in transit
- Advanced encryption for data at rest
- Secure tokenization for sensitive identifiers
This prevents data exposure even if infrastructure is compromised at any layer.
Secure Payment Processing
The Miracuves UberEats-type app integrates only with PCI DSS-compliant payment gateways and follows strict payment security policies including:
- Card data tokenization
- Secure transaction routing
- Fraud detection filters
- Chargeback risk management
Regular Security Updates
Miracuves releases:
- Monthly security updates
- Emergency vulnerability patches
- Continuous library and framework upgrades
This keeps the platform protected against newly discovered exploits.
Insurance Coverage Included
Miracuves maintains:
- Cyber liability insurance
- Professional indemnity coverage
This protects both Miracuves and its clients during major cyber or compliance incidents.
Conclusion
Do not compromise on security. Miracuves white-label UberEats app solutions come with enterprise-grade security built in from day one. With 600+ successful projects and a zero major breach record, Miracuves is trusted by businesses worldwide for safe, compliant, and scalable platforms. Get your free security assessment today and validate your platform before you launch.
A white-label UberEats app can be just as secure as a fully custom-built platform—if security is treated as a foundation and not a feature. In 2025, user trust, regulatory compliance, and long-term business survival depend directly on how seriously you approach data protection, payment security, and continuous monitoring. The right technology partner does not just help you launch faster—they protect your business reputation every single day.
FAQs
1. How secure is a white-label UberEats app compared to custom development?
A properly audited white-label UberEats app is often more secure than many custom apps because it benefits from continuous testing across multiple deployments.
2. What happens if there is a security breach?
A formal incident response process is triggered, affected systems are isolated, regulators are notified as required, and users are informed under legal timelines.
3. Who is responsible for security updates?
The white-label app provider is responsible for core platform security updates, while the business owner manages operational access control.
4. How is user data protected in a white-label UberEats app?
Through end-to-end encryption, secure APIs, role-based access control, and strict data retention policies.
5. Which compliance certifications should I look for?
At minimum: GDPR, PCI DSS, and alignment with ISO 27001 or SOC 2 standards.
6. Can a white-label UberEats app meet enterprise security standards?
Yes, when built on secure cloud infrastructure with continuous monitoring and third-party audits.
7. How often should security audits be conducted?
Internal scans should be continuous, while full penetration testing should be conducted at least once per year.
8. What is included in the Miracuves security package?
Encrypted data handling, PCI-compliant payments, GDPR-ready workflows, continuous monitoring, and regular security updates.
9. How is security handled across different countries?
Data protection rules are configured dynamically based on regional laws such as GDPR, CCPA, and DPDP.
10. What type of insurance is required for app security?
Cyber liability insurance and technology errors and omissions coverage are strongly recommended.
Related Articles: